A hash function transforms input data into a fixed-size string of characters, typically a sequence of numbers and letters, which represents the original content uniquely. Your data's integrity and security can be ensured by using strong cryptographic hash functions, crucial in various applications like password storage, data verification, and blockchain technology. Explore the rest of the article to understand how hash functions enhance digital security and data management.
Table of Comparison
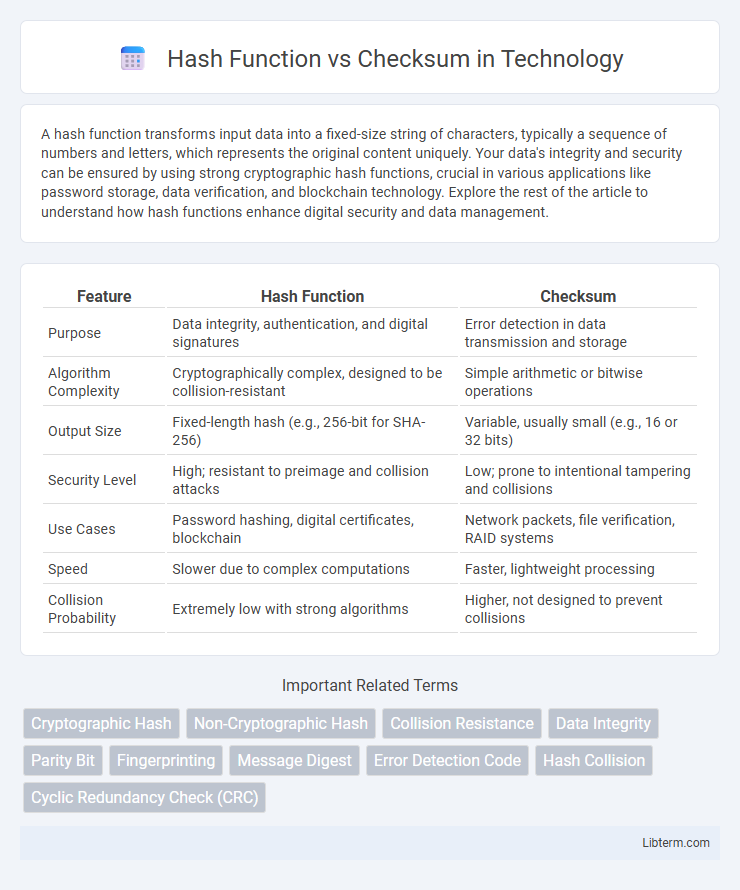
| Feature | Hash Function | Checksum |
|---|---|---|
| Purpose | Data integrity, authentication, and digital signatures | Error detection in data transmission and storage |
| Algorithm Complexity | Cryptographically complex, designed to be collision-resistant | Simple arithmetic or bitwise operations |
| Output Size | Fixed-length hash (e.g., 256-bit for SHA-256) | Variable, usually small (e.g., 16 or 32 bits) |
| Security Level | High; resistant to preimage and collision attacks | Low; prone to intentional tampering and collisions |
| Use Cases | Password hashing, digital certificates, blockchain | Network packets, file verification, RAID systems |
| Speed | Slower due to complex computations | Faster, lightweight processing |
| Collision Probability | Extremely low with strong algorithms | Higher, not designed to prevent collisions |
Introduction to Hash Functions and Checksums
Hash functions generate fixed-size outputs from variable-length input data, ensuring data integrity and enabling efficient data retrieval through unique identifiers called hash values. Checksums are simple error-detection codes computed by summing data values, primarily used to identify accidental data corruption during transmission or storage. Both techniques play crucial roles in data verification but differ in complexity, with cryptographic hash functions providing stronger security guarantees compared to basic checksum algorithms.
What Is a Hash Function?
A hash function converts input data into a fixed-size string of characters, typically a sequence of numbers and letters, which represents the original data uniquely. It is widely used in cryptography, data retrieval, and integrity verification due to its ability to efficiently map large amounts of data to a shorter, fixed-length hash code. Unlike checksums, hash functions provide stronger collision resistance, making them essential for secure data authentication and digital signatures.
What Is a Checksum?
A checksum is a value calculated from a data set to detect errors during transmission or storage by comparing the original and received data. Unlike cryptographic hash functions designed for security and uniqueness, checksums primarily ensure data integrity with simple algorithms like CRC or Adler-32. Commonly used in network communications and file storage, checksums quickly verify that data remains unchanged without providing strong protection against intentional tampering.
Key Differences Between Hash Functions and Checksums
Hash functions generate fixed-size, unique outputs called hash values from input data, ensuring data integrity and enabling secure verification through complex algorithms like SHA-256. Checksums produce simpler numeric values derived from data by summing byte values or performing basic arithmetic, primarily used to detect accidental errors in data transmission or storage. The key differences lie in their complexity, purpose, and collision resistance, where hash functions offer higher security and uniqueness, while checksums prioritize speed and error detection.
Use Cases of Hash Functions
Hash functions are primarily used in cybersecurity for data integrity verification, password hashing, and digital signatures, ensuring secure authentication and non-repudiation. They enable efficient indexing and retrieval in databases, as well as deduplication in storage systems by generating unique fixed-size hash values for variable-length inputs. In blockchain technology, hash functions secure transaction data, linking blocks immutably while facilitating consensus mechanisms and proof-of-work algorithms.
Common Applications of Checksums
Checksums are widely used in network communications and data storage systems to detect accidental errors by verifying data integrity. Common applications include verifying file downloads, error detection in network protocols like TCP/IP, and ensuring data consistency in RAID storage configurations. Hash functions differ by providing cryptographic security for authenticity and non-repudiation, whereas checksums primarily focus on simple error detection.
Security Considerations: Hash Functions vs Checksums
Hash functions provide stronger security than checksums by producing unique, fixed-size outputs that resist collisions and tampering, making them ideal for data integrity verification and cryptographic applications. Checksums are primarily designed for error detection and are vulnerable to intentional manipulation, lacking the complexity to prevent malicious alterations. Reliable security implementations favor cryptographic hash functions to ensure data authenticity and prevent unauthorized modifications.
Performance and Efficiency Comparison
Hash functions typically provide faster computation speeds and better collision resistance than checksums, making them more efficient for data integrity verification in large-scale applications. Checksums, while simpler and requiring less computational overhead, are less robust against intentional tampering and are best suited for quick error detection in limited data sets. Performance benchmarks indicate that hash functions like SHA-256 may have higher CPU usage but deliver superior security and reliability, whereas checksums like CRC32 offer minimal latency and lower resource consumption.
Popular Algorithms: Hash Functions and Checksums
Popular hash functions include MD5, SHA-1, and SHA-256, known for producing fixed-size digests used in data integrity and authentication. Common checksum algorithms like CRC32 and Adler-32 enable rapid error detection in network transmissions and file storage. Hash functions offer cryptographic security features, whereas checksums prioritize computational efficiency for error-checking purposes.
Choosing Between Hash Function and Checksum
Choosing between a hash function and a checksum depends on the level of data integrity and security required; hash functions provide stronger cryptographic guarantees and resistance to collisions, making them ideal for verifying data authenticity in security-sensitive applications. Checksums are simpler and faster, suitable for detecting accidental errors in data transmission or storage without the need for cryptographic strength. For critical security contexts, hash functions like SHA-256 offer robust protection, while checksums like CRC32 serve well for error-checking in less demanding environments.
Hash Function Infographic
 libterm.com
libterm.com