LDAP authentication verifies user credentials against a centralized directory service, enhancing security and simplifying access management across multiple systems. It enables seamless user login experiences by connecting to an LDAP server that stores user information and access rights. Explore the rest of the article to understand how LDAP authentication can strengthen Your organization's security framework.
Table of Comparison
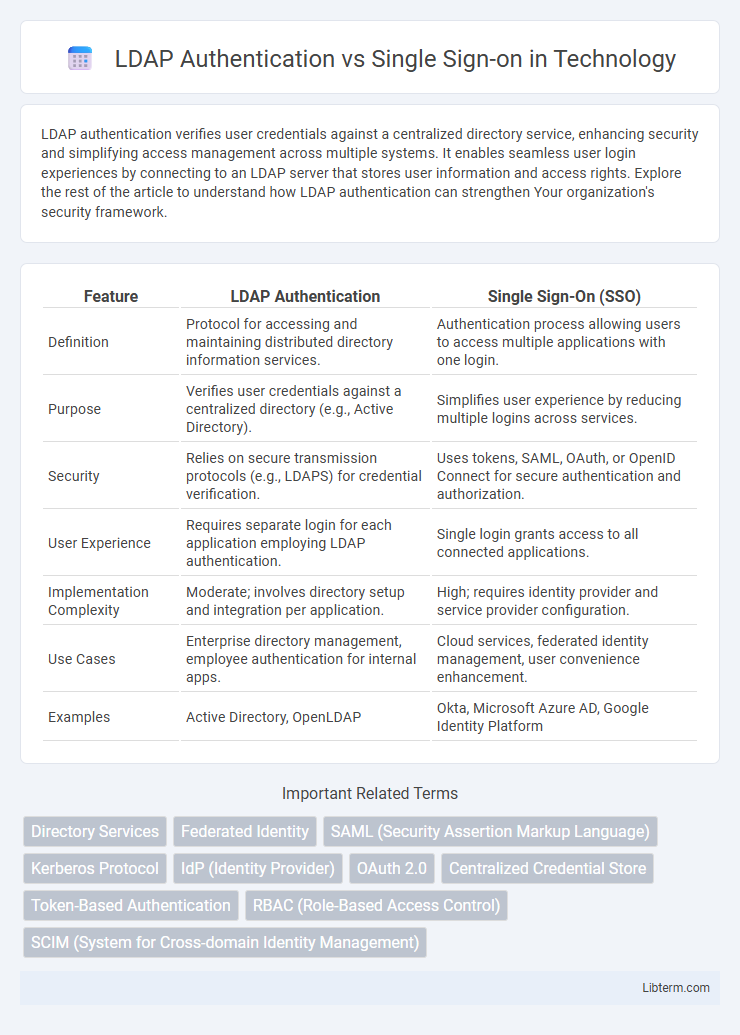
| Feature | LDAP Authentication | Single Sign-On (SSO) |
|---|---|---|
| Definition | Protocol for accessing and maintaining distributed directory information services. | Authentication process allowing users to access multiple applications with one login. |
| Purpose | Verifies user credentials against a centralized directory (e.g., Active Directory). | Simplifies user experience by reducing multiple logins across services. |
| Security | Relies on secure transmission protocols (e.g., LDAPS) for credential verification. | Uses tokens, SAML, OAuth, or OpenID Connect for secure authentication and authorization. |
| User Experience | Requires separate login for each application employing LDAP authentication. | Single login grants access to all connected applications. |
| Implementation Complexity | Moderate; involves directory setup and integration per application. | High; requires identity provider and service provider configuration. |
| Use Cases | Enterprise directory management, employee authentication for internal apps. | Cloud services, federated identity management, user convenience enhancement. |
| Examples | Active Directory, OpenLDAP | Okta, Microsoft Azure AD, Google Identity Platform |
Introduction to LDAP Authentication and Single Sign-On
LDAP authentication leverages the Lightweight Directory Access Protocol to verify user credentials against a centralized directory service, enabling secure access control within enterprise networks. Single Sign-On (SSO) allows users to access multiple applications with one set of login credentials, improving user experience and reducing password fatigue. Both methods streamline authentication processes but differ in scope; LDAP provides a directory-based authentication mechanism, while SSO offers unified access across diverse systems and services.
What is LDAP Authentication?
LDAP Authentication is a protocol used to verify users' credentials against a centralized directory service, such as Microsoft Active Directory or OpenLDAP, ensuring secure access to network resources. It operates by querying the LDAP directory to confirm usernames and passwords, facilitating user management and access control in enterprise environments. LDAP Authentication streamlines identity verification by maintaining a centralized database, reducing password redundancies and enhancing security through standardized authentication processes.
How Single Sign-On (SSO) Works
Single Sign-On (SSO) works by enabling users to access multiple applications or systems with one set of login credentials, leveraging a centralized authentication server. It uses protocols such as SAML, OAuth, or OpenID Connect to exchange authentication tokens between the identity provider (IdP) and service providers, ensuring secure and seamless user verification. This eliminates repeated login prompts, improves user convenience, and enhances security by centralizing credential management and session control.
Key Differences Between LDAP and SSO
LDAP Authentication directly verifies user credentials against a centralized directory like Active Directory, focusing on user identity validation within a specific network. Single Sign-On (SSO) enables users to access multiple applications with one set of login credentials, streamlining user experience and reducing password fatigue. Key differences include LDAP's role in authenticating users at the directory level versus SSO's function in providing unified access across various platforms and services.
Security Considerations: LDAP vs SSO
LDAP authentication directly verifies user credentials against a centralized directory, minimizing exposure by restricting authentication attempts to internal network boundaries, which reduces the risk of credential interception. Single Sign-On (SSO) enhances user convenience but introduces a broader attack surface since compromising the SSO token can grant access to multiple services, necessitating robust token encryption and multi-factor authentication. Both methods require strict implementation of secure communication protocols such as LDAPS for LDAP and OAuth or SAML with strong encryption for SSO to protect authentication data from interception and replay attacks.
User Experience: LDAP Authentication vs SSO
LDAP Authentication requires users to enter credentials separately for each application, often leading to multiple login prompts and fragmented user experiences. Single Sign-On (SSO) streamlines access by enabling users to authenticate once and gain seamless entry to multiple systems, significantly enhancing convenience and reducing password fatigue. SSO improves productivity and security by minimizing login interruptions and centralizing user authentication management.
Integration and Deployment Challenges
LDAP Authentication requires direct integration with directory services, demanding precise configuration and maintenance of user credentials across multiple applications, which can complicate deployment in diverse IT environments. Single Sign-on (SSO) streamlines user access by centralizing authentication, yet its integration involves complex protocols like SAML or OAuth, necessitating compatibility with existing identity providers and risking integration delays. Both methods face challenges in ensuring seamless interoperability, security compliance, and scalability during deployment, with LDAP focusing on directory synchronization and SSO emphasizing token exchange and session management.
Use Cases for LDAP Authentication
LDAP Authentication is commonly used in enterprise environments where centralized user directory services like Microsoft Active Directory or OpenLDAP manage user credentials and access rights. It excels in scenarios requiring granular control over user authorization, such as internal applications, network devices, and legacy systems that depend on directory services for authentication. Organizations implement LDAP Authentication to maintain consistent security policies across multiple platforms while avoiding the complexity of broader Single Sign-on (SSO) solutions.
When to Choose Single Sign-On
Single Sign-On (SSO) is ideal for organizations seeking to enhance user convenience and security across multiple applications by enabling a single authentication process. It reduces password fatigue and mitigates risks associated with password reuse by centralizing credential management through identity providers such as OAuth or SAML. Choose SSO when integrating diverse cloud services and enterprise applications to streamline login workflows and enforce unified access policies.
Conclusion: Choosing the Right Authentication Method
Choosing the right authentication method depends on organizational needs, security requirements, and user convenience. LDAP Authentication provides granular control over user credentials and directory services, ideal for environments requiring direct access management. Single Sign-on (SSO) enhances user experience by allowing seamless access across multiple applications using one set of credentials, reducing password fatigue and streamlining identity management.
LDAP Authentication Infographic
 libterm.com
libterm.com