Conducting a thorough risk assessment is essential for identifying potential hazards and evaluating the likelihood and impact of various threats to your organization. Effective risk assessment helps prioritize resources and implement appropriate mitigation strategies to protect assets and ensure operational continuity. Explore the rest of this article to discover practical steps and tools for mastering risk assessment in your workplace.
Table of Comparison
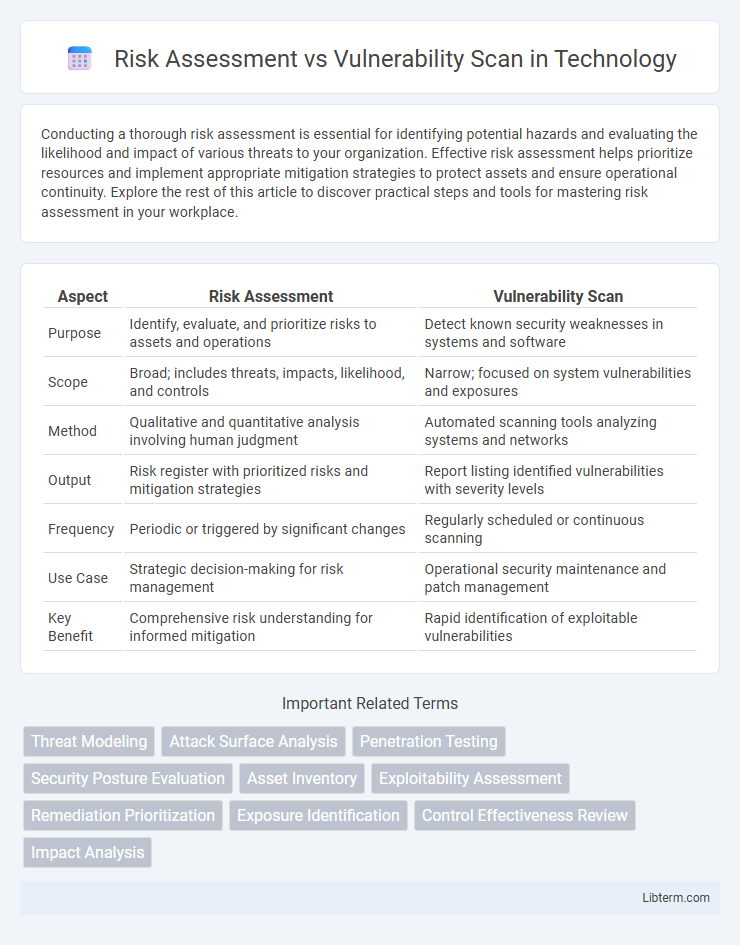
| Aspect | Risk Assessment | Vulnerability Scan |
|---|---|---|
| Purpose | Identify, evaluate, and prioritize risks to assets and operations | Detect known security weaknesses in systems and software |
| Scope | Broad; includes threats, impacts, likelihood, and controls | Narrow; focused on system vulnerabilities and exposures |
| Method | Qualitative and quantitative analysis involving human judgment | Automated scanning tools analyzing systems and networks |
| Output | Risk register with prioritized risks and mitigation strategies | Report listing identified vulnerabilities with severity levels |
| Frequency | Periodic or triggered by significant changes | Regularly scheduled or continuous scanning |
| Use Case | Strategic decision-making for risk management | Operational security maintenance and patch management |
| Key Benefit | Comprehensive risk understanding for informed mitigation | Rapid identification of exploitable vulnerabilities |
Introduction to Risk Assessment and Vulnerability Scanning
Risk assessment is a comprehensive process that identifies, evaluates, and prioritizes potential threats to an organization's assets, focusing on the likelihood and impact of different risk scenarios. Vulnerability scanning is a technical procedure that automatically detects known security weaknesses and exposures in systems, networks, or applications without assessing their overall business impact. Combining risk assessment and vulnerability scanning enhances cybersecurity by aligning identified vulnerabilities with organizational risk levels to determine appropriate mitigation strategies.
Defining Risk Assessment
Risk assessment is a systematic process of identifying, evaluating, and prioritizing potential threats to an organization's assets, focusing on the likelihood and impact of risks. It involves analyzing vulnerabilities, threats, and existing controls to determine risk levels and inform decision-making for risk mitigation. Unlike vulnerability scans that detect technical weaknesses, risk assessment provides a comprehensive evaluation of security posture by integrating business context and potential consequences.
Understanding Vulnerability Scanning
Vulnerability scanning is an automated process that identifies and catalogs security weaknesses in IT systems, focusing on known vulnerabilities across software, hardware, and network configurations. Unlike risk assessment, which evaluates the potential impact and likelihood of threats exploiting vulnerabilities, vulnerability scanning provides a snapshot of existing security gaps by continuously scanning for outdated patches, misconfigurations, and exploitable flaws. Effective vulnerability scanning supports proactive remediation efforts by delivering detailed reports that help prioritize vulnerabilities based on severity and exposure.
Key Differences Between Risk Assessment and Vulnerability Scan
Risk assessment evaluates the overall security posture by identifying, analyzing, and prioritizing risks based on potential impact and likelihood, while vulnerability scanning systematically detects known weaknesses and configuration flaws in systems. Risk assessment incorporates business context, threat intelligence, and asset value to determine risk levels, whereas vulnerability scans provide technical data used as an input for risk analysis. The key difference lies in risk assessment's broader scope and decision-making focus versus the vulnerability scan's specific role in discovering security gaps.
Purposes and Objectives of Each Approach
Risk assessment identifies and evaluates potential threats and their impact on organizational assets to prioritize security measures and allocate resources effectively. Vulnerability scanning systematically detects specific security weaknesses in systems, applications, or networks to facilitate timely remediation and reduce exposure. While risk assessment offers a strategic overview of risks to inform decision-making, vulnerability scanning provides tactical insights by pinpointing exact vulnerabilities for immediate action.
Methodologies Used in Risk Assessment vs Vulnerability Scanning
Risk assessment methodologies involve a comprehensive analysis of potential threats, impacts, and existing controls through qualitative or quantitative frameworks such as NIST SP 800-30 or OCTAVE. Vulnerability scanning employs automated tools like Nessus or OpenVAS to identify security weaknesses by probing systems, networks, or applications for known vulnerabilities. While risk assessments focus on contextual evaluation and prioritization of risks based on likelihood and impact, vulnerability scanning provides a snapshot of exploitable flaws without assessing their business impact.
Tools and Technologies Involved
Risk assessment involves comprehensive methodologies using tools like FAIR (Factor Analysis of Information Risk) and quantitative risk modeling software to evaluate potential threats and the impact on assets. Vulnerability scans rely on specialized technologies such as Nessus, OpenVAS, and Qualys, which automate the detection of security weaknesses in systems and networks. Both approaches utilize integration with SIEM (Security Information and Event Management) platforms to enhance threat analysis and response capabilities.
Benefits and Limitations of Each Method
Risk assessment identifies and prioritizes threats by evaluating the potential impact and likelihood, offering strategic insights for resource allocation but can be time-consuming and dependent on expert judgment. Vulnerability scanning rapidly detects security weaknesses in systems and applications, enabling timely remediation, yet may produce false positives and lacks context on the risk impact. Combining both methods enhances overall cybersecurity by providing a comprehensive view of risks and technical vulnerabilities.
Choosing the Right Approach for Your Organization
Risk assessment evaluates potential threats based on likelihood and impact, providing a strategic overview tailored to organizational goals and industry compliance requirements. Vulnerability scans identify specific security weaknesses in systems and networks, delivering actionable data for immediate remediation. Selecting the right approach depends on organizational risk tolerance, resource availability, and whether the priority is long-term risk management or real-time threat identification.
Integrating Risk Assessment and Vulnerability Scanning Strategies
Integrating risk assessment and vulnerability scanning strategies enhances cybersecurity by combining quantitative risk analysis with real-time identification of security flaws. This holistic approach allows organizations to prioritize vulnerabilities based on their potential impact and likelihood, thereby optimizing resource allocation for remediation. Leveraging automated scanning tools alongside comprehensive risk models ensures continuous monitoring and dynamic adjustment to emerging threats.
Risk Assessment Infographic
 libterm.com
libterm.com