Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to enable secure communication by generating encryption keys that are theoretically unbreakable. It uses the behavior of quantum particles to detect any eavesdropping attempts, ensuring the confidentiality of your transmitted information. Discover how QKD protects your data and revolutionizes cybersecurity by reading the rest of this article.
Table of Comparison
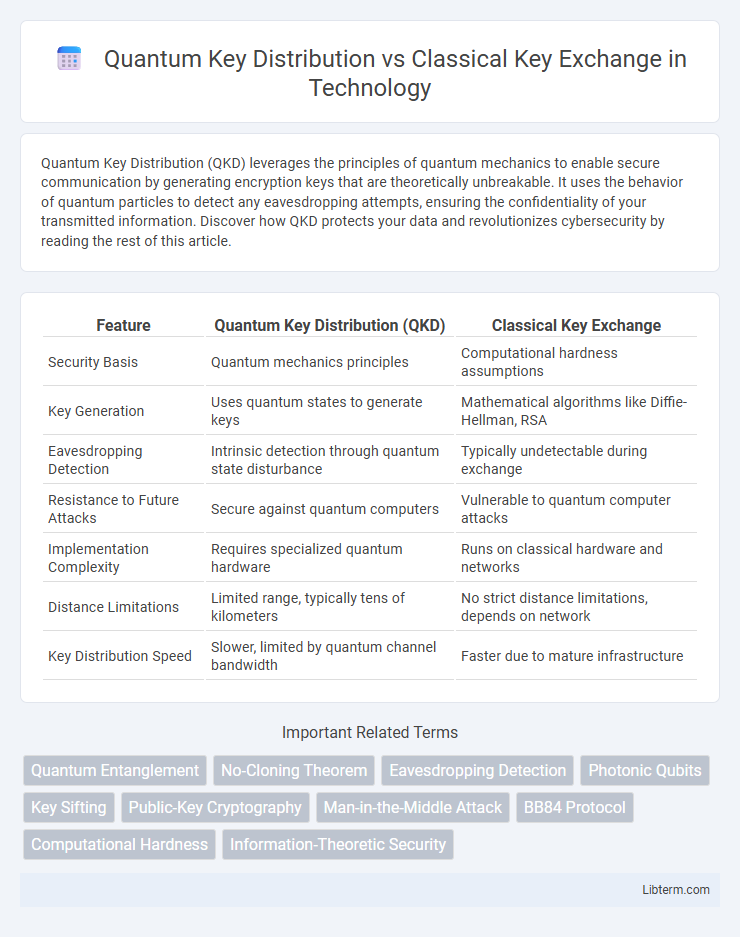
| Feature | Quantum Key Distribution (QKD) | Classical Key Exchange |
|---|---|---|
| Security Basis | Quantum mechanics principles | Computational hardness assumptions |
| Key Generation | Uses quantum states to generate keys | Mathematical algorithms like Diffie-Hellman, RSA |
| Eavesdropping Detection | Intrinsic detection through quantum state disturbance | Typically undetectable during exchange |
| Resistance to Future Attacks | Secure against quantum computers | Vulnerable to quantum computer attacks |
| Implementation Complexity | Requires specialized quantum hardware | Runs on classical hardware and networks |
| Distance Limitations | Limited range, typically tens of kilometers | No strict distance limitations, depends on network |
| Key Distribution Speed | Slower, limited by quantum channel bandwidth | Faster due to mature infrastructure |
Introduction to Secure Key Exchange
Quantum Key Distribution (QKD) leverages quantum mechanics principles to enable secure communication by generating cryptographic keys that are theoretically immune to eavesdropping, unlike classical key exchange methods relying on computational hardness assumptions. Classical key exchange algorithms such as Diffie-Hellman depend on mathematical problems like discrete logarithms or factoring large integers, which can be vulnerable to advances in quantum computing. QKD protocols, including BB84 and E91, introduce fundamentally secure key exchange through quantum states, ensuring detection of interception attempts and enhancing long-term data confidentiality.
Fundamentals of Quantum Key Distribution
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as superposition and entanglement, to securely distribute cryptographic keys with provable security against eavesdropping. Unlike classical key exchange methods based on mathematical complexity, QKD detects any interception attempt by measuring disturbances in quantum states, ensuring unconditional security validated by the laws of physics. Protocols like BB84 and E91 exemplify QKD's ability to establish shared encryption keys with guaranteed confidentiality unattainable through classical cryptographic techniques.
Overview of Classical Key Exchange Methods
Classical key exchange methods primarily rely on mathematical algorithms such as Diffie-Hellman, RSA, and elliptic curve cryptography to securely share encryption keys over public channels. These protocols depend on computational hardness assumptions, ensuring security against adversaries with limited processing power but remain vulnerable to attacks by quantum computers. Despite widespread adoption, classical key exchange systems face increasing risks as quantum computing advances threaten to solve underlying problems like prime factorization and discrete logarithms more efficiently.
Security Principles: Quantum vs Classical Approaches
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics, such as the no-cloning theorem and quantum entanglement, to enable theoretically unbreakable encryption by detecting eavesdropping through quantum state disturbances. Classical key exchange protocols, including Diffie-Hellman and RSA, rely on computational complexity assumptions that can be compromised by advances in algorithms or quantum computing, posing risks to their long-term security. The fundamental security distinction lies in QKD's intrinsic ability to provide information-theoretic security, while classical methods depend on computational hardness assumptions that may be vulnerable to future technological developments.
Vulnerabilities and Attack Resistance
Quantum Key Distribution (QKD) leverages the principles of quantum mechanics to detect eavesdropping attempts, providing provable security against interception through phenomena like quantum no-cloning and disturbance of quantum states. Classical key exchange protocols, such as Diffie-Hellman, rely on computational hardness assumptions that are vulnerable to attacks by quantum computers, especially Shor's algorithm, which threatens to break widely used public-key cryptography. While classical methods face risks from advances in computing power and algorithmic breakthroughs, QKD offers inherent resistance to these vulnerabilities by enabling secure key generation that can reveal any unauthorized access during transmission.
Performance and Scalability
Quantum Key Distribution (QKD) offers unconditionally secure key exchange by leveraging quantum mechanics but faces challenges in performance due to limited transmission distance and low key generation rates compared to classical key exchange methods like Diffie-Hellman or RSA, which provide higher speeds and broader network compatibility. Scalability issues in QKD arise from the need for specialized quantum hardware and quantum repeaters to extend communication beyond metropolitan areas, whereas classical key exchanges benefit from mature infrastructure and widespread deployment, enabling easier integration into large-scale systems. Despite these limitations, advancements in quantum network technologies and error correction techniques are gradually improving QKD's performance and scalability, positioning it as a complementary solution rather than a direct replacement for classical key exchange protocols.
Practical Implementation Challenges
Quantum Key Distribution (QKD) offers theoretically unbreakable encryption by leveraging quantum mechanics, but faces significant practical implementation challenges such as the requirement for specialized hardware like single-photon sources and detectors, sensitivity to environmental noise, and limited transmission distances without quantum repeaters. Classical key exchange methods, including RSA and Diffie-Hellman, benefit from mature infrastructure and widespread compatibility but are vulnerable to advances in quantum computing that threaten their cryptographic security. Deploying QKD systems requires overcoming scalability issues, high costs, and integration with existing communication networks, while classical systems rely on computational hardness assumptions that may not hold long-term.
Current Applications and Use Cases
Quantum Key Distribution (QKD) is primarily applied in high-security environments such as government communications, financial institutions, and critical infrastructure to provide theoretically unbreakable encryption keys based on quantum mechanics. Classical key exchange protocols, like Diffie-Hellman and RSA, remain widely used in everyday internet applications including VPNs, HTTPS, and secure emails due to their compatibility with existing digital infrastructure and efficiency. Emerging use cases for QKD involve securing satellite communications and integrating with 5G networks to enhance privacy and resist future quantum computing attacks.
Future Prospects in Cryptography
Quantum Key Distribution (QKD) offers unparalleled security by leveraging principles of quantum mechanics, ensuring theoretically unbreakable encryption resistant to future quantum computing attacks. Classical key exchange methods, such as Diffie-Hellman, remain vulnerable to advancements in quantum algorithms like Shor's algorithm, prompting urgent research to develop quantum-resistant cryptographic protocols. Future prospects in cryptography emphasize integrating QKD with classical infrastructure and advancing post-quantum cryptography to create hybrid systems that secure communication in the emerging quantum era.
Conclusion: Quantum Key Distribution vs Classical Key Exchange
Quantum Key Distribution (QKD) offers unparalleled security by leveraging the principles of quantum mechanics to detect eavesdropping, unlike classical key exchange methods that rely on computational hardness assumptions vulnerable to quantum computing attacks. Classical key exchange protocols, such as RSA and Diffie-Hellman, face increasing risks from advances in quantum algorithms, notably Shor's algorithm. QKD provides a future-proof solution for secure communication by enabling theoretically unbreakable encryption keys, making it essential for protecting sensitive information in the post-quantum era.
Quantum Key Distribution Infographic
 libterm.com
libterm.com