A Web Application Firewall (WAF) protects your online platforms by monitoring and filtering HTTP traffic to prevent cyber threats such as SQL injections, cross-site scripting, and other exploits. By analyzing incoming requests, a WAF ensures your web applications remain secure without compromising performance. Explore the rest of the article to learn how a WAF can safeguard your digital presence effectively.
Table of Comparison
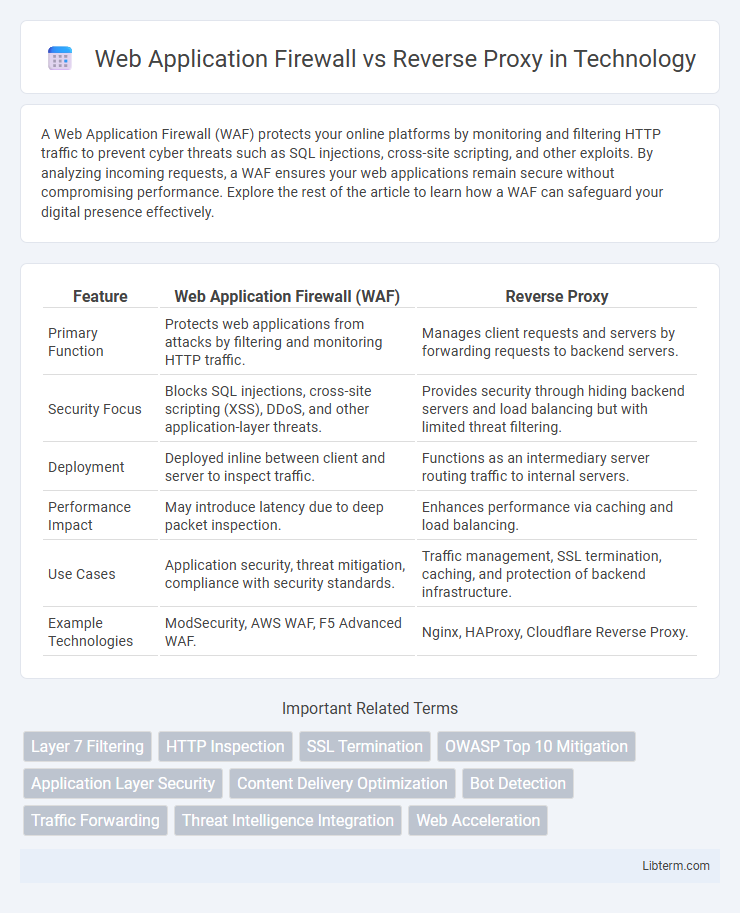
| Feature | Web Application Firewall (WAF) | Reverse Proxy |
|---|---|---|
| Primary Function | Protects web applications from attacks by filtering and monitoring HTTP traffic. | Manages client requests and servers by forwarding requests to backend servers. |
| Security Focus | Blocks SQL injections, cross-site scripting (XSS), DDoS, and other application-layer threats. | Provides security through hiding backend servers and load balancing but with limited threat filtering. |
| Deployment | Deployed inline between client and server to inspect traffic. | Functions as an intermediary server routing traffic to internal servers. |
| Performance Impact | May introduce latency due to deep packet inspection. | Enhances performance via caching and load balancing. |
| Use Cases | Application security, threat mitigation, compliance with security standards. | Traffic management, SSL termination, caching, and protection of backend infrastructure. |
| Example Technologies | ModSecurity, AWS WAF, F5 Advanced WAF. | Nginx, HAProxy, Cloudflare Reverse Proxy. |
Introduction to Web Application Firewall and Reverse Proxy
A Web Application Firewall (WAF) protects web applications by filtering and monitoring HTTP traffic between the internet and the application to block malicious requests such as SQL injection and cross-site scripting. A Reverse Proxy acts as an intermediary server that forwards client requests to one or more backend servers, often enhancing security, load balancing, and caching. While both improve web security and performance, a WAF specifically targets application-level threats, whereas a Reverse Proxy manages traffic routing and resource distribution.
Core Functions: WAF vs Reverse Proxy
A Web Application Firewall (WAF) primarily protects web applications by filtering and monitoring HTTP traffic to block malicious requests such as SQL injection, cross-site scripting, and other application-layer attacks. In contrast, a Reverse Proxy serves as an intermediary between clients and servers, managing incoming traffic to improve load balancing, caching, SSL termination, and hiding the backend server's identity. While both technologies enhance security, WAF focuses on application-level protection by analyzing request data, whereas Reverse Proxy emphasizes traffic management and performance optimization.
How Web Application Firewalls Work
Web Application Firewalls (WAFs) inspect incoming HTTP/HTTPS traffic by monitoring and filtering requests to protect web applications from common threats such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. By analyzing request headers, payloads, and URLs in real-time, WAFs enforce security policies and block malicious activities before they reach the application server. Unlike reverse proxies that primarily handle load balancing and request routing, WAFs provide specialized threat detection and attack mitigation tailored to web application security.
How Reverse Proxies Operate
Reverse proxies function as intermediaries between client requests and backend servers, managing traffic by forwarding client requests to appropriate servers based on load balancing algorithms or security rules. They enhance performance by caching content and compressing requests while masking the identity and characteristics of backend servers to improve security. Unlike Web Application Firewalls, which primarily filter and monitor HTTP traffic to detect and block malicious activities, reverse proxies provide broader control over traffic routing, SSL termination, and efficient resource allocation.
Key Differences Between WAF and Reverse Proxy
A Web Application Firewall (WAF) primarily filters, monitors, and blocks HTTP traffic to and from a web application to protect against attacks like SQL injection and cross-site scripting. A Reverse Proxy, on the other hand, serves as an intermediary for client requests by forwarding them to backend servers, enhancing security, load balancing, and caching. Unlike Reverse Proxies that manage traffic distribution, WAFs specialize in inspecting and filtering malicious payloads within web traffic.
Security Benefits: WAF vs Reverse Proxy
Web Application Firewalls (WAFs) provide specialized security by filtering, monitoring, and blocking malicious HTTP/HTTPS traffic to protect web applications from attacks like SQL injection and cross-site scripting. Reverse proxies enhance security by masking backend servers' IP addresses and distributing traffic, reducing the risk of direct attacks and improving load balancing. While WAFs offer granular protection against specific web vulnerabilities, reverse proxies primarily serve as a security gateway, improving anonymity and traffic management.
Performance and Load Balancing Considerations
Web Application Firewalls (WAFs) primarily focus on filtering and monitoring HTTP traffic to protect web applications, which can introduce latency due to deep packet inspection, impacting performance under high loads. Reverse proxies distribute client requests across multiple servers to enhance load balancing and improve response times by optimizing resource utilization and reducing server overload. Combining WAFs with reverse proxies can provide robust security and efficient load balancing, but careful tuning is required to minimize performance degradation and maintain optimal throughput.
Use Cases for Web Application Firewalls
Web Application Firewalls (WAFs) protect web applications by filtering and monitoring HTTP traffic to block malicious attacks such as SQL injection, cross-site scripting (XSS), and DDoS attempts, making them essential for securing sensitive data and maintaining compliance with regulations like PCI DSS. Unlike reverse proxies that primarily handle traffic routing and load balancing, WAFs offer granular control over application-layer threats and are deployed in environments requiring strong protection against zero-day vulnerabilities and bot attacks. Use cases for WAFs include safeguarding e-commerce platforms, financial services, and healthcare applications where preventing data breaches and ensuring uninterrupted service are critical.
Use Cases for Reverse Proxies
Reverse proxies serve as intermediaries between clients and backend servers, enhancing security by masking server details and distributing incoming traffic efficiently. They optimize load balancing, improve fault tolerance, and enable caching to reduce latency and server load. Common use cases include securing microservices architectures, providing SSL termination, and facilitating seamless content delivery across multiple servers.
Choosing the Right Solution for Your Web Application
Choosing the right solution between a Web Application Firewall (WAF) and a Reverse Proxy depends on your web application's security and performance needs. A WAF primarily protects against common web threats like SQL injection and cross-site scripting by analyzing HTTP requests, while a Reverse Proxy efficiently manages traffic load, improves latency, and provides anonymity by routing requests to backend servers. For comprehensive security and optimized user experience, integrating both solutions can offer robust threat protection alongside enhanced traffic management.
Web Application Firewall Infographic
 libterm.com
libterm.com