Hash tables provide efficient data storage and retrieval by using a hash function to map keys to specific indices in an array, enabling constant-time average search complexity. Collisions are managed through methods like chaining or open addressing to maintain performance and data integrity. Discover how hash tables optimize your programs and explore their practical implementations in the rest of this article.
Table of Comparison
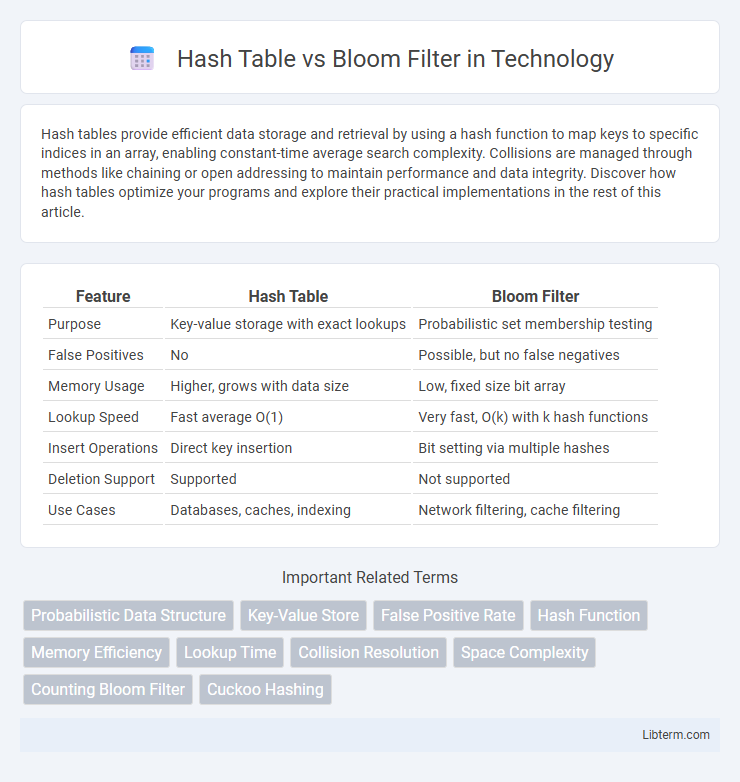
| Feature | Hash Table | Bloom Filter |
|---|---|---|
| Purpose | Key-value storage with exact lookups | Probabilistic set membership testing |
| False Positives | No | Possible, but no false negatives |
| Memory Usage | Higher, grows with data size | Low, fixed size bit array |
| Lookup Speed | Fast average O(1) | Very fast, O(k) with k hash functions |
| Insert Operations | Direct key insertion | Bit setting via multiple hashes |
| Deletion Support | Supported | Not supported |
| Use Cases | Databases, caches, indexing | Network filtering, cache filtering |
Introduction to Hash Table and Bloom Filter
Hash tables store key-value pairs using a hash function to map keys to unique indices, enabling constant-time average lookup, insertion, and deletion operations. Bloom filters are probabilistic data structures that efficiently test set membership by using multiple hash functions to set bits in a fixed-size bit array, allowing fast queries with a controlled false positive rate but no false negatives. Both leverage hashing but differ in storage, accuracy, and use cases: hash tables guarantee exact key retrieval, whereas Bloom filters provide space-efficient membership checks with probabilistic accuracy.
Core Concepts: How Hash Tables Work
Hash tables operate by mapping keys to indices in an array using a hash function, enabling fast data retrieval with average-case constant time complexity, O(1). Each key is transformed into a specific slot where the corresponding value is stored, and collisions are resolved through chaining or open addressing. This data structure is optimized for exact key matching, ensuring efficient insertion, deletion, and search operations.
Core Concepts: How Bloom Filters Work
Bloom filters use a probabilistic data structure to test whether an element is a member of a set, relying on multiple hash functions that map the element to a bit array. When an item is added, bits at positions determined by the hash functions are set to 1, enabling quick membership queries with a small memory footprint. False positives can occur because multiple elements may set overlapping bits, but false negatives are impossible, making Bloom filters efficient for space-constrained applications.
Memory Usage: Hash Table vs Bloom Filter
Hash tables store key-value pairs explicitly, which requires considerable memory proportional to the number of entries and the size of each key and value. Bloom filters use a fixed-size bit array combined with multiple hash functions, providing significant memory savings by encoding membership probabilistically rather than storing actual keys. In scenarios demanding low memory overhead with acceptable false positives, Bloom filters offer superior efficiency compared to hash tables.
Insertion and Lookup Performance Comparison
Hash tables provide constant average time complexity O(1) for both insertion and lookup operations, ensuring fast and precise data access by storing key-value pairs directly. Bloom filters, while also offering O(1) time complexity, trade off some accuracy for space efficiency by using multiple hash functions and bit arrays, leading to faster but probabilistic membership queries with possible false positives. For applications requiring exact results and dynamic data updates, hash tables outperform, whereas Bloom filters excel in scenarios demanding memory-efficient, high-speed membership checks with tolerable error rates.
Handling Collisions and False Positives
Hash tables handle collisions using techniques like chaining or open addressing, ensuring exact key-value pair retrieval without false positives. Bloom filters use multiple hash functions to map elements into a bit array, allowing fast membership queries but introducing a configurable false positive rate. While hash tables guarantee no false positives, they consume more memory compared to the space-efficient Bloom filters that trade some accuracy for reduced storage.
Use Cases: When to Use Hash Tables
Hash tables excel in scenarios requiring exact key-value mappings with frequent insert, delete, and lookup operations, such as database indexing, caching, and implementing associative arrays. Their ability to provide average constant-time complexity for search and update operations makes them ideal for applications demanding fast and precise data retrieval. Unlike Bloom filters, which are probabilistic and suited for membership testing with false positives, hash tables guarantee exact results and are preferred when accuracy is critical.
Use Cases: When to Use Bloom Filters
Bloom filters excel in scenarios requiring fast, memory-efficient membership checks with tolerable false positives, such as cache filtering, database query optimization, and network packet processing. Hash tables offer precise key-value storage and retrieval but consume more memory, making them less suitable for high-scale, probabilistic lookups. Choose bloom filters when reducing memory footprint and accelerating presence checks outweigh the need for exact accuracy.
Scalability and Limitations
Hash tables provide exact membership queries with dynamic resizing capabilities, supporting scalable storage and retrieval of large datasets while consuming significant memory. Bloom filters use probabilistic data structures that offer highly space-efficient membership testing with fixed-size arrays and controlled false positive rates, but cannot store actual data or support deletions without additional mechanisms. Scalability challenges in hash tables stem from memory overhead and collision resolution, while Bloom filters face limitations in handling false positives and lack of support for element removal.
Choosing the Right Data Structure
Choosing between a hash table and a Bloom filter depends on the need for exact key-value associations versus space-efficient membership queries. Hash tables provide constant-time lookups with precise data retrieval but consume more memory, making them ideal for applications requiring exact data storage. Bloom filters are probabilistic data structures offering highly memory-efficient membership tests with false positive rates, suitable for scenarios where space savings outweigh occasional inaccuracies.
Hash Table Infographic
 libterm.com
libterm.com