Implicit Flow is an OAuth 2.0 authorization method designed for client-side applications that require tokens directly without server-side exchanges. It enables faster authentication by returning access tokens immediately through the browser, enhancing user experience in single-page apps. Explore this article to understand how Implicit Flow can optimize your application's authentication process.
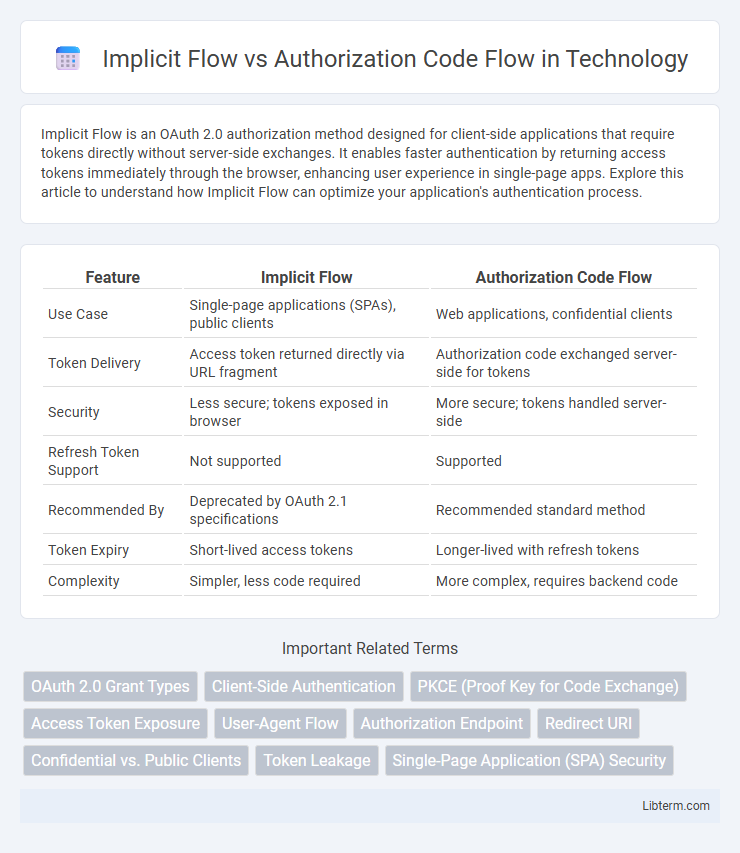
Table of Comparison
| Feature | Implicit Flow | Authorization Code Flow |
|---|---|---|
| Use Case | Single-page applications (SPAs), public clients | Web applications, confidential clients |
| Token Delivery | Access token returned directly via URL fragment | Authorization code exchanged server-side for tokens |
| Security | Less secure; tokens exposed in browser | More secure; tokens handled server-side |
| Refresh Token Support | Not supported | Supported |
| Recommended By | Deprecated by OAuth 2.1 specifications | Recommended standard method |
| Token Expiry | Short-lived access tokens | Longer-lived with refresh tokens |
| Complexity | Simpler, less code required | More complex, requires backend code |
Understanding OAuth 2.0 Flows
OAuth 2.0 flows optimize secure access delegation between clients and servers by defining distinct authorization methods. Implicit Flow enables client-side single-page applications to obtain access tokens directly from the authorization endpoint, minimizing server interaction but exposing tokens to browser-based risks. Authorization Code Flow involves an additional step that exchanges an authorization code for tokens via a backend server, enhancing security by keeping tokens off the user-agent and supporting refresh tokens for long-lived sessions.
What is Implicit Flow?
Implicit Flow is an OAuth 2.0 authentication process designed for public clients, such as single-page applications, where tokens are directly returned in the URL fragment without an intermediate authorization code. It eliminates the need for a client secret and reduces round-trips by providing access tokens immediately, but it exposes tokens in the browser, impacting security. Implicit Flow is less secure compared to Authorization Code Flow and is being replaced by Authorization Code Flow with PKCE for improved security in modern applications.
What is Authorization Code Flow?
Authorization Code Flow is an OAuth 2.0 authentication mechanism designed for securely obtaining access tokens by exchanging an authorization code received from the authorization server. It involves redirecting the user to authenticate, then receiving an authorization code that the client application exchanges for an access token and optionally a refresh token. This flow enhances security by keeping tokens off the front channel and is especially suitable for server-side or confidential applications.
Key Differences Between Implicit and Authorization Code Flows
Implicit Flow transmits tokens directly in the URL fragment, making it faster but less secure due to exposure in the browser, whereas Authorization Code Flow exchanges an authorization code for tokens on the backend, enhancing security by keeping tokens away from the user agent. Implicit Flow is suited for single-page applications without a backend, while Authorization Code Flow is preferred for server-side applications requiring secure token handling and refresh capabilities. OAuth 2.1 deprecates Implicit Flow in favor of Authorization Code Flow with PKCE for improved security and mitigation of token interception risks.
Security Considerations in Both Flows
Authorization Code Flow enhances security by exchanging an authorization code for tokens on the backend, reducing exposure of tokens to the browser and mitigating risks like token interception or leakage. Implicit Flow directly issues tokens to the browser, increasing vulnerability to token theft through browser history, malicious scripts, or network attacks. Modern best practices recommend Authorization Code Flow with Proof Key for Code Exchange (PKCE) to provide robust protection against authorization code interception and replay attacks, making it the preferred approach for both confidential and public clients.
Use Cases for Implicit Flow
Implicit Flow is ideal for single-page applications (SPAs) and public clients where maintaining client secrecy is challenging, enabling direct token issuance without backend code exchange. It suits scenarios requiring immediate access tokens for browser-based JavaScript applications without a server component. This flow reduces latency by eliminating the authorization code exchange step, enhancing user experience in client-only environments.
Use Cases for Authorization Code Flow
Authorization Code Flow is ideal for web and mobile applications requiring secure, reliable user authentication with server-side components that can safely store client secrets. It supports obtaining both access and refresh tokens, enabling long-lived sessions and seamless token renewal without user interaction. This flow is commonly used in scenarios involving sensitive data access, such as banking apps, enterprise software, and services requiring strong compliance with security standards.
Why the Industry Prefers Authorization Code Flow
Authorization Code Flow is preferred in the industry for its enhanced security, as it exchanges an authorization code for tokens on the backend, reducing exposure of access tokens to public clients or browsers. This flow supports the use of refresh tokens, enabling long-lived sessions without re-authentication, which is critical for maintaining secure user experiences. Implicit Flow, by contrast, exposes tokens directly to the user-agent, increasing vulnerability to interception and token leakage, leading to its decline in favor.
Migrating from Implicit Flow to Authorization Code Flow
Migrating from Implicit Flow to Authorization Code Flow enhances security by exchanging authorization codes for tokens via a back-channel, reducing exposure to access tokens in the browser. Authorization Code Flow, combined with PKCE (Proof Key for Code Exchange), mitigates risks of token interception and replay attacks commonly associated with Implicit Flow. Organizations should update client applications to support server-side token exchanges and implement PKCE to ensure secure and efficient OAuth 2.0 authentication in modern web environments.
Best Practices for Secure OAuth 2.0 Implementation
Authorization Code Flow remains the best practice for secure OAuth 2.0 implementation due to its use of server-side token exchanges, reducing exposure of access tokens to user agents. Implicit Flow, while simpler for browser-based applications, is less secure because access tokens are directly returned in the URI, increasing risk of token leakage. Security experts recommend leveraging Authorization Code Flow with Proof Key for Code Exchange (PKCE) to enhance protection against interception attacks in public clients.
Implicit Flow Infographic
 libterm.com
libterm.com