Accessibility by design ensures your products and services are usable by everyone, including people with disabilities, by integrating inclusive features from the very beginning of development. This proactive approach not only improves user experience but also broadens your audience reach and complies with legal standards. Discover how implementing accessibility by design can transform your projects by reading the full article.
Table of Comparison
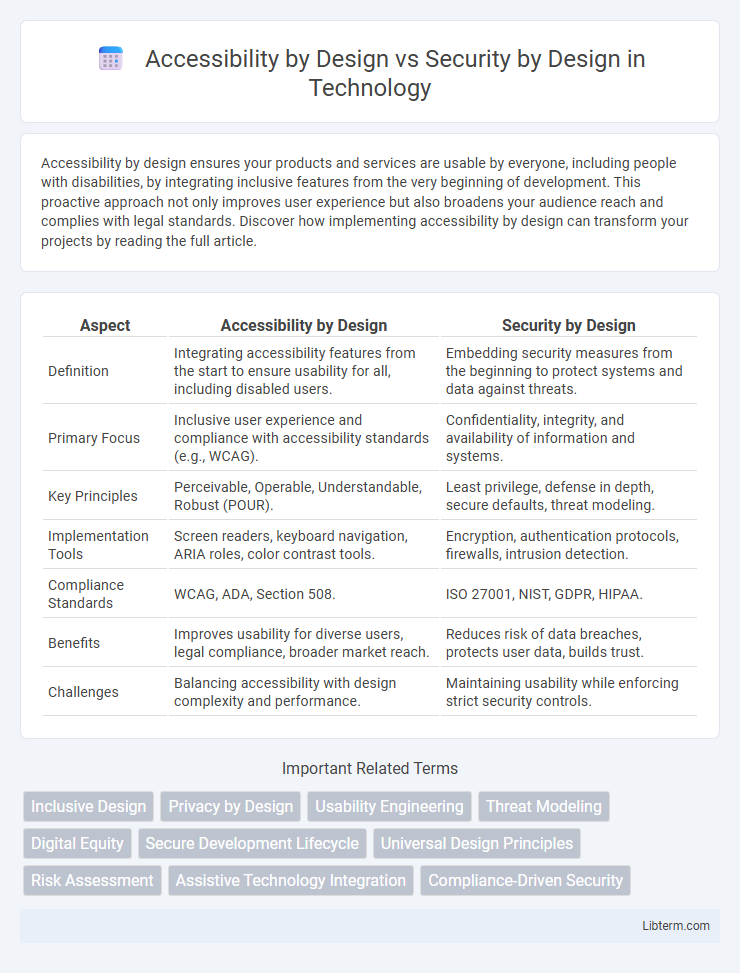
| Aspect | Accessibility by Design | Security by Design |
|---|---|---|
| Definition | Integrating accessibility features from the start to ensure usability for all, including disabled users. | Embedding security measures from the beginning to protect systems and data against threats. |
| Primary Focus | Inclusive user experience and compliance with accessibility standards (e.g., WCAG). | Confidentiality, integrity, and availability of information and systems. |
| Key Principles | Perceivable, Operable, Understandable, Robust (POUR). | Least privilege, defense in depth, secure defaults, threat modeling. |
| Implementation Tools | Screen readers, keyboard navigation, ARIA roles, color contrast tools. | Encryption, authentication protocols, firewalls, intrusion detection. |
| Compliance Standards | WCAG, ADA, Section 508. | ISO 27001, NIST, GDPR, HIPAA. |
| Benefits | Improves usability for diverse users, legal compliance, broader market reach. | Reduces risk of data breaches, protects user data, builds trust. |
| Challenges | Balancing accessibility with design complexity and performance. | Maintaining usability while enforcing strict security controls. |
Introduction: Defining Accessibility by Design and Security by Design
Accessibility by Design ensures digital products are inherently usable by individuals with disabilities through inclusive interfaces and assistive technologies. Security by Design integrates robust protection mechanisms into systems from the outset, safeguarding data and preventing unauthorized access. Both concepts prioritize proactive strategies for building resilient, user-centered digital environments.
Historical Context: Evolution of Accessibility and Security Paradigms
The historical context of Accessibility by Design traces back to early disability rights movements and landmark legislation like the Americans with Disabilities Act (ADA) of 1990, which shifted focus towards inclusive digital and physical environments. Security by Design, rooted in the development of computer science and cryptography during the Cold War era, evolved through frameworks such as the CIA triad (Confidentiality, Integrity, Availability) that prioritize proactive threat mitigation in system architecture. Both paradigms reflect distinct but converging evolutions driven by societal needs and technological advancements emphasizing proactive integration rather than reactive fixes.
Core Principles of Accessibility by Design
Accessibility by Design prioritizes inclusivity by embedding principles such as perceivability, operability, understandability, and robustness into every stage of product development. These core principles ensure that digital interfaces accommodate diverse user needs, including those with disabilities, by providing alternative text, keyboard navigation, clear instructions, and compatibility with assistive technologies. Emphasizing accessibility from the outset reduces barriers, enhances user experience, and promotes equal access for all.
Core Principles of Security by Design
Security by Design emphasizes embedding robust security measures into the development process from the outset, focusing on principles such as least privilege, defense in depth, and secure defaults to minimize vulnerabilities. Core principles include ensuring confidentiality, integrity, and availability of data while implementing rigorous authentication, authorization, and audit controls. This proactive approach contrasts Accessibility by Design, which prioritizes usability and inclusivity, ensuring products are accessible to users with diverse needs without compromising security fundamentals.
Points of Intersection: Where Accessibility and Security Overlap
Accessibility by Design and Security by Design intersect in creating systems that are both usable and protected, ensuring that security measures do not impede access for users with disabilities. Implementing multi-factor authentication with accessible options, such as biometric or assistive technology compatibility, exemplifies this overlap. Balancing user experience and protection requires integrating inclusive security protocols that accommodate diverse needs without compromising system robustness.
Conflicts and Trade-offs Between Accessibility and Security
Accessibility by Design aims to create inclusive interfaces that accommodate diverse users, including those with disabilities, while Security by Design prioritizes robust protections against cyber threats and unauthorized access. Conflicts arise when accessibility features, such as simplified authentication or broad permissions, potentially reduce security measures, increasing vulnerability to attacks. Trade-offs require careful balance to ensure security protocols do not exclude users or create barriers, demanding adaptive solutions that integrate multi-factor authentication with accessible options like biometric recognition and screen reader compatibility.
Case Studies: Successes and Failures in Accessibility and Security Integration
Case studies in Accessibility by Design demonstrate increased user engagement and compliance with regulations, exemplified by companies like Microsoft improving screen reader compatibility in Windows. Conversely, Security by Design successes include Airbnb's proactive encryption and multi-factor authentication, significantly reducing data breaches. Failures arise when firms prioritize security over accessibility, such as Uber's initial inaccessible app updates causing user exclusion and legal challenges.
Industry Standards and Regulatory Requirements
Industry standards such as WCAG 2.1 and Section 508 emphasize Accessibility by Design to ensure digital inclusivity for users with disabilities, mandating compliance through specific technical criteria and testing protocols. Security by Design follows frameworks like NIST SP 800-53 and ISO/IEC 27001, embedding risk management and data protection measures throughout the development lifecycle to meet regulatory requirements such as GDPR and HIPAA. Both approaches require integration early in product development to align with legal obligations and industry best practices, minimizing risks related to accessibility lawsuits and cybersecurity breaches.
Best Practices for Balancing Accessibility and Security
Balancing Accessibility by Design and Security by Design requires implementing best practices such as adopting inclusive authentication methods like biometric verification and multi-factor authentication to enhance security without compromising user access. Ensuring compliance with accessibility standards like WCAG alongside security frameworks such as OWASP helps create systems that are both secure and user-friendly. Continuous testing and user feedback integration are essential to identify and address potential conflicts between accessibility features and security measures.
Future Trends: Toward Inclusive and Secure Digital Environments
Accessibility by Design integrates universal usability principles from the outset, ensuring digital products meet diverse user needs, while Security by Design embeds robust protection mechanisms to safeguard data and privacy proactively. Future trends highlight the convergence of these approaches, promoting inclusive yet resilient digital environments powered by AI-driven adaptive interfaces and zero-trust security frameworks. Emphasizing interoperability, real-time threat detection, and user-centered accessibility, the next wave of digital innovation fosters seamless interaction for all users without compromising security integrity.
Accessibility by Design Infographic
 libterm.com
libterm.com