Efficient user management is essential for maintaining security and enhancing productivity within any organization. Streamlined processes allow you to easily assign roles, monitor access levels, and ensure compliance with data protection policies. Explore the full article to discover best practices for optimizing your user management system.
Table of Comparison
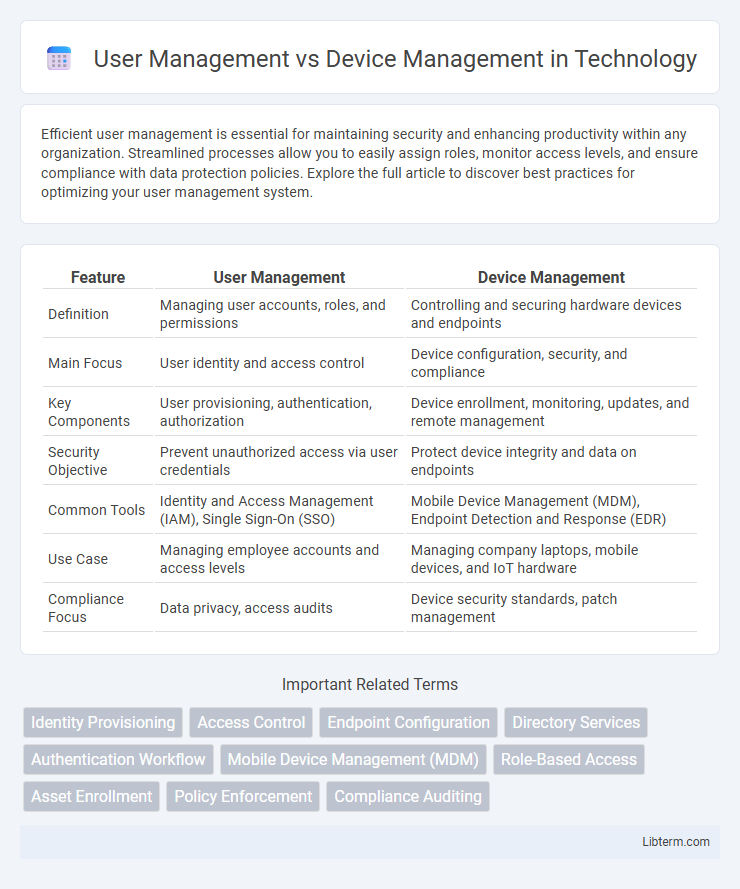
| Feature | User Management | Device Management |
|---|---|---|
| Definition | Managing user accounts, roles, and permissions | Controlling and securing hardware devices and endpoints |
| Main Focus | User identity and access control | Device configuration, security, and compliance |
| Key Components | User provisioning, authentication, authorization | Device enrollment, monitoring, updates, and remote management |
| Security Objective | Prevent unauthorized access via user credentials | Protect device integrity and data on endpoints |
| Common Tools | Identity and Access Management (IAM), Single Sign-On (SSO) | Mobile Device Management (MDM), Endpoint Detection and Response (EDR) |
| Use Case | Managing employee accounts and access levels | Managing company laptops, mobile devices, and IoT hardware |
| Compliance Focus | Data privacy, access audits | Device security standards, patch management |
Introduction to User Management and Device Management
User Management centralizes control over user identities, access rights, and roles to ensure secure authentication and authorization within an IT environment. Device Management involves monitoring, configuring, and securing hardware assets such as laptops, smartphones, and IoT devices to maintain operational efficiency and enforce security policies. Both frameworks are essential components of enterprise IT infrastructure, enabling seamless coordination between user access and device integrity.
Key Differences Between User Management and Device Management
User Management focuses on administering user identities, roles, access permissions, and authentication across systems to ensure secure and personalized user experiences. Device Management involves the configuration, monitoring, security, and maintenance of physical devices such as smartphones, laptops, and IoT equipment to guarantee operational integrity and compliance. Key differences include User Management managing digital identities and access control, while Device Management handles hardware lifecycle, security patches, and device-specific policy enforcement.
Core Functions of User Management
User Management primarily focuses on managing user identities, access permissions, and authentication processes to ensure secure and efficient access to systems and resources. It includes core functions such as user provisioning, role assignment, password management, and access control policies to maintain organizational security and compliance. Device Management, by contrast, handles the monitoring, configuration, and security of hardware devices, emphasizing device lifecycle and policy enforcement rather than individual user credentials.
Essential Features of Device Management
Device management essential features include device enrollment, configuration, monitoring, and remote control, ensuring secure access and compliance across all endpoints. It enables automated updates, policy enforcement, and real-time threat detection to protect devices from vulnerabilities. This comprehensive control contrasts with user management, which centers on authentication, role assignments, and access permissions for individual users.
Security Considerations for Users and Devices
User Management emphasizes securing identities and access controls by implementing strong authentication, role-based permissions, and continuous monitoring of user activities to prevent unauthorized data access or insider threats. Device Management focuses on enforcing security policies across endpoints, including device encryption, regular patching, and compliance checks to protect against malware, data breaches, and physical device loss. Integrating both ensures comprehensive protection by safeguarding user credentials while maintaining device integrity in dynamic IT environments.
Use Cases: When to Prioritize User Management
User Management is prioritized when security policies require tailored access controls based on individual roles, ensuring proper authorization and compliance within organizations. It is essential in scenarios involving frequent employee onboarding and offboarding, where user identity and permissions must be dynamically managed. Environments emphasizing collaboration and personalized user settings benefit from User Management to maintain operational efficiency and data protection.
Use Cases: When to Focus on Device Management
Device management is crucial in environments where hardware security, firmware updates, and physical asset control are priorities, such as in healthcare and manufacturing industries. It ensures real-time monitoring, configuration, and compliance of devices, reducing downtime and safeguarding sensitive data. User management complements device management but less effectively addresses hardware-specific risks and operational continuity.
Integration of User and Device Management Systems
Integrating user and device management systems enhances security by enabling centralized control over access permissions and device compliance policies. This unified approach streamlines identity verification processes and enforces consistent security standards across all endpoints. Organizations benefit from improved operational efficiency and reduced risk of unauthorized access through synchronized management of user credentials and device configurations.
Challenges in User and Device Management
User management faces challenges in ensuring secure authentication, handling diverse access permissions, and maintaining user privacy amidst growing cybersecurity threats. Device management struggles with the complexity of managing numerous device types, ensuring software updates across varied platforms, and preventing unauthorized device access. Both require robust policies and tools to balance security with usability in dynamic IT environments.
Best Practices for Unified Management Strategies
Implementing unified management strategies requires integrating user management and device management to enhance security and streamline IT operations. Best practices include leveraging identity and access management (IAM) systems with mobile device management (MDM) tools to enforce consistent policies, enable single sign-on (SSO), and provide role-based access control (RBAC). Centralized dashboards and automated compliance reporting improve visibility and responsiveness across user accounts and connected devices.
User Management Infographic
 libterm.com
libterm.com