Symmetric encryption uses the same key for both encrypting and decrypting data, ensuring fast and efficient protection of your information. It is widely applied in securing communications, data storage, and network protocols due to its simplicity and speed. Discover how symmetric encryption works and why it is a fundamental component of modern cybersecurity in the rest of this article.
Table of Comparison
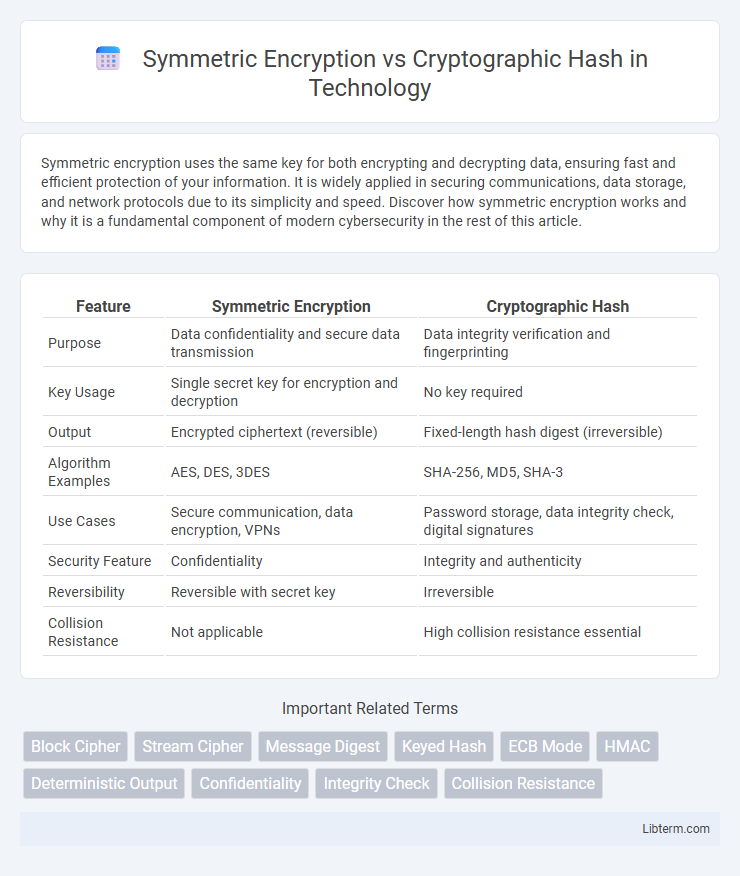
| Feature | Symmetric Encryption | Cryptographic Hash |
|---|---|---|
| Purpose | Data confidentiality and secure data transmission | Data integrity verification and fingerprinting |
| Key Usage | Single secret key for encryption and decryption | No key required |
| Output | Encrypted ciphertext (reversible) | Fixed-length hash digest (irreversible) |
| Algorithm Examples | AES, DES, 3DES | SHA-256, MD5, SHA-3 |
| Use Cases | Secure communication, data encryption, VPNs | Password storage, data integrity check, digital signatures |
| Security Feature | Confidentiality | Integrity and authenticity |
| Reversibility | Reversible with secret key | Irreversible |
| Collision Resistance | Not applicable | High collision resistance essential |
Introduction to Symmetric Encryption and Cryptographic Hash
Symmetric encryption uses a single secret key for both encryption and decryption, enabling fast and secure data confidentiality in communication systems. Cryptographic hash functions generate fixed-size, unique digests from input data, ensuring integrity and authenticity by detecting any changes. Both methods are fundamental in cybersecurity: symmetric encryption protects sensitive data during transmission, while cryptographic hashes verify data integrity and enable secure password storage.
Defining Symmetric Encryption
Symmetric encryption is a cryptographic method that uses a single secret key for both encryption and decryption of data, ensuring confidentiality and fast processing. It is widely employed in securing communication channels, such as AES (Advanced Encryption Standard) used in securing sensitive information. Unlike cryptographic hashes, which produce a fixed-size digest for data integrity verification, symmetric encryption allows reversible data transformation through the shared secret key.
Explaining Cryptographic Hash Functions
Cryptographic hash functions generate fixed-size output hashes from input data, ensuring data integrity by producing unique, irreversible digests. Unlike symmetric encryption that requires a secret key for both encryption and decryption, hash functions do not involve keys and are designed to be one-way, preventing the original data from being retrieved. Common algorithms, such as SHA-256 and MD5, are extensively used for verifying file authenticity, digital signatures, and password storage.
Core Differences between Symmetric Encryption and Hashing
Symmetric encryption uses a single secret key to both encrypt and decrypt data, ensuring confidentiality and enabling reversible transformation of plaintext to ciphertext. Cryptographic hashing, however, generates a fixed-length, unique hash value from input data, providing data integrity verification with a one-way, irreversible process. The core difference lies in encryption allowing data recovery via the same key, whereas hashing produces a non-reversible output primarily used for integrity checks and authentication.
Use Cases for Symmetric Encryption
Symmetric encryption is primarily used for securing data in transit and at rest, such as encrypting files, emails, or network communications, where the same key is shared between sender and receiver to ensure confidentiality. It enables fast and efficient encryption/decryption processes suitable for real-time applications like VPNs, SSL/TLS sessions, and disk encryption. Unlike cryptographic hashes, which verify data integrity and authenticity without reversible encryption, symmetric encryption focuses on protecting sensitive information from unauthorized access.
Use Cases for Cryptographic Hash Functions
Cryptographic hash functions are primarily used for data integrity verification, password hashing, and digital signatures, providing fixed-size output that uniquely represents input data. Unlike symmetric encryption, which enables data confidentiality through reversible transformation with a secret key, hash functions produce irreversible digests that protect against data tampering and ensure authenticity. Applications such as blockchain technology and secure password storage leverage cryptographic hashes to maintain security without exposing sensitive information.
Security Strengths and Limitations
Symmetric encryption uses a shared secret key for both encryption and decryption, providing strong data confidentiality but requiring secure key management to prevent unauthorized access. Cryptographic hash functions generate fixed-size outputs from input data, ensuring data integrity and authentication through collision resistance but do not offer encryption or confidentiality. While symmetric encryption protects data confidentiality, cryptographic hashes excel in verifying data integrity and authenticity, making them complementary in secure communication systems.
Common Algorithms: Symmetric vs Hash
Common symmetric encryption algorithms include AES, DES, and Blowfish, which utilize a single secret key for both encryption and decryption to ensure data confidentiality. Cryptographic hash functions such as SHA-256, MD5, and SHA-3 produce fixed-size hash values from input data, providing data integrity and authentication without reversible output. While symmetric algorithms protect information by transforming readable data into ciphertext, hash algorithms generate unique digital fingerprints that verify data authenticity and detect alterations.
Performance Considerations and Efficiency
Symmetric encryption algorithms like AES typically offer faster performance compared to cryptographic hash functions such as SHA-256 due to their design for data confidentiality with efficient block or stream processing. Cryptographic hashes prioritize data integrity and produce fixed-size outputs, often requiring more computational cycles per byte to ensure collision resistance and pre-image resistance. In high-throughput systems, symmetric encryption is favored for bulk data encryption, while hash functions are optimized for quick integrity verification and digital signatures.
Choosing the Right Approach for Data Protection
Symmetric encryption uses a single secret key to both encrypt and decrypt data, making it ideal for protecting sensitive information that requires confidentiality and quick access. Cryptographic hash functions generate fixed-size, unique outputs from input data, ensuring data integrity and authentication without reversible encryption. Choosing the right approach depends on whether the primary goal is to maintain data confidentiality through reversible encryption or to verify data integrity and authenticity with irreversible hash functions.
Symmetric Encryption Infographic
 libterm.com
libterm.com