SQL injection exploits vulnerabilities in database queries to manipulate or access data unauthorizedly, posing significant security risks to applications. Protecting your databases requires implementing prepared statements, parameterized queries, and input validation to prevent malicious code from altering SQL commands. Explore the rest of this article to learn effective strategies for detecting and mitigating SQL injection attacks.
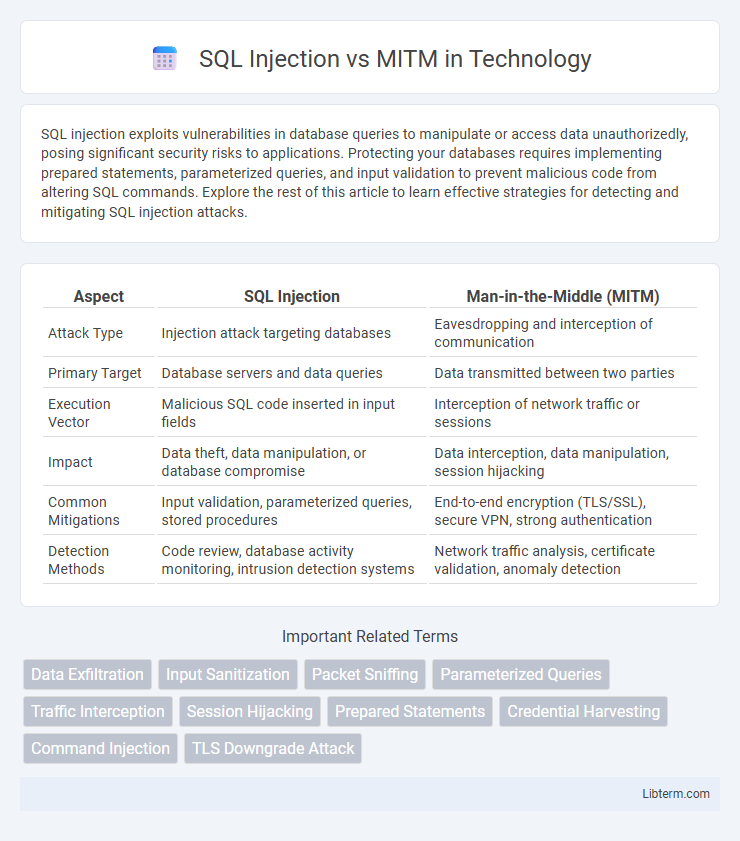
Table of Comparison
| Aspect | SQL Injection | Man-in-the-Middle (MITM) |
|---|---|---|
| Attack Type | Injection attack targeting databases | Eavesdropping and interception of communication |
| Primary Target | Database servers and data queries | Data transmitted between two parties |
| Execution Vector | Malicious SQL code inserted in input fields | Interception of network traffic or sessions |
| Impact | Data theft, data manipulation, or database compromise | Data interception, data manipulation, session hijacking |
| Common Mitigations | Input validation, parameterized queries, stored procedures | End-to-end encryption (TLS/SSL), secure VPN, strong authentication |
| Detection Methods | Code review, database activity monitoring, intrusion detection systems | Network traffic analysis, certificate validation, anomaly detection |
Introduction to SQL Injection and MITM Attacks
SQL Injection exploits vulnerabilities in web applications by inserting malicious SQL code to manipulate databases and access unauthorized data. Man-in-the-Middle (MITM) attacks intercept communication between two parties to eavesdrop or alter data in transit without detection. Both pose significant cybersecurity threats, but SQL Injection targets backend databases while MITM targets network communication.
Understanding SQL Injection: Definition and Mechanisms
SQL Injection is a cyberattack targeting databases through malicious SQL code input, exploiting vulnerabilities in user input validation to manipulate or access sensitive data. It leverages unfiltered or improperly sanitized queries, enabling attackers to execute unauthorized commands such as data retrieval, modification, or deletion. This attack contrasts with Man-in-the-Middle (MITM) attacks, which intercept and alter communications between parties rather than directly targeting database query structures.
MITM Attacks: Techniques and Workflow
MITM (Man-in-the-Middle) attacks intercept and manipulate communication between two parties without their knowledge, often using techniques like packet sniffing, session hijacking, and SSL stripping. Attackers exploit unsecured networks or weak encryption protocols to insert themselves into the data flow, capturing sensitive information such as passwords, credit card numbers, or session tokens. The typical workflow involves eavesdropping on the target connection, intercepting data packets, altering or injecting malicious content, and relaying the communication to maintain the illusion of a normal conversation.
Key Differences Between SQL Injection and MITM Attacks
SQL Injection targets vulnerabilities in a web application's database query by injecting malicious SQL code to manipulate or access sensitive data unauthorizedly. Man-in-the-Middle (MITM) attacks intercept or alter communications between two parties to eavesdrop, steal information, or inject false data without the target's knowledge. SQL Injection exploits application-layer database flaws, while MITM exploits network-layer communication weaknesses, highlighting their distinct attack vectors and defense mechanisms.
Common Vulnerabilities Exploited by SQL Injection
SQL Injection exploits vulnerabilities in web application databases by injecting malicious SQL code to manipulate or extract sensitive data, often due to improper input validation or parameterized query usage. Common vulnerabilities enabling SQL Injection include unescaped user inputs, lack of prepared statements, and poor error handling that reveal database structure. Man-in-the-Middle (MITM) attacks, in contrast, intercept communication between parties, targeting data in transit rather than backend database architecture.
MITM Attack Vectors in Modern Networks
MITM attacks exploit vulnerabilities in modern network protocols such as Wi-Fi, DNS, and HTTPS to intercept and manipulate data between communicating parties. Common attack vectors include rogue Wi-Fi hotspots, DNS spoofing, and SSL stripping, enabling attackers to capture sensitive information or inject malicious content. Advanced techniques like ARP poisoning and TCP session hijacking further compromise data integrity and confidentiality in enterprise and public networks.
Real-World Examples: SQL Injection vs MITM
Real-world examples of SQL Injection attacks include the 2012 LinkedIn breach, where attackers exploited vulnerable database queries to access millions of user passwords. Man-in-the-Middle (MITM) attacks were notably demonstrated in the 2013 Target breach, where hackers intercepted communication between the retailer's network and payment card processing systems, leading to massive credit card data theft. Both attack types highlight critical vulnerabilities in data security but differ in execution: SQL Injection targets backend databases through malicious code, while MITM manipulates data interception within communication channels.
Detection Methods for SQL Injection and MITM Attacks
SQL Injection detection methods primarily rely on input validation, anomaly detection in database queries, and monitoring unusual database activity patterns such as unexpected SQL error messages or atypical query execution times. Man-in-the-Middle (MITM) attack detection techniques include monitoring network traffic for cipher inconsistencies, verifying certificate authenticity using Public Key Infrastructure (PKI), and detecting sudden changes in IP or MAC address associations indicative of interception. Both attack types benefit from employing intrusion detection systems (IDS) and implementing secure communication protocols like TLS to minimize exploitation risks.
Prevention Strategies: Securing Against SQL Injection and MITM
Implement prepared statements and parameterized queries to prevent SQL Injection attacks by ensuring user inputs are treated as data, not executable code. Use HTTPS and strong encryption protocols such as TLS to safeguard communication channels from Man-in-the-Middle (MITM) attacks by verifying server authenticity and encrypting transmitted data. Regularly update and patch database management systems, web servers, and network devices to close vulnerabilities exploited by both SQL Injection and MITM attackers.
Conclusion: Choosing the Right Security Measures
Selecting the appropriate security measures requires understanding the distinct threats posed by SQL Injection and Man-in-the-Middle (MITM) attacks. Implementing parameterized queries and input validation effectively mitigates SQL Injection vulnerabilities, while deploying strong encryption protocols such as TLS and mutual authentication protects against MITM attacks. A comprehensive security strategy integrates both database security best practices and network encryption to safeguard data integrity and confidentiality.
SQL Injection Infographic
 libterm.com
libterm.com