Public Key Infrastructure (PKI) secures digital communications by enabling encryption and authentication through the use of public and private cryptographic keys. It supports critical functions such as secure email, digital signatures, and virtual private network (VPN) access to protect sensitive data from unauthorized access. Discover how understanding PKI can enhance your cybersecurity strategy by reading the full article.
Table of Comparison
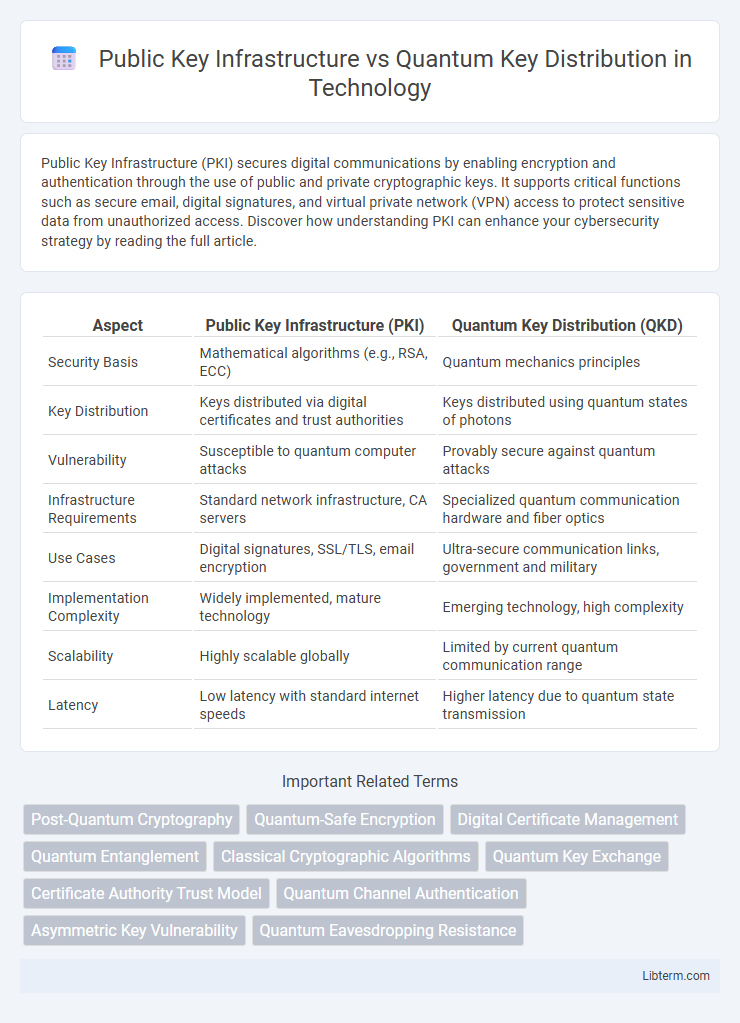
| Aspect | Public Key Infrastructure (PKI) | Quantum Key Distribution (QKD) |
|---|---|---|
| Security Basis | Mathematical algorithms (e.g., RSA, ECC) | Quantum mechanics principles |
| Key Distribution | Keys distributed via digital certificates and trust authorities | Keys distributed using quantum states of photons |
| Vulnerability | Susceptible to quantum computer attacks | Provably secure against quantum attacks |
| Infrastructure Requirements | Standard network infrastructure, CA servers | Specialized quantum communication hardware and fiber optics |
| Use Cases | Digital signatures, SSL/TLS, email encryption | Ultra-secure communication links, government and military |
| Implementation Complexity | Widely implemented, mature technology | Emerging technology, high complexity |
| Scalability | Highly scalable globally | Limited by current quantum communication range |
| Latency | Low latency with standard internet speeds | Higher latency due to quantum state transmission |
Introduction to Secure Communication Technologies
Public Key Infrastructure (PKI) relies on asymmetric cryptography using digital certificates to authenticate users and encrypt data in secure communication systems. Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to enable provably secure key exchange, resistant to computational attacks. Both technologies form the foundation of modern secure communication, with PKI offering scalable trust models and QKD ensuring future-proof confidentiality against quantum computing threats.
Understanding Public Key Infrastructure (PKI)
Public Key Infrastructure (PKI) establishes a framework for secure digital communication by using asymmetric cryptography involving a pair of public and private keys. It relies on trusted Certificate Authorities (CAs) to issue and manage digital certificates, ensuring authentication, data integrity, and non-repudiation. PKI supports secure transactions across the internet but faces challenges against emerging quantum computing threats, prompting exploration of quantum-resistant cryptographic methods.
Fundamentals of Quantum Key Distribution (QKD)
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as superposition and entanglement, to enable two parties to generate and share a secure cryptographic key with the ability to detect any eavesdropping. Unlike Public Key Infrastructure (PKI), which relies on computational hardness assumptions for encryption and digital signatures, QKD provides information-theoretic security guaranteed by the laws of physics. Protocols like BB84 and E91 establish secure key exchange over quantum channels, ensuring unconditional security against any computational attack, even those posed by quantum computers.
Core Principles: PKI vs QKD
Public Key Infrastructure (PKI) relies on asymmetric cryptography using mathematically linked key pairs for secure data exchange and authentication, supported by trusted certificate authorities to validate identities. Quantum Key Distribution (QKD) harnesses the principles of quantum mechanics, specifically quantum entanglement and no-cloning theorem, to enable two parties to generate shared, provably secure encryption keys with detection of any eavesdropping. While PKI's security depends on computational hardness assumptions vulnerable to future quantum attacks, QKD offers information-theoretic security based on fundamental physical laws.
Security Strengths and Weaknesses
Public Key Infrastructure (PKI) relies on asymmetric cryptographic algorithms like RSA and ECC, which provide robust authentication and secure key exchange but are vulnerable to quantum computing attacks due to their reliance on mathematical problems such as factoring and discrete logarithms. Quantum Key Distribution (QKD) offers theoretically unbreakable security by using quantum mechanics principles, enabling detection of eavesdropping and ensuring secure key exchange resistant to both classical and quantum attacks. However, QKD's practical deployment faces challenges such as limited distance, high cost, and the need for specialized hardware, whereas PKI benefits from widespread adoption and scalability despite its potential future cryptographic vulnerabilities.
Implementation Complexity and Costs
Public Key Infrastructure (PKI) involves well-established cryptographic algorithms with widespread support, making its implementation cost-effective and manageable for most organizations due to standardized protocols and existing infrastructure. Quantum Key Distribution (QKD) requires specialized quantum hardware and secure optical communication channels, resulting in significantly higher deployment complexity and initial investment costs. The operational expenses of QKD rise with maintenance of quantum devices and network integrity, whereas PKI benefits from scalable software solutions with lower ongoing costs.
Scalability in Real-World Applications
Public Key Infrastructure (PKI) offers established scalability with extensive support across global networks, relying on asymmetric cryptographic algorithms that efficiently manage large user bases and certificate authorities. Quantum Key Distribution (QKD) faces scalability challenges due to physical hardware requirements like quantum repeaters and limited transmission distances, restricting widespread deployment in metropolitan and long-distance networks. Integration of QKD with classical infrastructure is ongoing, aiming to enhance secure communication while overcoming quantum channel limitations to achieve practical large-scale applications.
Resistance to Quantum Attacks
Public Key Infrastructure (PKI) relies on mathematical problems such as RSA or ECC, which are vulnerable to quantum algorithms like Shor's algorithm, making traditional PKI susceptible to quantum attacks. Quantum Key Distribution (QKD) uses principles of quantum mechanics to securely exchange cryptographic keys, providing inherent resistance to quantum computing threats by detecting eavesdropping through quantum state disturbances. As quantum computers advance, QKD offers a future-proof method for secure key exchange, while PKI requires integration of post-quantum cryptographic algorithms to maintain security.
Future Prospects and Industry Adoption
Public Key Infrastructure (PKI) remains the backbone of digital security with widespread industry adoption relying on trusted certificate authorities and asymmetric cryptography. Quantum Key Distribution (QKD) offers unprecedented security through quantum mechanics, promising immunity to computational attacks from future quantum computers. Despite current deployment challenges, QKD's integration into critical sectors like finance and government signals a transformative shift toward quantum-resilient communication in the coming decades.
Choosing Between PKI and QKD
Choosing between Public Key Infrastructure (PKI) and Quantum Key Distribution (QKD) depends on the specific security requirements and technological environment of an organization. PKI offers widely adopted, scalable cryptographic solutions based on asymmetric encryption algorithms such as RSA and ECC, which are effective for digital certificates and secure communications in classical computing contexts. In contrast, QKD leverages principles of quantum mechanics to provide theoretically unbreakable key exchange, making it ideal for environments requiring long-term data confidentiality against future quantum computing threats but currently facing limitations in infrastructure and deployment costs.
Public Key Infrastructure Infographic
 libterm.com
libterm.com