Device Authorization Flow simplifies user authentication on devices with limited input capabilities by allowing users to authorize the device through another trusted device. This secure process enhances user experience while maintaining strong security measures by separating the device verification from the direct login input. Explore the rest of this article to understand how Device Authorization Flow can optimize your multi-device access management.
Table of Comparison
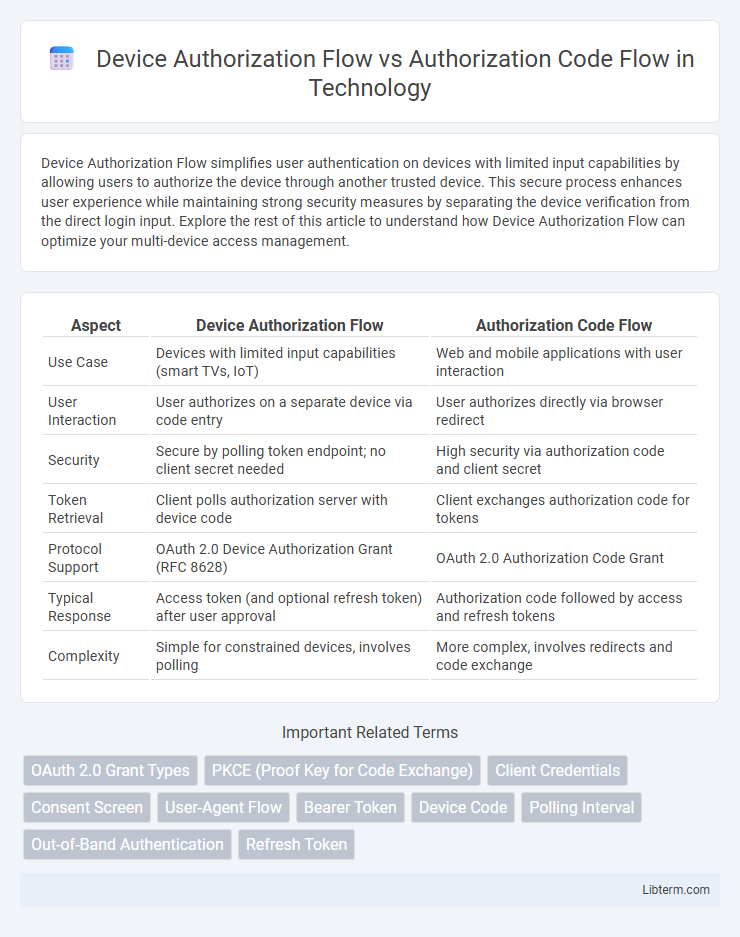
| Aspect | Device Authorization Flow | Authorization Code Flow |
|---|---|---|
| Use Case | Devices with limited input capabilities (smart TVs, IoT) | Web and mobile applications with user interaction |
| User Interaction | User authorizes on a separate device via code entry | User authorizes directly via browser redirect |
| Security | Secure by polling token endpoint; no client secret needed | High security via authorization code and client secret |
| Token Retrieval | Client polls authorization server with device code | Client exchanges authorization code for tokens |
| Protocol Support | OAuth 2.0 Device Authorization Grant (RFC 8628) | OAuth 2.0 Authorization Code Grant |
| Typical Response | Access token (and optional refresh token) after user approval | Authorization code followed by access and refresh tokens |
| Complexity | Simple for constrained devices, involves polling | More complex, involves redirects and code exchange |
Introduction to OAuth 2.0 Flows
OAuth 2.0 flows facilitate secure delegated access by enabling client applications to obtain access tokens on behalf of users. Device Authorization Flow is designed for devices with limited input capabilities, allowing users to authorize devices via an external browser, whereas Authorization Code Flow is optimized for confidential clients with a backend, involving a direct redirection and exchange of an authorization code for tokens. Both flows maintain user consent and security but serve different use cases based on device capabilities and user interaction models.
What is Device Authorization Flow?
Device Authorization Flow is an OAuth 2.0 protocol designed for input-constrained devices like smart TVs and IoT gadgets, enabling users to grant access without typing credentials directly on the device. It involves the device displaying a user code and verification URL for users to authenticate on a secondary device with full input capabilities. This flow enhances security and usability by decoupling device authentication from user interaction on limited-input hardware.
What is Authorization Code Flow?
Authorization Code Flow is an OAuth 2.0 authentication method designed for web and mobile applications to securely obtain access tokens by exchanging an authorization code received after user consent. This flow enhances security by keeping tokens off the user agent and requiring a client secret during the token exchange, reducing the risk of token interception. It is widely used in scenarios where the client application can maintain confidentiality and handles sensitive user authentication tasks.
Key Differences Between Device and Authorization Code Flows
The Device Authorization Flow enables user authentication on devices with limited input capabilities by allowing them to enter a code on a separate device, whereas the Authorization Code Flow requires a direct user interaction with a browser to exchange an authorization code for tokens. Device Flow is optimized for TVs, gaming consoles, and IoT devices, leveraging a user code and verification URI, while Authorization Code Flow is typically used in web and mobile applications with a redirect URI and supports strong client authentication. Key differences include the presence of user interaction with the client, the method of token acquisition, and the types of devices each flow supports.
Security Considerations: Device vs Authorization Code
Device Authorization Flow prioritizes user convenience on limited-input devices but requires careful handling of refresh tokens to prevent unauthorized access. Authorization Code Flow enhances security by exchanging codes directly between client and authorization server, minimizing token exposure. Both flows rely on secure storage and proper validation, but Authorization Code Flow typically offers stronger protection against interception and replay attacks.
User Experience Comparison
Device Authorization Flow offers a streamlined user experience by allowing users to authenticate on a separate device, eliminating the need for entering credentials directly on the input-constrained device. Authorization Code Flow requires users to interact with a browser for login and consent, which may introduce friction on devices with limited input capabilities. The Device Authorization Flow enhances convenience and accessibility, particularly for smart TVs and IoT devices, while Authorization Code Flow remains preferred for web applications emphasizing security and seamless redirect handling.
Suitable Use Cases for Device Authorization Flow
Device Authorization Flow is ideal for input-constrained devices such as smart TVs, gaming consoles, and IoT devices where direct user interaction is limited or impractical. This flow enables users to authorize devices by using a secondary device like a smartphone or computer, improving security and user experience without entering credentials directly on the constrained device. It is specifically designed to handle scenarios where entering complex input or redirect URLs is not feasible, unlike Authorization Code Flow which suits web and mobile applications with rich user interfaces.
Suitable Use Cases for Authorization Code Flow
Authorization Code Flow is ideal for web applications and mobile apps where the client can securely store client secrets and interact with the authorization server via a backend. This flow ensures enhanced security by exchanging an authorization code for tokens on a secure server, preventing exposure of tokens to the user agent. It suits scenarios requiring user authentication with sensitive data access and strong protection against token interception, such as banking apps and enterprise-grade services.
Implementation Challenges and Best Practices
Device Authorization Flow implementation challenges often include handling limited input capabilities and ensuring secure user code verification, requiring robust back-end validation and clear user instructions. Authorization Code Flow demands careful management of redirect URIs, secure storage of authorization codes, and mitigation of CSRF attacks through state parameters. Best practices involve using PKCE (Proof Key for Code Exchange) for enhanced security, implementing token expiration and refresh strategies, and thorough logging for troubleshooting both flows.
Which OAuth Flow Should You Choose?
Device Authorization Flow is ideal for devices with limited input capabilities, such as smart TVs or IoT devices, allowing users to authenticate using a secondary device. Authorization Code Flow suits web and mobile applications where secure server-side exchanges can be performed, ensuring tokens are not exposed to the user-agent. Choose Device Authorization Flow for seamless user experience on constrained devices and Authorization Code Flow for traditional applications requiring robust security and token confidentiality.
Device Authorization Flow Infographic
 libterm.com
libterm.com