Red Team exercises simulate real-world cyberattacks to identify vulnerabilities in your security infrastructure before malicious hackers can exploit them. These controlled attacks help organizations strengthen their defenses by revealing weaknesses in systems, processes, and employee awareness. Explore the full article to discover how Red Team strategies can enhance your cybersecurity posture.
Table of Comparison
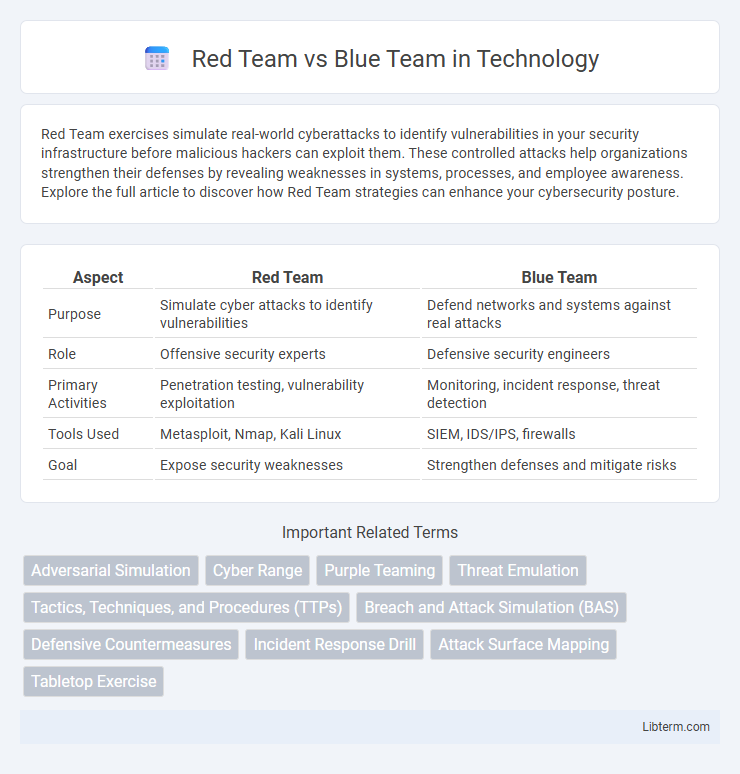
| Aspect | Red Team | Blue Team |
|---|---|---|
| Purpose | Simulate cyber attacks to identify vulnerabilities | Defend networks and systems against real attacks |
| Role | Offensive security experts | Defensive security engineers |
| Primary Activities | Penetration testing, vulnerability exploitation | Monitoring, incident response, threat detection |
| Tools Used | Metasploit, Nmap, Kali Linux | SIEM, IDS/IPS, firewalls |
| Goal | Expose security weaknesses | Strengthen defenses and mitigate risks |
Introduction to Red Team vs Blue Team
Red Team and Blue Team represent two crucial roles in cybersecurity defense and attack simulations. The Red Team acts as ethical hackers, simulating realistic cyberattacks to identify vulnerabilities within an organization's security infrastructure. The Blue Team focuses on detecting, responding to, and mitigating these simulated threats to strengthen defense mechanisms and improve overall security posture.
Defining the Red Team: Offensive Security
Red Team refers to a specialized group focused on offensive security strategies, simulating real-world cyber-attacks to identify vulnerabilities within an organization's defenses. These experts employ penetration testing, social engineering, and advanced hacking techniques to challenge security systems proactively. The goal of the Red Team is to expose weaknesses before malicious actors can exploit them, enhancing the overall cyber resilience of the organization.
Understanding the Blue Team: Defensive Security
The Blue Team specializes in defensive security by continuously monitoring networks, analyzing threats, and implementing protective measures to safeguard organizational assets. Their responsibilities include deploying firewalls, conducting vulnerability assessments, and responding promptly to security incidents to minimize damage. Effective Blue Team operations rely on real-time threat intelligence, robust incident response plans, and comprehensive system hardening practices to maintain a secure IT environment.
Key Roles and Responsibilities
Red Team members simulate real-world cyber-attacks to identify vulnerabilities and test the effectiveness of security measures within an organization. Blue Team professionals are responsible for monitoring, detecting, and responding to cyber threats in real time, ensuring the protection and resilience of IT infrastructure. Both teams collaborate through continuous feedback to strengthen overall cybersecurity posture and incident response capabilities.
Tools and Techniques Used by Both Teams
Red Teams utilize advanced penetration testing tools like Metasploit, Cobalt Strike, and custom malware to simulate real-world cyberattacks, focusing on exploiting vulnerabilities, social engineering, and evasion techniques. Blue Teams deploy defensive technologies such as Security Information and Event Management (SIEM) systems, Intrusion Detection Systems (IDS), and Endpoint Detection and Response (EDR) to monitor, analyze, and respond to threats in real time. Both teams employ threat intelligence platforms and continuous network monitoring tools to enhance their offensive and defensive strategies in cybersecurity exercises.
Common Scenarios in Red vs Blue Exercises
Common scenarios in Red Team vs Blue Team exercises include simulated cyberattacks such as phishing campaigns, malware infiltration, and insider threats designed to test an organization's detection and response capabilities. Red Team operators often emulate advanced persistent threats (APTs) by exploiting zero-day vulnerabilities and conducting lateral movement within the network. Blue Team defenders focus on incident detection, containment, and recovery by utilizing tools like Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS), and comprehensive threat hunting techniques.
Red Team and Blue Team Collaboration
Red Team and Blue Team collaboration enhances cybersecurity defenses by fostering continuous feedback loops where Red Team simulates realistic cyberattacks and Blue Team strengthens detection and response strategies. This dynamic cooperation enables identification of vulnerabilities and rapid mitigation, reinforcing organizational resilience against evolving threats. Shared insights and joint exercises improve threat intelligence, incident handling, and overall security posture through integrated adversarial thinking and defense tactics.
Benefits of Red Team vs Blue Team Exercises
Red Team vs Blue Team exercises enhance organizational cybersecurity by simulating realistic cyber attacks and defense scenarios, improving the ability to detect and respond to threats. These exercises identify system vulnerabilities and strengthen incident response, leading to more robust security policies and infrastructure. Continuous engagement in such practices fosters collaboration between offensive and defensive teams, resulting in a proactive security posture and reduced risk of breaches.
Evolving Threats and Future Trends
Red Team and Blue Team operations continuously adapt to evolving cyber threats, employing advanced tactics such as AI-driven attack simulations and automated defense mechanisms to stay ahead of sophisticated adversaries. Emerging trends include leveraging machine learning for real-time threat detection, enhanced collaboration through threat intelligence sharing platforms, and integrating zero-trust architectures to mitigate insider threats. The future landscape emphasizes proactive resilience strategies, incorporating behavioral analytics and quantum-resistant encryption to counteract the increasing complexity of cyberattacks.
Building an Effective Security Culture
Building an effective security culture requires integrating Red Team and Blue Team exercises to simulate real-world cyber threats and enhance organizational resilience. Red Teams identify vulnerabilities by mimicking attacker tactics, while Blue Teams develop robust defense mechanisms through continuous monitoring and response. This collaborative approach fosters proactive threat detection, employee awareness, and a culture of shared responsibility in cybersecurity.
Red Team Infographic
 libterm.com
libterm.com