Encryption secures your digital information by converting data into unreadable code, preventing unauthorized access. It plays a vital role in safeguarding sensitive communications, financial transactions, and personal data from cyber threats. Discover how encryption protects your privacy and the technologies behind it by reading the full article.
Table of Comparison
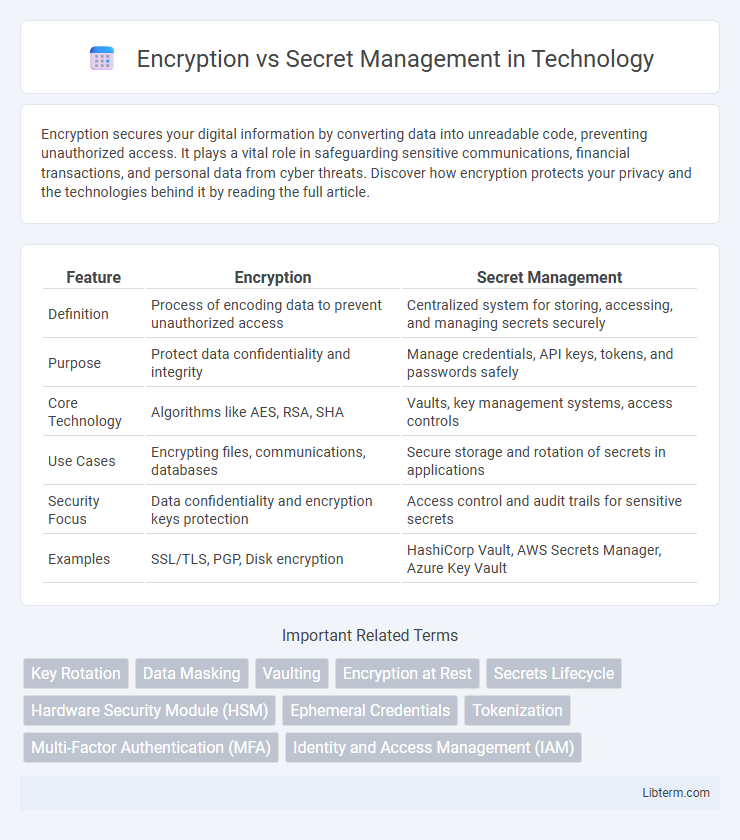
| Feature | Encryption | Secret Management |
|---|---|---|
| Definition | Process of encoding data to prevent unauthorized access | Centralized system for storing, accessing, and managing secrets securely |
| Purpose | Protect data confidentiality and integrity | Manage credentials, API keys, tokens, and passwords safely |
| Core Technology | Algorithms like AES, RSA, SHA | Vaults, key management systems, access controls |
| Use Cases | Encrypting files, communications, databases | Secure storage and rotation of secrets in applications |
| Security Focus | Data confidentiality and encryption keys protection | Access control and audit trails for sensitive secrets |
| Examples | SSL/TLS, PGP, Disk encryption | HashiCorp Vault, AWS Secrets Manager, Azure Key Vault |
Introduction to Encryption and Secret Management
Encryption transforms data into a coded format to prevent unauthorized access, ensuring confidentiality and integrity of sensitive information. Secret management involves the secure storage, distribution, and access control of cryptographic keys, passwords, and API tokens used in encryption processes. Both are essential components in cybersecurity, working together to protect data from breaches and unauthorized disclosures.
Understanding Encryption: Key Concepts
Encryption transforms readable data into ciphertext using algorithms and keys, ensuring confidentiality and data integrity during storage or transmission. Keys, including symmetric (single key) and asymmetric (public-private key pairs), are critical for encrypting and decrypting information securely. Understanding key management practices is essential to prevent unauthorized access and maintain the effectiveness of encryption in protecting sensitive data.
What is Secret Management?
Secret management involves securely storing, accessing, and controlling sensitive information such as API keys, passwords, and cryptographic keys within an organization's infrastructure. It ensures that secrets are encrypted at rest and in transit, while providing role-based access control, auditing, and automated secret rotation to minimize security risks. Unlike encryption, which protects data by transforming it into unreadable formats, secret management focuses on the lifecycle and governance of sensitive credentials used within applications and systems.
Key Differences Between Encryption and Secret Management
Encryption transforms data into unreadable ciphertext using cryptographic algorithms and keys to ensure confidentiality, while secret management involves securely storing, distributing, and rotating sensitive information such as passwords, API keys, and certificates. Encryption is primarily a data protection mechanism, whereas secret management encompasses broader lifecycle management of secrets to prevent unauthorized access. Key differences include encryption's focus on data confidentiality versus secret management's emphasis on secure handling and access control of secrets throughout their lifecycle.
Use Cases for Encryption
Encryption secures sensitive data by converting it into unreadable ciphertext, making it essential for protecting information in transit and at rest, such as securing emails, financial transactions, and personal data stored in databases. Use cases include safeguarding communication channels via TLS, encrypting files and disks to prevent unauthorized access, and enabling secure data sharing in cloud environments. Encryption ensures compliance with regulations like GDPR and HIPAA by maintaining data confidentiality and integrity throughout its lifecycle.
Use Cases for Secret Management
Secret management solutions are essential for securely storing, accessing, and distributing sensitive information such as API keys, passwords, and certificates across cloud environments and DevOps pipelines. They enable automated credential rotation, fine-grained access control, and audit logging to reduce the risk of unauthorized access and data breaches. Use cases span protecting secrets in container orchestration systems like Kubernetes, managing credentials in CI/CD workflows, and ensuring compliance with industry standards through centralized secret vaults.
Common Encryption Techniques
Common encryption techniques include symmetric-key algorithms like AES (Advanced Encryption Standard), which use the same key for both encryption and decryption, and asymmetric-key algorithms such as RSA (Rivest-Shamir-Adleman), relying on a public-private key pair for secure communication. Secret management often involves secure storage and rotation of cryptographic keys, tokens, and passwords, ensuring that these sensitive credentials are protected throughout their lifecycle. Combining encryption techniques with robust secret management practices enhances overall data security by preventing unauthorized access and minimizing the risk of key exposure.
Popular Secret Management Tools
Popular secret management tools like HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault provide centralized platforms to securely store, access, and manage cryptographic keys, API keys, passwords, and other sensitive information. Encryption focuses on protecting data confidentiality by converting plaintext into ciphertext, whereas secret management tools offer features such as automated secret rotation, access control policies, audit logging, and seamless integration with cloud-native environments to reduce the risk of exposure and unauthorized access. These tools play a crucial role in DevOps and cloud security by enabling secure secret injection and reducing human error in handling sensitive credentials.
Security Challenges and Best Practices
Encryption protects data by converting it into unreadable code, preventing unauthorized access during storage or transmission, but managing encryption keys securely remains a critical challenge. Secret management involves securely storing, distributing, and rotating credentials, API keys, and tokens to minimize risks of leakage or misuse in dynamic environments. Best practices include implementing hardware security modules (HSMs), automating secret rotation, enforcing least privilege access, and employing strong encryption algorithms like AES-256 to enhance overall security posture.
Choosing the Right Solution for Your Needs
Encryption safeguards data by converting it into unreadable formats, ensuring confidentiality during storage and transmission, while secret management securely handles sensitive information like API keys, passwords, and certificates across applications. Selecting the right solution depends on specific business requirements, including data sensitivity, compliance standards, and operational complexity. Combining encryption with a robust secret management system enhances overall security posture by protecting data both at rest and in transit, and by managing access credentials effectively.
Encryption Infographic
 libterm.com
libterm.com