Password-Authenticated Key Exchange (PAKE) protocols enable secure cryptographic key exchange using a shared password, protecting against eavesdropping and man-in-the-middle attacks without transmitting the password itself. These protocols enhance authentication and confidentiality in environments with limited trust, making them essential for secure online communications and password-based systems. Discover how PAKE can safeguard your digital interactions by reading the rest of the article.
Table of Comparison
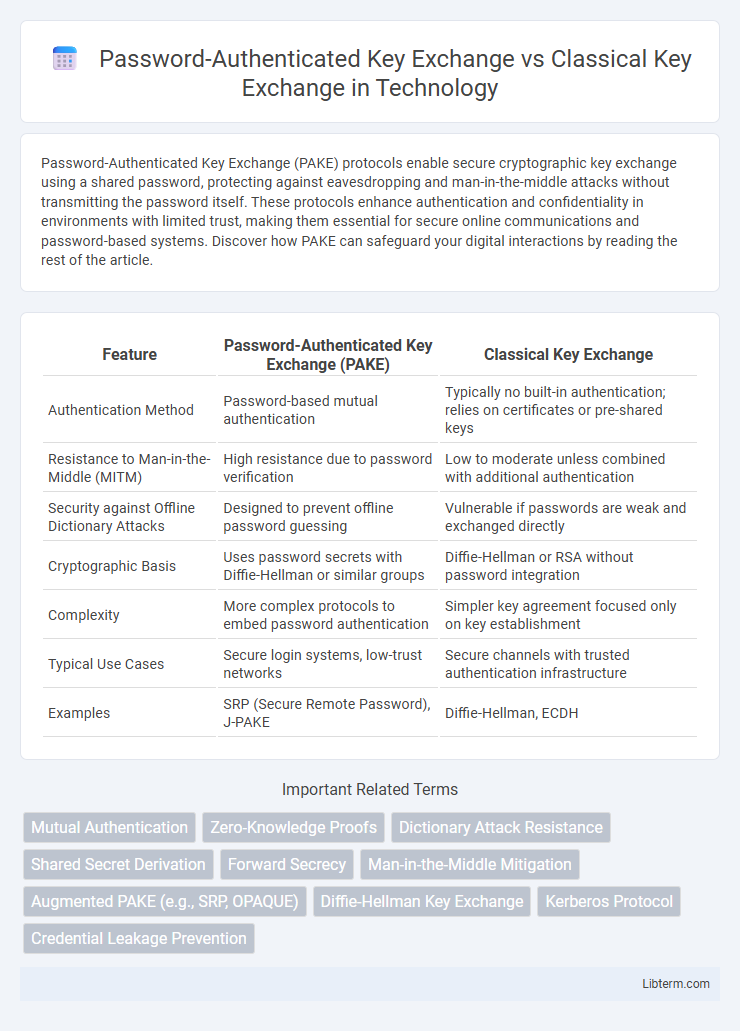
| Feature | Password-Authenticated Key Exchange (PAKE) | Classical Key Exchange |
|---|---|---|
| Authentication Method | Password-based mutual authentication | Typically no built-in authentication; relies on certificates or pre-shared keys |
| Resistance to Man-in-the-Middle (MITM) | High resistance due to password verification | Low to moderate unless combined with additional authentication |
| Security against Offline Dictionary Attacks | Designed to prevent offline password guessing | Vulnerable if passwords are weak and exchanged directly |
| Cryptographic Basis | Uses password secrets with Diffie-Hellman or similar groups | Diffie-Hellman or RSA without password integration |
| Complexity | More complex protocols to embed password authentication | Simpler key agreement focused only on key establishment |
| Typical Use Cases | Secure login systems, low-trust networks | Secure channels with trusted authentication infrastructure |
| Examples | SRP (Secure Remote Password), J-PAKE | Diffie-Hellman, ECDH |
Introduction to Key Exchange Protocols
Password-Authenticated Key Exchange (PAKE) protocols enhance classical key exchange methods by integrating user passwords to authenticate parties securely during the key agreement process. Unlike traditional protocols like Diffie-Hellman, which are vulnerable to man-in-the-middle attacks without prior authentication, PAKE ensures that only users sharing the correct password can establish the session key, providing resistance to offline dictionary attacks. These protocols play a critical role in secure communication systems by combining confidentiality and authentication seamlessly.
Overview of Classical Key Exchange Methods
Classical key exchange methods primarily include Diffie-Hellman and RSA algorithms, which facilitate secure sharing of cryptographic keys over insecure channels. These methods rely on computational hardness assumptions like discrete logarithms and integer factorization, making them vulnerable to attacks if the underlying mathematical problems are solved efficiently. Unlike Password-Authenticated Key Exchange (PAKE), classical methods do not incorporate user passwords for authentication, potentially exposing them to man-in-the-middle attacks without additional authentication mechanisms.
Understanding Password-Authenticated Key Exchange (PAKE)
Password-Authenticated Key Exchange (PAKE) protocols enable two parties to establish a secure cryptographic key based on a shared password without exposing the password itself, effectively mitigating risks of interception and offline dictionary attacks. Unlike classical key exchange methods that rely solely on public-key cryptography, PAKE combines password verification with key exchange, ensuring mutual authentication even over insecure channels. This approach enhances security by preventing common vulnerabilities associated with weak or reused passwords in traditional key exchange protocols.
Security Fundamentals: PAKE vs Classical Key Exchange
Password-Authenticated Key Exchange (PAKE) protocols enhance security fundamentals by integrating password verification with key exchange, preventing offline dictionary attacks even if an adversary intercepts communication. Classical key exchange mechanisms, such as Diffie-Hellman, typically lack inherent authentication, making them vulnerable to man-in-the-middle attacks without supplementary authentication methods. PAKE ensures mutual authentication and secure key establishment simultaneously, significantly strengthening resistance against common cryptographic threats compared to classical key exchanges.
Authentication Mechanisms Compared
Password-Authenticated Key Exchange (PAKE) protocols integrate user passwords directly into the key exchange process, ensuring mutual authentication based on shared secrets without exposing passwords to interception. Classical Key Exchange methods, such as Diffie-Hellman, typically rely on digital certificates or pre-shared keys for authentication, which can be vulnerable if certificates are compromised or pre-shared keys are weak. PAKE strengthens security by resisting man-in-the-middle attacks and providing explicit authentication while enabling secure session key generation even when using low-entropy passwords.
Resistance to Attacks: Brute-force and Man-in-the-Middle
Password-Authenticated Key Exchange (PAKE) protocols enhance resistance against brute-force attacks by integrating password verification directly into the cryptographic handshake, limiting an attacker's ability to test multiple passwords without detection. In contrast, classical key exchange methods like Diffie-Hellman lack inherent password verification and are more vulnerable to dictionary attacks if passwords are weakly managed. PAKE protocols also provide robust defense against man-in-the-middle attacks by requiring mutual authentication based on shared secrets, whereas classical key exchanges often require additional authentication mechanisms to prevent interception and impersonation.
Usability and User Experience Considerations
Password-Authenticated Key Exchange (PAKE) improves usability by enabling secure key agreement based solely on user-chosen passwords, eliminating the need for complex cryptographic key management common in Classical Key Exchange methods. PAKE protocols reduce user errors and enhance user experience by simplifying authentication without requiring additional hardware or trusted third parties, unlike classical schemes that often rely on PKI infrastructure. This focus on human-friendly interaction makes PAKE particularly suitable for environments where ease of use and security must coexist seamlessly.
Real-World Applications and Use Cases
Password-Authenticated Key Exchange (PAKE) protocols enhance security in real-world applications by enabling secure key establishment using only human-memorable passwords, making them ideal for user authentication in web services, IoT devices, and secure messaging platforms. Classical Key Exchange methods like Diffie-Hellman excel in scenarios requiring high computational efficiency and are common in VPNs, SSL/TLS protocols, and encrypted cloud communications without relying on passwords. PAKE's resistance to offline dictionary attacks and man-in-the-middle attacks makes it particularly valuable where password-based authentication is necessary, while classical key exchanges are preferred in environments prioritizing performance and established cryptographic infrastructure.
Implementation Challenges and Performance
Password-Authenticated Key Exchange (PAKE) presents unique implementation challenges including the need to securely handle weak or low-entropy passwords without exposing them to offline dictionary attacks, which complicates protocol design compared to Classical Key Exchange methods like Diffie-Hellman. Performance-wise, PAKE protocols often incur higher computational and communication overhead due to additional cryptographic primitives aimed at securely validating passwords, whereas Classical Key Exchanges benefit from more streamlined operations focused solely on key agreement. Ensuring resistance against active attacks such as man-in-the-middle while maintaining efficiency in PAKE protocols requires careful balancing of security parameters, often resulting in slower key establishment relative to traditional key exchanges.
Future Trends in Key Exchange Protocols
Password-Authenticated Key Exchange (PAKE) protocols enhance security by integrating user passwords directly into the cryptographic process, reducing vulnerability to offline dictionary attacks common in classical key exchange methods like Diffie-Hellman. Future trends emphasize zero-knowledge proofs and post-quantum cryptography to ensure resilience against emerging quantum threats, while maintaining user-friendly authentication. Research continues to prioritize seamless integration with multi-factor authentication and blockchain technologies, aiming to balance strong security with practical deployment in distributed systems.
Password-Authenticated Key Exchange Infographic
 libterm.com
libterm.com