Group Key Exchange protocols enable multiple users to securely establish a shared secret key for encrypted communication in a network. These protocols focus on scalability, efficiency, and resilience against attacks to ensure confidentiality and integrity among group members. Discover how these mechanisms enhance your group security by reading the rest of the article.
Table of Comparison
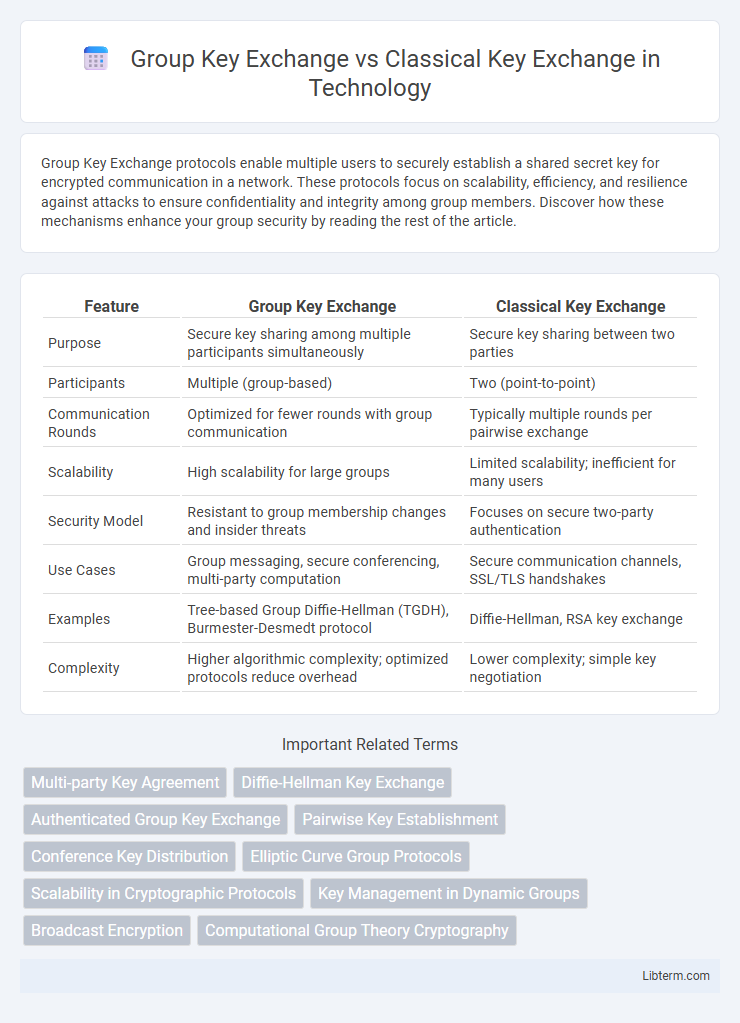
| Feature | Group Key Exchange | Classical Key Exchange |
|---|---|---|
| Purpose | Secure key sharing among multiple participants simultaneously | Secure key sharing between two parties |
| Participants | Multiple (group-based) | Two (point-to-point) |
| Communication Rounds | Optimized for fewer rounds with group communication | Typically multiple rounds per pairwise exchange |
| Scalability | High scalability for large groups | Limited scalability; inefficient for many users |
| Security Model | Resistant to group membership changes and insider threats | Focuses on secure two-party authentication |
| Use Cases | Group messaging, secure conferencing, multi-party computation | Secure communication channels, SSL/TLS handshakes |
| Examples | Tree-based Group Diffie-Hellman (TGDH), Burmester-Desmedt protocol | Diffie-Hellman, RSA key exchange |
| Complexity | Higher algorithmic complexity; optimized protocols reduce overhead | Lower complexity; simple key negotiation |
Introduction to Key Exchange Protocols
Key exchange protocols establish a secure method for parties to share cryptographic keys, essential for encrypted communication. Classical key exchange, such as Diffie-Hellman, typically involves two parties establishing a shared secret over an insecure channel. Group key exchange protocols extend this concept to multiple participants, enabling secure key sharing within a group for applications like group messaging or collaborative environments.
Understanding Classical Key Exchange Methods
Classical key exchange methods, such as Diffie-Hellman and RSA, rely on secure pairwise communication channels to establish shared secrets between two parties. These protocols use mathematical principles like discrete logarithms or factorization to generate cryptographic keys without directly transmitting the keys themselves. Understanding classical key exchange is essential for recognizing the challenges in scaling secure communication to multiple participants, which group key exchange protocols aim to address.
What is Group Key Exchange?
Group Key Exchange enables multiple participants to collaboratively generate a shared cryptographic key, enhancing secure communications within a group setting. Unlike Classical Key Exchange, which establishes a secret key between two parties, Group Key Exchange protocols optimize scalability and efficiency for multi-user interactions. This method is essential for applications such as secure conferencing, collaborative workspaces, and decentralized networks.
Core Differences Between Classical and Group Key Exchange
Classical Key Exchange protocols, such as Diffie-Hellman, establish a shared secret between two parties, while Group Key Exchange protocols enable multiple participants to derive a common cryptographic key simultaneously. Group Key Exchange must efficiently handle dynamic membership changes, ensuring forward and backward secrecy for the entire group, a complexity absent in classical two-party exchanges. The core difference lies in scalability and collaboration, with group protocols designed to maintain security properties amid multiple users rather than a single key pair.
Security Considerations in Both Approaches
Group Key Exchange protocols enhance security by enabling a dynamic, scalable approach to establishing a shared secret among multiple participants, reducing risks of key compromise through collective authentication and forward secrecy mechanisms. Classical Key Exchange methods, such as Diffie-Hellman, primarily secure pairwise communications but face challenges in scalability and increased vulnerability to impersonation attacks in multi-party settings. Evaluating both approaches highlights that Group Key Exchange provides stronger resilience against insider threats and better privacy preservation in collaborative environments compared to traditional pairwise key agreements.
Scalability and Performance Analysis
Group Key Exchange protocols significantly enhance scalability by enabling secure key establishment among multiple participants simultaneously, reducing the communication rounds compared to Classical Key Exchange which typically involves pairwise key agreements. Performance analysis shows that Group Key Exchange protocols optimize computation and communication overhead in large groups, minimizing latency and resource consumption. Classical Key Exchange methods face exponential growth in operations and message exchanges as the number of participants increases, resulting in reduced efficiency for extensive networks.
Typical Use Cases for Classical vs Group Key Exchange
Classical key exchange protocols, such as Diffie-Hellman or RSA-based exchanges, are typically used for secure communication between two parties in scenarios like secure web browsing, email encryption, and VPN connections. Group key exchange protocols are designed for environments requiring secure multicast or group communication, including collaborative workspaces, video conferencing, and distributed sensor networks. These protocols ensure that all group members share a common secret key, protecting group data integrity and confidentiality simultaneously.
Implementation Challenges and Solutions
Group Key Exchange protocols face implementation challenges such as ensuring scalability, managing dynamic group membership, and preserving forward secrecy, which are less critical in Classical Key Exchange schemes focused on two-party communication. Solutions include employing contributory key agreement protocols, leveraging efficient rekeying mechanisms, and utilizing robust multicast cryptographic primitives to address these issues. Advances in decentralized group key management and on-demand key distribution frameworks further enhance security and performance in multi-party environments.
Future Trends in Key Exchange Technologies
Future trends in key exchange technologies emphasize enhanced scalability and security for Group Key Exchange protocols, leveraging advancements in post-quantum cryptography to resist emerging quantum threats. Classical Key Exchange methods, primarily based on Diffie-Hellman and RSA, face vulnerabilities from quantum computing, prompting a shift toward lattice-based and hash-based schemes within group settings. Research focuses on optimizing efficiency and minimizing communication overhead in dynamic groups, integrating blockchain and decentralized mechanisms to achieve robust and forward-secure key distribution.
Conclusion: Choosing the Right Key Exchange Method
Choosing the right key exchange method depends on the specific application requirements, such as the number of participants and security needs. Group Key Exchange protocols are optimized for multi-party communication, providing efficiency and scalability compared to Classical Key Exchange, which is better suited for two-party interactions. Evaluating factors like computational overhead, latency, and security guarantees ensures the selection of a key exchange method that balances performance and protection.
Group Key Exchange Infographic
 libterm.com
libterm.com