Purple Team integrates the strengths of Red Team offensive tactics with the defensive expertise of Blue Team to enhance an organization's cybersecurity posture. By collaborating closely, they identify vulnerabilities and improve response strategies, ensuring your security framework is robust against evolving threats. Explore the rest of the article to understand how Purple Teams can transform your cybersecurity efforts.
Table of Comparison
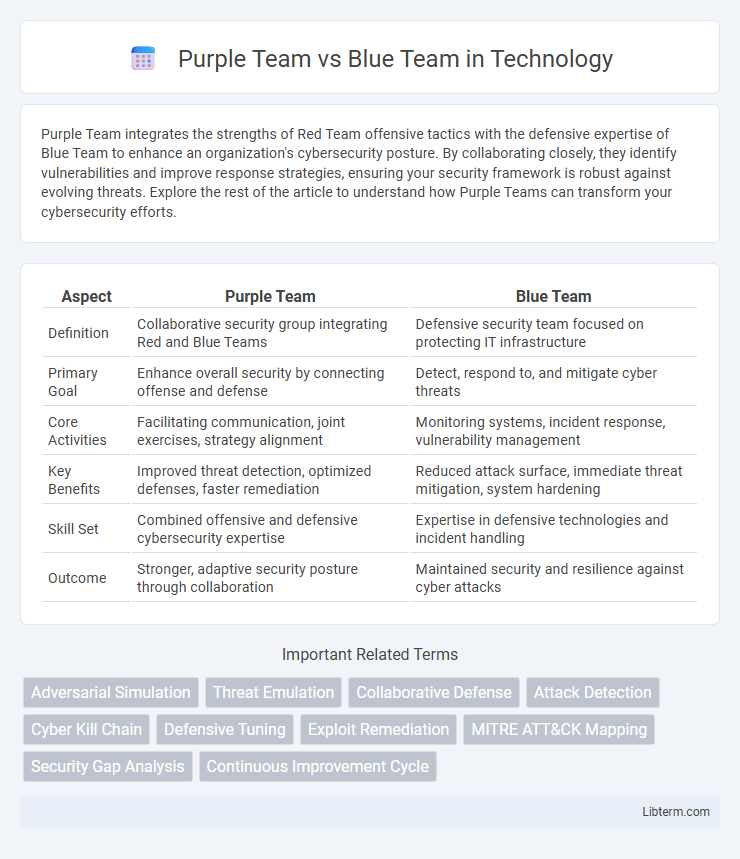
| Aspect | Purple Team | Blue Team |
|---|---|---|
| Definition | Collaborative security group integrating Red and Blue Teams | Defensive security team focused on protecting IT infrastructure |
| Primary Goal | Enhance overall security by connecting offense and defense | Detect, respond to, and mitigate cyber threats |
| Core Activities | Facilitating communication, joint exercises, strategy alignment | Monitoring systems, incident response, vulnerability management |
| Key Benefits | Improved threat detection, optimized defenses, faster remediation | Reduced attack surface, immediate threat mitigation, system hardening |
| Skill Set | Combined offensive and defensive cybersecurity expertise | Expertise in defensive technologies and incident handling |
| Outcome | Stronger, adaptive security posture through collaboration | Maintained security and resilience against cyber attacks |
Understanding Purple Team and Blue Team
Purple Team combines offensive tactics of the Red Team with the defensive skills of the Blue Team, enhancing cybersecurity by promoting collaboration and continuous feedback between attack simulation and threat defense. Blue Team specializes in defending an organization's information systems through monitoring, detecting, and responding to security incidents using tools like SIEM, IDS, and firewalls. Understanding the roles and interactions of Purple and Blue Teams helps organizations improve their security posture by integrating proactive threat hunting with robust incident response strategies.
Core Responsibilities of Blue Teams
Blue Teams primarily focus on defense by monitoring networks, systems, and endpoints to detect and respond to cyber threats in real time. Their core responsibilities include implementing cybersecurity measures such as firewalls, intrusion detection systems (IDS), and continuous threat hunting to prevent unauthorized access. They also conduct vulnerability assessments, incident response, and recovery efforts to minimize damage from security breaches and maintain organizational resilience.
The Role of Purple Teams in Cybersecurity
Purple Teams bridge the gap between Red Team offensive tactics and Blue Team defensive measures, enhancing overall cybersecurity by fostering collaboration and knowledge sharing. Their primary role involves simulating realistic cyber-attacks while continuously improving an organization's detection and response capabilities through joint exercises. By integrating threat intelligence and advanced analytic techniques, Purple Teams enable proactive defense strategies that minimize vulnerabilities and strengthen security posture.
Key Differences: Purple Team vs Blue Team
Purple Team integrates both offensive and defensive cybersecurity strategies, combining Red Team's attack simulations with Blue Team's defense mechanisms to enhance organizational security. Blue Team specializes in monitoring, defending, and responding to threats in real-time, employing tools like SIEM, intrusion detection systems, and incident response protocols. The key difference lies in Purple Team's collaborative approach to proactively identify vulnerabilities, while Blue Team primarily focuses on maintaining and strengthening existing security postures.
Collaboration Strategies for Enhanced Security
Purple Team and Blue Team collaboration strategies enhance security by integrating offensive tactics with defensive measures, enabling real-time feedback and continuous improvement. Joint exercises such as simulated attacks and threat hunting foster shared intelligence, increasing detection and response capabilities against advanced persistent threats (APTs). Leveraging automated tools and communication platforms strengthens coordination, reduces attack surface vulnerabilities, and accelerates incident mitigation processes.
Tools and Techniques Used by Each Team
Purple Teams integrate offensive tools like Metasploit and Cobalt Strike with defensive solutions such as Splunk and Wireshark to enhance collaboration and improve overall security posture. Blue Teams utilize monitoring and detection tools including Security Information and Event Management (SIEM) systems, endpoint detection and response (EDR) platforms, and network traffic analysis tools like Zeek to identify and mitigate threats in real time. Both teams employ threat intelligence feeds and vulnerability assessment tools to continuously refine their tactics and strengthen organizational defenses.
Real-World Use Cases and Scenarios
Purple Team exercises enhance collaboration between Red Team attackers and Blue Team defenders by simulating realistic cyberattack scenarios to improve detection and response capabilities. Blue Teams primarily focus on continuous monitoring, threat hunting, and incident response in enterprise environments to protect networks from ransomware, phishing, and Advanced Persistent Threats (APTs). Real-world use cases include Purple Teams orchestrating joint simulations to fine-tune security controls, while Blue Teams implement these insights to strengthen firewall rules, SIEM alerts, and endpoint protection in critical infrastructure and financial institutions.
Benefits of Integrating Purple and Blue Teams
Integrating Purple and Blue Teams enhances organizational cybersecurity by combining offensive tactics and defensive strategies, leading to more comprehensive threat detection and response. This collaboration facilitates continuous feedback loops where Blue Team defenders improve security measures based on real-time adversarial insights from Purple Team exercises. Leveraging this integrated approach reduces vulnerabilities, accelerates incident response times, and strengthens overall resilience against sophisticated cyberattacks.
Challenges in Purple-Blue Team Operations
Purple team operations face significant challenges in balancing offensive tactics with defensive strategies, often requiring seamless collaboration between red and blue teams to identify and remediate vulnerabilities effectively. Differences in team objectives, communication gaps, and varying skill sets can hinder unified threat detection and response efforts during joint exercises. Continuous alignment and sophisticated coordination tools are essential to overcoming these operational hurdles and enhancing overall cybersecurity posture.
Future Trends in Team-Based Cyber Defense
Purple Team and Blue Team collaboration is evolving through increased integration of AI-driven analytics and automated threat detection tools, enhancing proactive threat hunting and rapid incident response. Future trends emphasize continuous real-time simulation and adaptive training environments to improve teamwork and resilience against advanced persistent threats (APTs). Enhanced information sharing platforms are facilitating seamless communication and coordinated defense strategies between teams, optimizing overall cybersecurity posture.
Purple Team Infographic
 libterm.com
libterm.com