A Man-in-the-Middle (MitM) attack occurs when a malicious actor intercepts communication between two parties, secretly altering or eavesdropping on the exchange without their knowledge. This form of cyber threat can compromise sensitive information, such as login credentials or financial data, by manipulating data transmissions in real time. Discover how to recognize, prevent, and respond to MitM attacks in the rest of this article to protect your digital interactions.
Table of Comparison
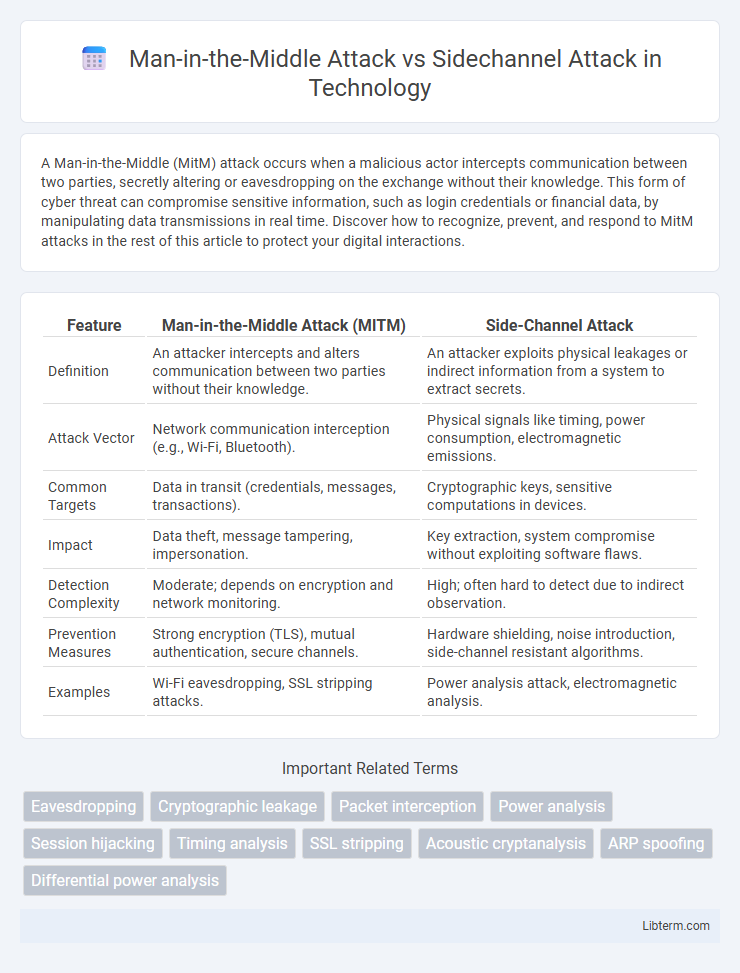
| Feature | Man-in-the-Middle Attack (MITM) | Side-Channel Attack |
|---|---|---|
| Definition | An attacker intercepts and alters communication between two parties without their knowledge. | An attacker exploits physical leakages or indirect information from a system to extract secrets. |
| Attack Vector | Network communication interception (e.g., Wi-Fi, Bluetooth). | Physical signals like timing, power consumption, electromagnetic emissions. |
| Common Targets | Data in transit (credentials, messages, transactions). | Cryptographic keys, sensitive computations in devices. |
| Impact | Data theft, message tampering, impersonation. | Key extraction, system compromise without exploiting software flaws. |
| Detection Complexity | Moderate; depends on encryption and network monitoring. | High; often hard to detect due to indirect observation. |
| Prevention Measures | Strong encryption (TLS), mutual authentication, secure channels. | Hardware shielding, noise introduction, side-channel resistant algorithms. |
| Examples | Wi-Fi eavesdropping, SSL stripping attacks. | Power analysis attack, electromagnetic analysis. |
Introduction to Cybersecurity Attacks
Man-in-the-Middle (MitM) attacks intercept and alter communication between two parties without their knowledge, compromising data confidentiality and integrity. Side-channel attacks exploit physical leakages or indirect information, such as timing or power consumption, to extract sensitive data from cryptographic systems. Both attacks highlight critical vulnerabilities in cybersecurity, emphasizing the necessity for robust encryption and system hardening measures.
Defining Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks involve an attacker secretly intercepting and potentially altering communication between two parties without their knowledge, aiming to steal sensitive information or inject malicious content. Unlike side-channel attacks that exploit physical or implementation-based information leakage (such as timing or power consumption), MitM attacks primarily target network communication channels to compromise data privacy and integrity. Effective MitM attack defenses include robust encryption protocols, mutual authentication, and secure key exchange mechanisms.
Understanding Sidechannel Attacks
Sidechannel attacks exploit indirect information leakage from hardware or software implementations, such as timing variations, power consumption, or electromagnetic emissions, to extract sensitive data without directly interacting with cryptographic algorithms. Unlike Man-in-the-Middle attacks, which intercept or alter communication between two parties, sidechannel attacks target physical or operational characteristics of a device. Understanding sidechannel vulnerabilities is critical for securing encryption modules, smartcards, and IoT devices where unintended data emissions can be leveraged for unauthorized access.
Mechanisms of Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks intercept and alter communications between two parties without their knowledge, often employing techniques like IP spoofing, DNS spoofing, or session hijacking to insert the attacker into the data exchange. Attackers exploit vulnerabilities in network protocols or insecure communication channels, enabling them to eavesdrop, inject malicious content, or capture sensitive data such as authentication credentials. Unlike side-channel attacks that extract secrets through physical leakage or indirect channels, MitM attacks primarily rely on manipulating network traffic to compromise confidentiality and integrity during real-time transmissions.
Techniques Used in Sidechannel Attacks
Sidechannel attacks exploit physical leakages such as power consumption, electromagnetic emissions, or timing information to extract secret data from a device without direct access to it. Techniques used include differential power analysis (DPA), which monitors fluctuations in power usage during cryptographic operations, and electromagnetic analysis that captures unintended EM radiation to infer sensitive information. These methods bypass traditional software defenses by targeting hardware vulnerabilities, contrasting with Man-in-the-Middle attacks that intercept and manipulate communication between parties.
Key Differences Between MITM and Sidechannel Attacks
Man-in-the-Middle (MITM) attacks involve intercepting and altering communication between two parties without their knowledge, targeting data integrity and confidentiality in transit. Side-channel attacks exploit indirect information leakage such as timing, power consumption, or electromagnetic emissions from a device to extract cryptographic keys or sensitive data without directly interacting with the communication channel. The key difference lies in MITM attacks actively manipulating or eavesdropping on data flow between endpoints, while side-channel attacks passively gather information from physical hardware characteristics.
Real-World Examples of Both Attack Types
Man-in-the-Middle (MitM) attacks frequently target insecure Wi-Fi networks, as seen in public hotspots where attackers intercept data between users and service providers, exemplified by the infamous 2015 Starbucks Wi-Fi breach. Side-channel attacks exploit hardware vulnerabilities to extract sensitive information, such as the 2018 Tesla Model S key fob exploit, where attackers used electromagnetic analysis to clone car keys. Both attack types highlight the importance of robust encryption and hardware-level security in protecting real-world systems from unauthorized access and data theft.
Detection and Prevention Strategies
Man-in-the-Middle (MitM) attacks require robust encryption protocols such as TLS combined with mutual authentication to detect anomalies in communication channels and prevent unauthorized interception. Side-channel attacks demand hardware-level countermeasures like constant-time algorithms and electromagnetic shielding, alongside continuous monitoring of power consumption and timing variations to identify potential leaks. Implementing intrusion detection systems that analyze traffic patterns and anomaly-based alerts enhances defense against both attack vectors.
Impact on Data Security and Privacy
Man-in-the-Middle (MitM) attacks directly compromise data security by intercepting and altering communications between parties, leading to unauthorized data access and potential identity theft. Sidechannel attacks exploit physical or implementation-based vulnerabilities to extract sensitive information without direct access to encrypted data, threatening both data privacy and cryptographic key integrity. Both attack types undermine confidentiality and trust in secure communications, but MitM attacks typically result in real-time data exposure, whereas sidechannel attacks can silently leak critical information over time.
Future Trends in Mitigating Cyber Attacks
Emerging mitigation strategies for Man-in-the-Middle (MitM) attacks emphasize quantum-resistant cryptography and zero-trust network architectures, aiming to secure communication channels against interception. In contrast, advancements in defending against Side-Channel Attacks prioritize enhanced hardware security modules (HSMs) and machine learning-based anomaly detection to identify and prevent leakage of sensitive information. The integration of artificial intelligence and blockchain technology is expected to play a pivotal role in evolving comprehensive defense mechanisms for both attack vectors.
Man-in-the-Middle Attack Infographic
 libterm.com
libterm.com