Digital signatures provide a secure and efficient way to verify the authenticity and integrity of electronic documents, ensuring that the content has not been altered. They rely on cryptographic algorithms to create a unique identifier linked to the document and the signer's identity. Explore the rest of the article to understand how digital signatures enhance security and streamline your document verification process.
Table of Comparison
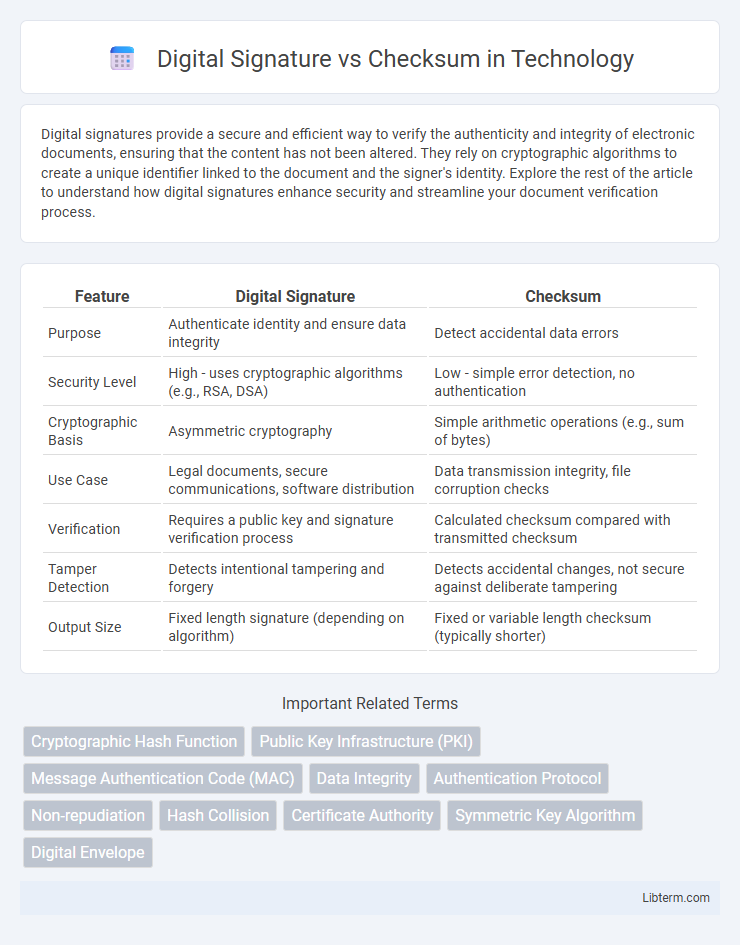
| Feature | Digital Signature | Checksum |
|---|---|---|
| Purpose | Authenticate identity and ensure data integrity | Detect accidental data errors |
| Security Level | High - uses cryptographic algorithms (e.g., RSA, DSA) | Low - simple error detection, no authentication |
| Cryptographic Basis | Asymmetric cryptography | Simple arithmetic operations (e.g., sum of bytes) |
| Use Case | Legal documents, secure communications, software distribution | Data transmission integrity, file corruption checks |
| Verification | Requires a public key and signature verification process | Calculated checksum compared with transmitted checksum |
| Tamper Detection | Detects intentional tampering and forgery | Detects accidental changes, not secure against deliberate tampering |
| Output Size | Fixed length signature (depending on algorithm) | Fixed or variable length checksum (typically shorter) |
Introduction to Digital Signature and Checksum
Digital signatures use cryptographic algorithms to verify the authenticity and integrity of digital messages or documents by generating a unique signature based on the sender's private key. Checksums, on the other hand, are simpler error-detecting codes calculated from the data content to identify accidental changes during transmission or storage. While checksums detect data corruption, digital signatures provide proof of origin and non-repudiation, making them essential in secure communications.
What is a Digital Signature?
A digital signature is a cryptographic tool that verifies the authenticity and integrity of a digital message or document by using a private key to generate a unique encrypted hash value. Unlike a checksum, which only detects errors in data transmission, a digital signature provides non-repudiation by confirming the sender's identity and ensuring the content has not been altered. Digital signatures are widely used in secure communications, software distribution, and legal documents to establish trust and data authenticity.
What is a Checksum?
A checksum is a calculated value used to verify the integrity of data by detecting errors during transmission or storage. It works by applying a hashing algorithm to a data set, producing a unique string of characters that changes if the data is altered. Unlike digital signatures, which provide authentication and non-repudiation, checksums primarily ensure data has not been corrupted or tampered with.
Core Differences Between Digital Signatures and Checksums
Digital signatures provide authentication, non-repudiation, and integrity by using asymmetric encryption to create a unique signature linked to the sender's private key, ensuring the message originates from the claimed sender. Checksums, on the other hand, are simple error-detection codes calculated through hash functions to verify data integrity but do not offer authentication or non-repudiation. While checksums detect accidental data corruption, digital signatures protect against intentional tampering by validating both data integrity and the sender's identity.
Security Mechanisms: Digital Signature vs Checksum
Digital signatures use asymmetric cryptography to provide authentication, non-repudiation, and data integrity by linking a user's private key to the document. In contrast, checksums are computed values used solely to detect accidental data corruption with no built-in authentication or non-repudiation capabilities. The security strength of digital signatures surpasses checksums due to encryption and identity verification, whereas checksums are vulnerable to intentional tampering without key-based protection.
Use Cases of Digital Signature
Digital signatures provide authentication, non-repudiation, and data integrity in transactions such as electronic contracts, software distribution, and secure email communication. They are crucial in legal agreements, financial services, and government documentation to verify the identity of the sender and ensure the message has not been altered. Unlike checksums, which only detect data corruption, digital signatures use cryptographic algorithms to establish trust and protect against forgery.
Use Cases of Checksum
Checksums are primarily used for error detection in data transmission and storage, ensuring data integrity by verifying that information remains unchanged during transfer or retrieval. Common use cases include verifying filenames in downloads, validating data packets in network communications, and detecting corruption in files stored on disks. Unlike digital signatures, checksums do not provide authentication or non-repudiation but serve as a quick method to identify accidental data alterations.
Advantages and Limitations of Digital Signatures
Digital signatures provide strong authentication, data integrity, and non-repudiation, ensuring that documents are verified and tamper-proof. They offer legal validity and cryptographic security, making them essential for secure electronic transactions. However, digital signatures require complex infrastructure such as Public Key Infrastructure (PKI) and may face compatibility issues across different platforms.
Pros and Cons of Using Checksums
Checksums provide a fast and straightforward method for verifying data integrity by detecting accidental errors during transmission or storage, but they cannot authenticate the sender or protect against intentional tampering, limiting their security functionality. While checksums are computationally efficient and require less processing power compared to digital signatures, their inability to prevent malicious modifications makes them unsuitable for scenarios requiring robust data authentication. In contrast, digital signatures utilize cryptographic algorithms to ensure both data integrity and non-repudiation, offering stronger security at the cost of increased computational overhead.
Choosing Between Digital Signature and Checksum
When choosing between a digital signature and a checksum, prioritize security requirements and authentication needs. Digital signatures provide non-repudiation, data integrity, and verification using asymmetric cryptography, making them ideal for legal documents and secure communications. Checksums focus on error detection by verifying data integrity with simpler algorithms but do not offer authentication or protection against malicious tampering.
Digital Signature Infographic
 libterm.com
libterm.com