Phishing attacks exploit deceptive emails and websites to steal your personal information such as passwords, credit card numbers, and social security details. These cyber threats often appear as legitimate communications from trusted sources, making vigilance essential in recognizing suspicious links or requests. Learn how to protect your data and spot phishing scams by reading the rest of this article.
Table of Comparison
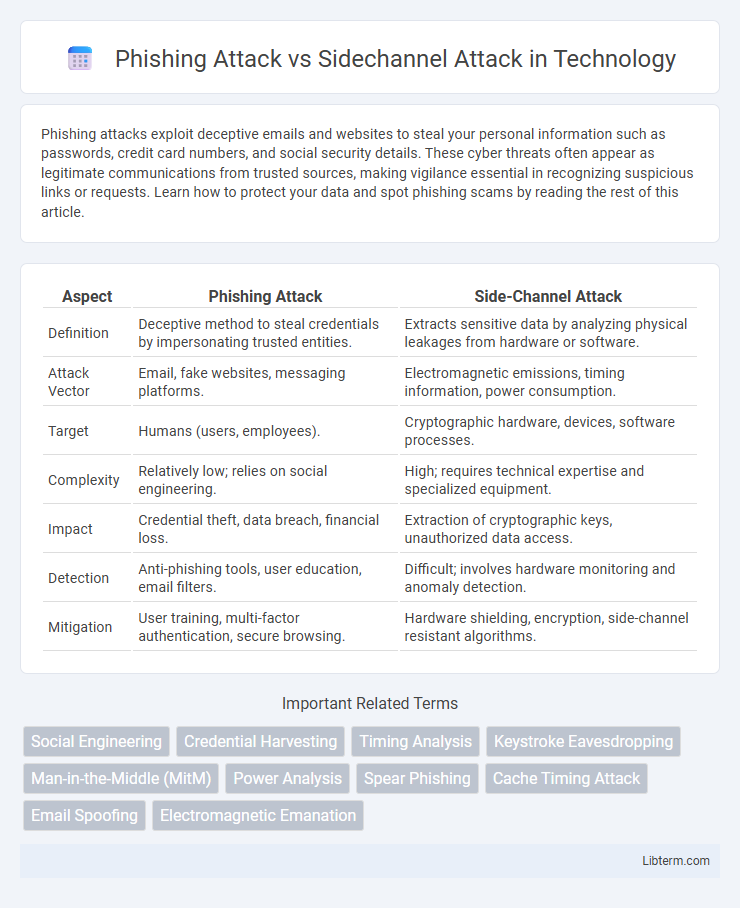
| Aspect | Phishing Attack | Side-Channel Attack |
|---|---|---|
| Definition | Deceptive method to steal credentials by impersonating trusted entities. | Extracts sensitive data by analyzing physical leakages from hardware or software. |
| Attack Vector | Email, fake websites, messaging platforms. | Electromagnetic emissions, timing information, power consumption. |
| Target | Humans (users, employees). | Cryptographic hardware, devices, software processes. |
| Complexity | Relatively low; relies on social engineering. | High; requires technical expertise and specialized equipment. |
| Impact | Credential theft, data breach, financial loss. | Extraction of cryptographic keys, unauthorized data access. |
| Detection | Anti-phishing tools, user education, email filters. | Difficult; involves hardware monitoring and anomaly detection. |
| Mitigation | User training, multi-factor authentication, secure browsing. | Hardware shielding, encryption, side-channel resistant algorithms. |
Understanding Phishing Attacks
Phishing attacks exploit social engineering tactics to deceive individuals into revealing sensitive information like passwords, credit card numbers, or login credentials by masquerading as trustworthy entities through emails, fake websites, or messages. These attacks rely heavily on human error and the inability to detect fraudulent communications rather than technological vulnerabilities. Effective prevention includes user education, multi-factor authentication, and advanced email filtering to block malicious content and links.
What Are Sidechannel Attacks?
Sidechannel attacks exploit indirect information leakage from physical implementations of cryptographic systems, such as timing, power consumption, electromagnetic emissions, or acoustic signals, to extract secret data without breaking the encryption algorithm itself. Unlike phishing attacks that rely on social engineering to deceive users into revealing sensitive information, sidechannel attacks target hardware vulnerabilities and the physical characteristics of devices to bypass traditional security measures. These attacks are critical in high-security environments where attackers aim to retrieve cryptographic keys or confidential information stealthily.
Key Differences Between Phishing and Sidechannel Attacks
Phishing attacks primarily exploit social engineering techniques to deceive individuals into revealing sensitive information such as passwords or credit card numbers by impersonating trustworthy entities. Sidechannel attacks, on the other hand, leverage indirect information leakage from hardware devices, such as timing information, power consumption, or electromagnetic emissions, to extract cryptographic keys without direct interaction with the user. The key difference lies in the attack vector: phishing manipulates human behavior, whereas sidechannel attacks exploit physical vulnerabilities in computing systems.
Common Techniques Used in Phishing
Phishing attacks commonly use deceptive techniques such as email spoofing, fake websites, and social engineering to trick victims into revealing sensitive information like passwords or credit card numbers. Attackers often employ spear phishing, which targets specific individuals with personalized messages to increase credibility and effectiveness. These methods exploit human trust and lack of awareness, contrasting with side-channel attacks that typically rely on hardware or software vulnerabilities to extract data.
Sidechannel Attack Methods and Examples
Sidechannel attacks exploit indirect information leakage such as timing, power consumption, electromagnetic emissions, or acoustic signals to extract sensitive data from cryptographic devices or secure systems without directly attacking the algorithms. Common examples of sidechannel attack methods include timing attacks that measure the time taken for cryptographic operations, power analysis attacks like Differential Power Analysis (DPA) that monitor fluctuations in power usage, and electromagnetic analysis that captures emissions during processing. These attacks pose significant threats to hardware security by revealing secret keys, passwords, or other confidential information through non-invasive means.
Identifying Signs of a Phishing Attempt
Phishing attacks often involve deceptive emails or messages that urge recipients to click on suspicious links or provide personal information, with signs including urgent language, mismatched URLs, and unexpected requests from seemingly trusted sources. Side-channel attacks, in contrast, exploit physical or informational leakage such as timing information, power consumption, or electromagnetic emissions, making them less identifiable through direct communication cues. Recognizing phishing attempts requires vigilance for anomalies like spelling errors, inconsistent sender addresses, and unsolicited attachments to prevent credential theft or malware infection.
Indicators and Detection of Sidechannel Attacks
Sidechannel attacks exploit physical leakages such as timing, power consumption, or electromagnetic emissions to extract sensitive data, with indicators including unusual hardware behavior or abnormal signal patterns. Detection techniques involve monitoring for irregular power signatures, timing anomalies, and electromagnetic sidebands using specialized sensors and machine learning algorithms. Robust detection frameworks combine hardware instrumentation with real-time data analysis to identify and mitigate sidechannel threats effectively.
Impact and Consequences of Phishing vs Sidechannel Attacks
Phishing attacks primarily result in unauthorized access to sensitive personal or financial information, leading to identity theft, financial loss, and compromised user accounts. Sidechannel attacks exploit hardware vulnerabilities to extract cryptographic keys or sensitive data without detection, causing severe breaches in data confidentiality and integrity. While phishing often targets individuals through social engineering, sidechannel attacks challenge system security at the hardware level, potentially affecting entire networks or devices.
Prevention Strategies for Both Attack Types
Phishing attack prevention strategies emphasize user education, robust email filtering, and multi-factor authentication to reduce the risk of credential theft and impersonation. Side-channel attack defenses include implementing hardware and software countermeasures such as constant-time algorithms, noise injection, and secure cryptographic modules to protect sensitive data leakage. Both attack types benefit from continuous monitoring and updating security protocols to adapt to evolving threat vectors.
Strengthening Cybersecurity Against Phishing and Sidechannel Attacks
Phishing attacks exploit social engineering to deceive users into revealing sensitive information, while sidechannel attacks target hardware vulnerabilities to extract confidential data without direct access. Strengthening cybersecurity involves implementing multi-factor authentication, email filtering, and continuous user education to mitigate phishing risks, alongside deploying hardware security modules (HSMs), constant monitoring, and secure cryptographic protocols to defend against sidechannel exploits. Combining these strategies enhances overall resilience by addressing both human and technical attack vectors effectively.
Phishing Attack Infographic
 libterm.com
libterm.com