Firewalling is a crucial cybersecurity measure that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It serves as a barrier between trusted internal networks and untrusted external sources, preventing unauthorized access and potential threats. Explore the rest of the article to understand how firewalling can protect your digital assets effectively.
Table of Comparison
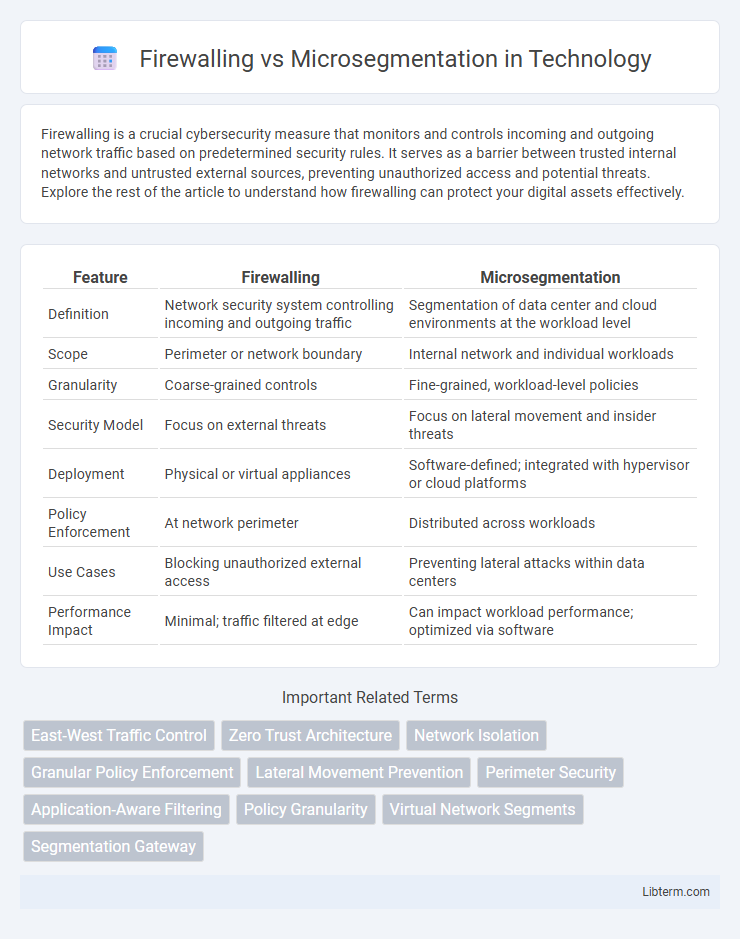
| Feature | Firewalling | Microsegmentation |
|---|---|---|
| Definition | Network security system controlling incoming and outgoing traffic | Segmentation of data center and cloud environments at the workload level |
| Scope | Perimeter or network boundary | Internal network and individual workloads |
| Granularity | Coarse-grained controls | Fine-grained, workload-level policies |
| Security Model | Focus on external threats | Focus on lateral movement and insider threats |
| Deployment | Physical or virtual appliances | Software-defined; integrated with hypervisor or cloud platforms |
| Policy Enforcement | At network perimeter | Distributed across workloads |
| Use Cases | Blocking unauthorized external access | Preventing lateral attacks within data centers |
| Performance Impact | Minimal; traffic filtered at edge | Can impact workload performance; optimized via software |
Introduction to Network Security Approaches
Firewalling establishes a perimeter defense by filtering traffic between trusted and untrusted networks, enforcing security policies based on predefined rules. Microsegmentation enhances network security by dividing the network into granular segments, applying tailored access controls to minimize lateral movement of threats within the environment. Combining these approaches optimizes network protection by addressing both external threats and internal vulnerabilities through layered security controls.
What is Firewalling?
Firewalling is a network security mechanism designed to monitor and control incoming and outgoing traffic based on predetermined security rules, effectively creating a barrier between trusted internal networks and untrusted external networks. It operates at various layers, including packet filtering, stateful inspection, and application layer filtering, to prevent unauthorized access and cyber threats. Firewalls can be hardware-based, software-based, or cloud-managed, providing essential protection by blocking malicious traffic and enforcing security policies across network boundaries.
What is Microsegmentation?
Microsegmentation is a network security technique that divides a data center or cloud environment into secure segments down to the workload level, enabling granular control over east-west traffic. Unlike traditional firewalling, which filters traffic between broad network zones, microsegmentation enforces policies directly within the network fabric, minimizing lateral movement of threats. This approach enhances security by isolating applications and workloads, reducing attack surfaces, and improving compliance with regulatory standards.
Key Differences Between Firewalling and Microsegmentation
Firewalling primarily controls traffic between different network segments or between an internal network and external networks based on predefined security rules, focusing on perimeter defense. Microsegmentation, however, provides granular, application-level security within a data center or cloud environment by isolating workloads to limit lateral movement of threats. Unlike traditional firewalls that operate at the network perimeter, microsegmentation enforces policies closer to the workload, enhancing security posture against sophisticated cyber threats.
Advantages of Traditional Firewalling
Traditional firewalling offers robust perimeter defense by filtering traffic based on predefined security rules, effectively blocking unauthorized access and preventing external threats. It provides centralized control and simplicity in managing network security policies across multiple devices and endpoints. This approach reduces the attack surface and is well-suited for organizations requiring straightforward, scalable protection against common cyberattacks.
Benefits of Microsegmentation in Modern Networks
Microsegmentation enhances network security by creating granular, isolated segments within a data center or cloud environment, reducing the attack surface and limiting lateral movement of threats. Unlike traditional firewalling, microsegmentation applies context-aware policies at the workload level, enabling precise control over east-west traffic between applications and services. This approach improves compliance, minimizes the risk of data breaches, and supports dynamic, scalable environments characteristic of modern networks.
Use Cases: When to Choose Firewalling
Firewalling is ideal for perimeter security by controlling inbound and outbound traffic between trusted internal networks and untrusted external environments, making it suitable for protecting enterprise networks from external threats. It is effective in scenarios requiring broad access control policies, such as blocking malicious IP addresses or restricting ports and protocols across the entire network. Organizations should choose firewalling when the primary goal is to enforce network boundaries and prevent unauthorized access at entry and exit points.
Use Cases: When to Implement Microsegmentation
Microsegmentation is ideal for environments requiring granular security controls, such as data centers, cloud infrastructures, and zero trust architectures where lateral movement of threats must be minimized. Unlike traditional firewalling that protects network perimeters, microsegmentation isolates workloads and applications within a network to enforce fine-grained policies based on identity, context, and risk. Implement microsegmentation when comprehensive visibility and control within internal network segments are critical to prevent internal threats or comply with regulatory standards like PCI DSS and HIPAA.
Integration: Combining Firewalling and Microsegmentation
Integrating firewalling and microsegmentation enhances network security by providing granular control over internal and perimeter traffic, reducing attack surfaces. Firewalling enforces perimeter defenses, while microsegmentation applies policy controls at the workload or application layer, enabling dynamic and context-aware security. This combination supports continuous monitoring, threat detection, and automated responses, ensuring comprehensive protection across hybrid cloud environments.
Future Trends in Network Security Solutions
Future trends in network security solutions highlight a shift from traditional firewalling towards advanced microsegmentation techniques, offering granular control over east-west traffic within data centers and cloud environments. Microsegmentation leverages machine learning and behavioral analytics to dynamically enforce security policies at the workload level, significantly reducing attack surfaces and lateral movement of threats. Integration with zero trust architectures and automation platforms further enhances microsegmentation's capability to provide adaptive, context-aware protection in increasingly complex hybrid and multi-cloud networks.
Firewalling Infographic
 libterm.com
libterm.com