Gold Team stands out for its exceptional performance, strategic planning, and seamless teamwork in competitive environments. Their ability to adapt quickly and execute precise maneuvers consistently leads to victory across various challenges. Discover how Gold Team can elevate your game by reading the rest of the article.
Table of Comparison
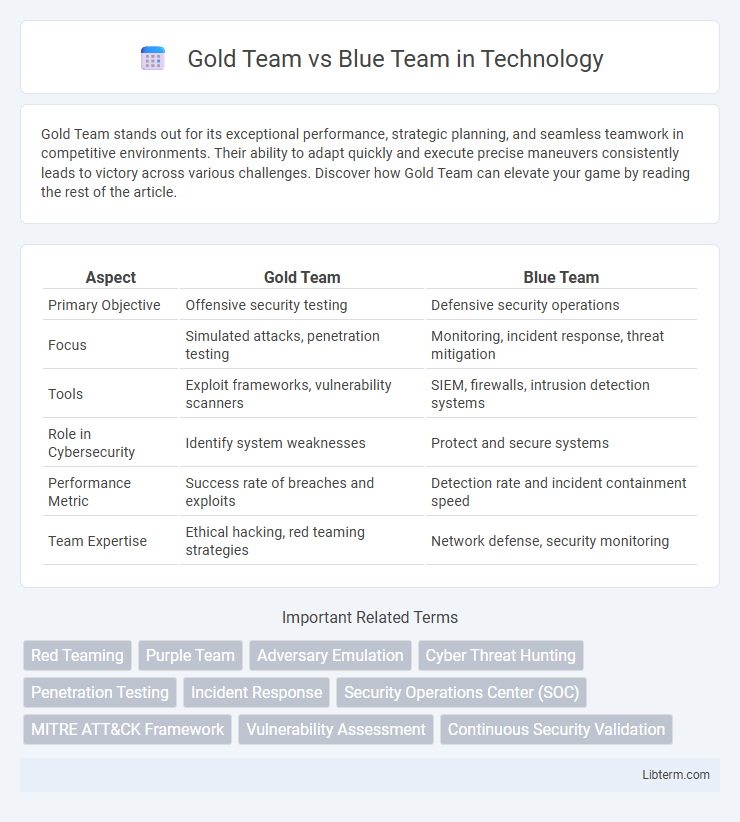
| Aspect | Gold Team | Blue Team |
|---|---|---|
| Primary Objective | Offensive security testing | Defensive security operations |
| Focus | Simulated attacks, penetration testing | Monitoring, incident response, threat mitigation |
| Tools | Exploit frameworks, vulnerability scanners | SIEM, firewalls, intrusion detection systems |
| Role in Cybersecurity | Identify system weaknesses | Protect and secure systems |
| Performance Metric | Success rate of breaches and exploits | Detection rate and incident containment speed |
| Team Expertise | Ethical hacking, red teaming strategies | Network defense, security monitoring |
Introduction to Gold Team and Blue Team
Gold Team and Blue Team represent distinct cybersecurity roles focused on defending and testing organizational security. Gold Team specializes in managing and optimizing red team operations to simulate real-world attack scenarios, enhancing the effectiveness of adversary emulation. Blue Team concentrates on continuous monitoring, incident response, and strengthening security measures to protect systems against threats uncovered by adversary activities.
Core Objectives of Gold Team Operations
Gold Team operations prioritize offensive security measures designed to simulate real-world cyberattacks, aiming to identify vulnerabilities within organizational networks and systems. Key objectives include exploiting security weaknesses, testing incident response effectiveness, and enhancing threat detection capabilities by mimicking adversarial tactics, techniques, and procedures (TTPs). These activities enable organizations to strengthen their defenses by proactively uncovering risks before Blue Team defenders can mitigate them.
Fundamental Roles of Blue Team Defense
Blue Team defense centers on threat detection, incident response, and continuous monitoring to protect organizational assets. Core roles include cybersecurity analysts who analyze alerts and vulnerabilities, incident responders who mitigate breaches swiftly, and system administrators who maintain secure network configurations. Effective collaboration ensures resilient defense against cyberattacks by strengthening perimeter security, conducting regular audits, and implementing proactive threat hunting.
Key Differences Between Gold and Blue Teams
Gold Teams specialize in offensive cybersecurity strategies, focusing on penetration testing and vulnerability exploitation to identify system weaknesses. Blue Teams emphasize defensive measures, including real-time threat detection, incident response, and system hardening to protect networks from attacks. The key difference lies in their objectives: Gold Teams simulate attacks to uncover security gaps, while Blue Teams implement safeguards and monitor for breaches to maintain organizational security.
Collaborative Scenarios: Gold Team Meets Blue Team
Gold Team and Blue Team collaboration enhances cybersecurity resilience by combining offensive tactics with defensive strategies during simulated attack scenarios. This integration allows real-time identification of vulnerabilities and immediate implementation of mitigation techniques, improving threat detection accuracy. Joint exercises between Gold and Blue Teams foster adaptive response capabilities, reducing incident response time and minimizing potential damage from cyber threats.
Tools and Techniques Used by Each Team
Gold Team utilizes offensive security tools such as Metasploit, Cobalt Strike, and custom malware for penetration testing and vulnerability exploitation. Blue Team employs defense mechanisms including SIEM systems like Splunk, endpoint detection and response (EDR) platforms such as CrowdStrike, and network monitoring tools like Wireshark to detect, analyze, and mitigate threats. Both teams leverage threat intelligence feeds and automation scripts to enhance their respective attack and defense capabilities.
Gold Team Strategies for Security Testing
Gold Team strategies for security testing emphasize proactive vulnerability identification through advanced penetration testing techniques and red teaming exercises that simulate real-world cyberattacks. They integrate threat intelligence and exploit development to uncover system weaknesses, enabling targeted remediation before adversaries can exploit them. Continuous collaboration with Blue Team ensures adaptive defense tactics while improving overall organizational resilience against evolving threats.
Blue Team Approaches to Threat Detection
Blue Team approaches to threat detection employ advanced behavioral analytics and real-time monitoring to identify anomalies within network traffic, enhancing early identification of potential cyber threats. They integrate automated threat intelligence platforms with endpoint detection and response (EDR) tools to facilitate rapid detection and containment of malicious activities. Continuous vulnerability assessments and proactive threat hunting further strengthen the ability of Blue Teams to mitigate risks before they escalate into security breaches.
Real-World Case Studies: Gold vs Blue Team
Real-world case studies of Gold Team vs Blue Team exercises reveal critical insights into cybersecurity defense strategies and attack simulations. In a notable case, a financial institution's Blue Team successfully detected and mitigated a sophisticated phishing campaign simulated by the Gold Team, highlighting the effectiveness of layered security protocols and real-time threat intelligence. Another study of a healthcare provider demonstrated how the Gold Team's targeted penetration testing exposed vulnerabilities that the Blue Team then fortified through enhanced network segmentation and incident response improvements.
Choosing the Right Approach: When to Use Each Team
Gold Team specializes in offensive cybersecurity tasks, simulating real-world attacks to identify vulnerabilities and test defenses. Blue Team focuses on defense by monitoring, detecting, and responding to security threats in real-time to protect organizational assets. Choosing the right approach depends on the objective: use Gold Team exercises for proactive vulnerability assessment and penetration testing, while Blue Team operations are essential for strengthening incident response and maintaining ongoing security posture.
Gold Team Infographic
 libterm.com
libterm.com