Cross-Site Scripting (XSS) is a security vulnerability that allows attackers to inject malicious scripts into trusted websites, potentially compromising user data and session integrity. This type of attack exploits vulnerabilities in web applications to execute unauthorized code in the user's browser, leading to identity theft, data breaches, and unauthorized actions on behalf of the user. Discover how to protect your website from XSS attacks and maintain robust security by reading the full article.
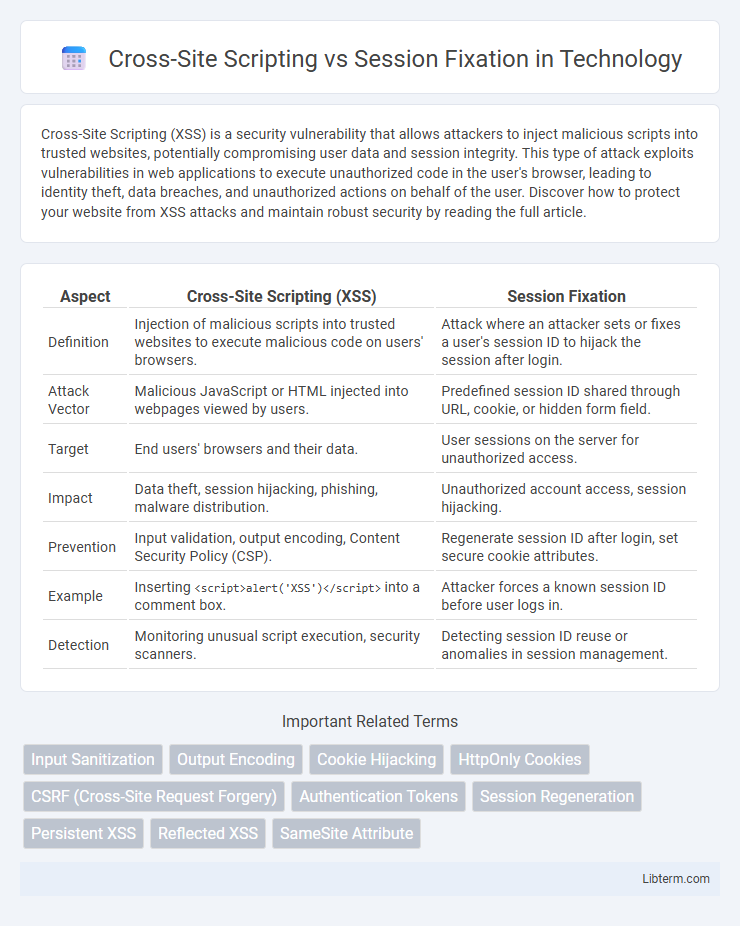
Table of Comparison
| Aspect | Cross-Site Scripting (XSS) | Session Fixation |
|---|---|---|
| Definition | Injection of malicious scripts into trusted websites to execute malicious code on users' browsers. | Attack where an attacker sets or fixes a user's session ID to hijack the session after login. |
| Attack Vector | Malicious JavaScript or HTML injected into webpages viewed by users. | Predefined session ID shared through URL, cookie, or hidden form field. |
| Target | End users' browsers and their data. | User sessions on the server for unauthorized access. |
| Impact | Data theft, session hijacking, phishing, malware distribution. | Unauthorized account access, session hijacking. |
| Prevention | Input validation, output encoding, Content Security Policy (CSP). | Regenerate session ID after login, set secure cookie attributes. |
| Example | Inserting <script>alert('XSS')</script> into a comment box. |
Attacker forces a known session ID before user logs in. |
| Detection | Monitoring unusual script execution, security scanners. | Detecting session ID reuse or anomalies in session management. |
Introduction to Web Application Vulnerabilities
Cross-Site Scripting (XSS) and Session Fixation are common web application vulnerabilities that compromise user security and data integrity. XSS enables attackers to inject malicious scripts into trusted websites, whereas Session Fixation tricks users into using a predefined session ID to hijack active sessions. Understanding these vulnerabilities is crucial for implementing effective security measures in web application development and safeguarding sensitive information.
Understanding Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is a web security vulnerability that allows attackers to inject malicious scripts into trusted websites, targeting the end user's browser. This attack exploits insufficient input validation or output encoding, enabling scripts to steal cookies, session tokens, or other sensitive information. Understanding XSS involves recognizing the importance of sanitizing user inputs and implementing Content Security Policy (CSP) to mitigate script injection risks effectively.
Types of Cross-Site Scripting Attacks
Cross-Site Scripting (XSS) attacks primarily include Stored XSS, Reflected XSS, and DOM-based XSS, each exploiting vulnerabilities in different ways to inject malicious scripts into web applications. Stored XSS involves permanently embedding harmful scripts into target websites, affecting all users who access the compromised content. Reflected XSS sends malicious code through user input in HTTP requests that is reflected back by the server, while DOM-based XSS manipulates the client-side document object model to execute scripts without server interaction.
What is Session Fixation?
Session Fixation is a web security vulnerability where an attacker forces a user's session ID to a known value, enabling unauthorized access once the victim logs in. Unlike Cross-Site Scripting (XSS), which exploits client-side scripts to inject malicious code, Session Fixation targets the session management mechanism by hijacking or predefining session tokens. Preventing this attack requires regenerating session IDs after authentication and implementing secure cookie attributes.
Methods Used in Session Fixation Attacks
Session Fixation attacks manipulate a user's session by forcing them to use a known session ID, often through URLs, cookies, or hidden form fields, which the attacker can then exploit to hijack the session. Attackers typically set the victim's session ID before login by embedding the fixation token in links, HTTP headers, or through social engineering techniques. Effective defense mechanisms include regenerating session IDs upon authentication and implementing secure cookie attributes like HttpOnly and Secure to prevent session fixation exploitation.
Comparing Cross-Site Scripting and Session Fixation
Cross-Site Scripting (XSS) exploits vulnerabilities by injecting malicious scripts into web pages viewed by other users, compromising user data and session cookies. Session Fixation attacks target the server-side session management by forcing a user to use a known session ID, enabling attackers to hijack active sessions after authentication. While XSS involves client-side script injection affecting multiple users, Session Fixation specifically manipulates session IDs to gain unauthorized access to a single user's session.
Impact on Users and Applications
Cross-Site Scripting (XSS) enables attackers to inject malicious scripts into web pages, compromising user data, hijacking sessions, and defacing websites, which undermines user trust and data integrity. Session Fixation targets the session management mechanism by forcing users to adopt a known session ID, allowing attackers to hijack authenticated sessions and gain unauthorized access to user accounts and sensitive information. Both vulnerabilities significantly impact application security by enabling identity theft, data breaches, and unauthorized actions within the compromised user sessions.
Detection Techniques for XSS and Session Fixation
Detecting Cross-Site Scripting (XSS) involves techniques such as content security policy (CSP) monitoring, input validation automation, and heuristic analysis of script injections within user inputs. Session fixation detection relies on monitoring session token integrity, observing irregular session ID changes, and employing secure session management practices that detect anomalies in session handling. Advanced intrusion detection systems (IDS) and behavior-based analytics enhance the identification of both XSS payloads and session fixation attempts by analyzing traffic patterns and user behavior deviations.
Prevention and Mitigation Strategies
Cross-Site Scripting (XSS) prevention relies on input validation, output encoding, and Content Security Policy (CSP) implementation to block malicious scripts, while Session Fixation mitigation requires regenerating session IDs upon user authentication and setting secure, HttpOnly, and SameSite cookie attributes. Employing web application firewalls (WAFs) enhances defense by detecting and blocking suspicious activities associated with both XSS and session fixation attacks. Continuous security testing, including penetration testing and vulnerability scanning, ensures that these protective measures adapt to evolving threats in real-time.
Best Practices for Secure Web Development
To prevent Cross-Site Scripting (XSS) and Session Fixation attacks in secure web development, implement strict input validation and output encoding to neutralize malicious scripts effectively. Employ secure cookie attributes such as HttpOnly, Secure, and SameSite to protect session identifiers from interception and fixation. Regularly rotate session IDs upon login and enforce strong session expiration policies to minimize risks associated with session hijacking.
Cross-Site Scripting Infographic
 libterm.com
libterm.com