Penetration testing identifies vulnerabilities in your network, applications, and systems by simulating real cyberattacks to expose weaknesses before malicious hackers can exploit them. This proactive approach enhances your security posture and ensures compliance with industry standards. Discover how effective penetration testing safeguards your digital assets by reading the full article.
Table of Comparison
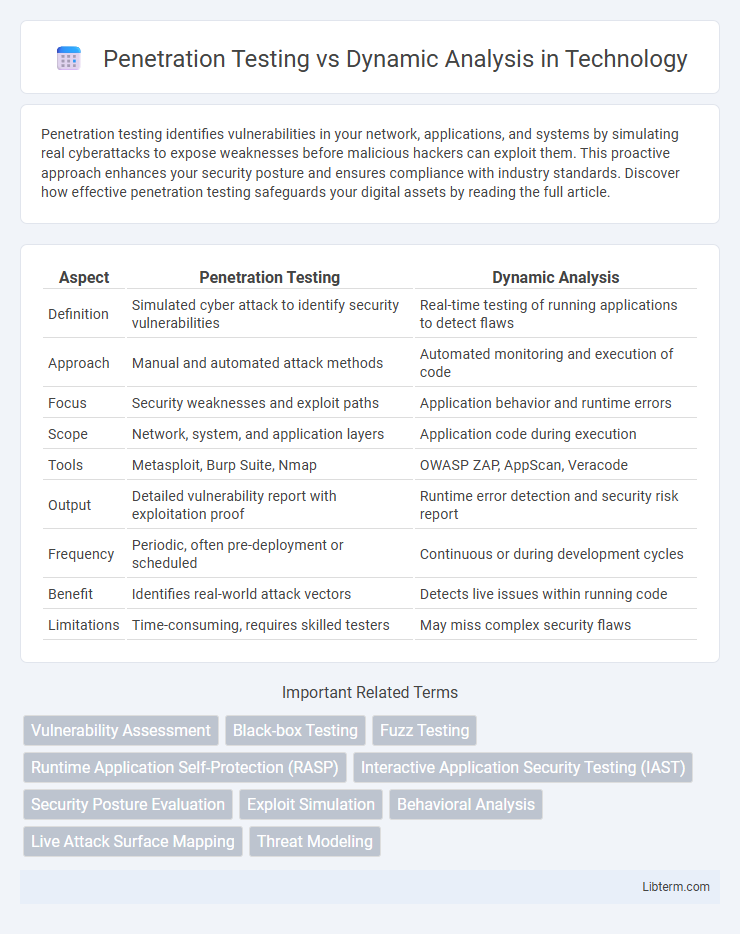
| Aspect | Penetration Testing | Dynamic Analysis |
|---|---|---|
| Definition | Simulated cyber attack to identify security vulnerabilities | Real-time testing of running applications to detect flaws |
| Approach | Manual and automated attack methods | Automated monitoring and execution of code |
| Focus | Security weaknesses and exploit paths | Application behavior and runtime errors |
| Scope | Network, system, and application layers | Application code during execution |
| Tools | Metasploit, Burp Suite, Nmap | OWASP ZAP, AppScan, Veracode |
| Output | Detailed vulnerability report with exploitation proof | Runtime error detection and security risk report |
| Frequency | Periodic, often pre-deployment or scheduled | Continuous or during development cycles |
| Benefit | Identifies real-world attack vectors | Detects live issues within running code |
| Limitations | Time-consuming, requires skilled testers | May miss complex security flaws |
Understanding Penetration Testing
Penetration testing involves simulating cyberattacks on systems to identify vulnerabilities before malicious actors exploit them, providing a comprehensive assessment of security posture. This method uses real-world attack techniques, enabling testers to evaluate the effectiveness of defenses and uncover complex security weaknesses often missed by automated tools. Penetration testing is essential for organizations seeking proactive risk management and compliance with industry standards like PCI DSS and HIPAA.
What is Dynamic Analysis?
Dynamic analysis is a method of evaluating software by examining its behavior during runtime, identifying vulnerabilities such as memory leaks, race conditions, and input validation errors. Unlike penetration testing that simulates cyberattacks to uncover security flaws, dynamic analysis involves real-time monitoring and automated testing tools to detect runtime anomalies and security issues. This approach complements penetration testing by providing deeper insights into application performance, security risks, and operational weaknesses under actual execution conditions.
Key Objectives: Penetration Testing vs Dynamic Analysis
Penetration Testing aims to identify vulnerabilities by simulating real-world attacks, assessing security weaknesses across networks, applications, and systems. Dynamic Analysis focuses on examining software behavior at runtime to detect defects such as memory leaks, performance bottlenecks, and security flaws in real-time. Both methodologies enhance cybersecurity posture but differ in scope: Penetration Testing validates security defenses externally, while Dynamic Analysis provides internal insights during code execution.
Methodologies Compared
Penetration testing employs manual and automated techniques to simulate real-world cyberattacks, identifying vulnerabilities through active exploitation and assessing security posture across networks, applications, and systems. Dynamic analysis focuses on monitoring software behavior during execution, using automated tools to detect runtime vulnerabilities such as memory leaks, input validation errors, and security flaws in code. Both methodologies complement each other by combining external attack simulation with internal behavioral observation to provide a comprehensive security assessment.
Tools Used in Penetration Testing
Penetration testing relies on specialized tools such as Metasploit, Nmap, and Burp Suite to identify and exploit security vulnerabilities in networks and applications. These tools enable security professionals to simulate cyberattacks, perform reconnaissance, and execute payload delivery to assess a system's resilience. Dynamic analysis, by contrast, involves tools like OWASP ZAP and AppScan that monitor runtime behavior but do not emphasize exploitation.
Tools Used in Dynamic Analysis
Dynamic analysis employs tools such as OWASP ZAP, Burp Suite, and IBM AppScan to evaluate the security of running applications by simulating attacks in real-time. These tools facilitate the identification of vulnerabilities like SQL injection, cross-site scripting, and authentication flaws during application execution. Unlike penetration testing, dynamic analysis tools provide continuous monitoring and automated scanning, enhancing vulnerability detection efficiency in dynamic environments.
Pros and Cons of Penetration Testing
Penetration testing offers in-depth evaluation of system vulnerabilities by simulating real-world cyberattacks, providing actionable insights into security weaknesses and potential exploit paths. However, it is resource-intensive, requiring skilled professionals and significant time to perform thorough assessments, which may limit its frequency and scope. Despite these challenges, penetration testing remains essential for uncovering complex security flaws that automated dynamic analysis tools might miss.
Advantages and Limitations of Dynamic Analysis
Dynamic analysis offers real-time evaluation of software behavior by executing code in a controlled environment, enabling the detection of runtime vulnerabilities such as memory leaks, race conditions, and input validation errors. Its advantage lies in identifying issues that static methods or penetration tests might miss, especially those emerging from actual application execution under various inputs. However, it is limited by potential blind spots in code coverage, reliance on test case quality, and higher resource consumption compared to static analysis or targeted penetration testing.
When to Use Penetration Testing or Dynamic Analysis
Penetration testing is ideal when seeking a controlled, manual evaluation to identify exploitable vulnerabilities in production environments, especially for assessing real-world attack scenarios. Dynamic analysis is best utilized during the software development lifecycle to automatically detect runtime security issues by analyzing the application behavior in a test environment. Employ penetration testing for in-depth security validation before deployment, and dynamic analysis for continuous vulnerability detection during ongoing development.
Choosing the Right Approach for Cybersecurity
Penetration testing simulates real-world cyberattacks to identify vulnerabilities by exploiting security weaknesses, providing actionable insights into system defenses. Dynamic analysis evaluates applications during runtime to detect issues like memory leaks, performance bottlenecks, and security flaws through continuous monitoring. Choosing the right approach depends on the organization's specific security goals, resources, and whether the focus is on external threats or in-depth application behavior analysis.
Penetration Testing Infographic
 libterm.com
libterm.com