Transport Layer Security (TLS) is a cryptographic protocol that ensures privacy and data integrity between communicating applications and users over a network. It protects sensitive information from eavesdropping, tampering, and forgery by employing encryption and certificate-based authentication. Discover how TLS safeguards your digital interactions and why it's essential for online security by reading the rest of this article.
Table of Comparison
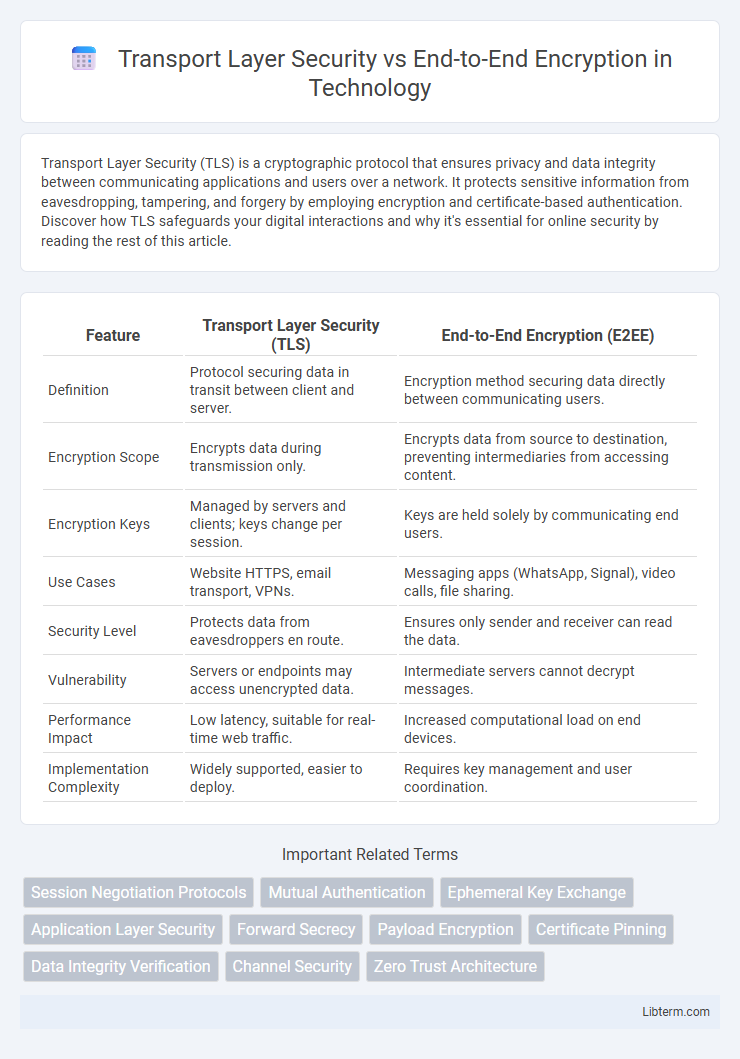
| Feature | Transport Layer Security (TLS) | End-to-End Encryption (E2EE) |
|---|---|---|
| Definition | Protocol securing data in transit between client and server. | Encryption method securing data directly between communicating users. |
| Encryption Scope | Encrypts data during transmission only. | Encrypts data from source to destination, preventing intermediaries from accessing content. |
| Encryption Keys | Managed by servers and clients; keys change per session. | Keys are held solely by communicating end users. |
| Use Cases | Website HTTPS, email transport, VPNs. | Messaging apps (WhatsApp, Signal), video calls, file sharing. |
| Security Level | Protects data from eavesdroppers en route. | Ensures only sender and receiver can read the data. |
| Vulnerability | Servers or endpoints may access unencrypted data. | Intermediate servers cannot decrypt messages. |
| Performance Impact | Low latency, suitable for real-time web traffic. | Increased computational load on end devices. |
| Implementation Complexity | Widely supported, easier to deploy. | Requires key management and user coordination. |
Introduction to Data Security Protocols
Transport Layer Security (TLS) ensures data integrity and encryption between a client and server, protecting information during transit across networks. End-to-End Encryption (E2EE) encrypts data directly between communicating parties, preventing intermediaries from accessing the plaintext. Data security protocols like TLS and E2EE are fundamental for safeguarding sensitive information in online communications and preventing unauthorized access.
What Is Transport Layer Security (TLS)?
Transport Layer Security (TLS) is a cryptographic protocol designed to provide secure communication over a computer network by encrypting data between client and server, preventing eavesdropping, tampering, and message forgery. TLS operates at the transport layer, establishing a secure channel through handshake mechanisms that authenticate parties and negotiate encryption keys. Widely used in HTTPS connections, TLS ensures data integrity and confidentiality during transmission, but unlike end-to-end encryption, it protects data only while in transit, not during storage or processing on intermediate servers.
Understanding End-to-End Encryption (E2EE)
End-to-End Encryption (E2EE) ensures that data is encrypted on the sender's device and only decrypted on the recipient's device, preventing intermediaries from accessing the content. Unlike Transport Layer Security (TLS), which secures data during transit between servers but can be decrypted at endpoints, E2EE provides a higher level of privacy by maintaining encryption throughout the entire communication path. This mechanism is crucial for protecting sensitive information in messaging apps, secure file sharing, and confidential communication channels.
Core Differences: TLS vs. End-to-End Encryption
Transport Layer Security (TLS) encrypts data between a client and a server, securing communication channels but allowing intermediaries like service providers to access decrypted content. End-to-End Encryption (E2EE) ensures that only the communicating users hold the decryption keys, preventing intermediaries from reading the transmitted data. TLS operates at the transport layer to protect data in transit, while E2EE encrypts data at the application layer, providing a higher level of privacy by securing data from sender to recipient.
Use Cases for TLS in Modern Networks
Transport Layer Security (TLS) is widely used to secure data in transit between clients and servers, protecting web browsing, email, and API communications in modern networks. TLS is essential for securing HTTPS connections, ensuring data integrity and confidentiality over public networks without requiring endpoint control. Unlike end-to-end encryption, which encrypts data from sender to recipient without intermediate decryption, TLS secures data primarily during transmission, making it ideal for securing data in client-server architectures and cloud environments.
Applications of End-to-End Encryption in Communication
End-to-End Encryption (E2EE) secures communication by ensuring that only the communicating users can read the messages, preventing intermediaries from accessing the content. Applications like WhatsApp, Signal, and iMessage implement E2EE to protect user conversations, voice calls, and video chats from eavesdropping and unauthorized access. Unlike Transport Layer Security (TLS), which encrypts data in transit between client and server, E2EE maintains encryption throughout the entire communication path, providing stronger privacy guarantees in messaging and collaboration platforms.
Strengths and Limitations of TLS
Transport Layer Security (TLS) offers robust data protection by encrypting communications between client and server, ensuring confidentiality, integrity, and authentication during transit. Its strength lies in widespread adoption, standardized protocols, and fast performance with minimal latency, making it suitable for securing web traffic and VPNs. However, TLS security is limited to the communication channel, leaving data exposed on endpoints and vulnerable to server-side breaches, unlike end-to-end encryption which secures payloads throughout the entire transmission path.
Advantages and Challenges of End-to-End Encryption
End-to-End Encryption (E2EE) ensures that only communicating users can read the messages, providing superior privacy by preventing intermediaries, including service providers, from accessing the content. Its main advantage lies in robust data protection against surveillance and unauthorized access, crucial for sensitive communications in sectors like finance and healthcare. Challenges include complex key management, potential usability issues, and difficulties in content filtering or lawful interception, which can limit scalability and regulatory compliance.
Choosing the Right Security Approach for Your Needs
Transport Layer Security (TLS) secures data during transmission between devices by encrypting the communication channel, ideal for protecting information in transit on networks like the internet. End-to-End Encryption (E2EE) encrypts data from the sender to the receiver, ensuring only authorized parties can decrypt the content, making it essential for highly confidential communications such as messaging apps and sensitive data exchanges. Selecting the appropriate security method depends on the specific use case: TLS is suitable for general data transport security, while E2EE is preferred when absolute message privacy and control over encryption keys are critical.
Future Trends in Encryption and Data Privacy
Future trends in encryption and data privacy emphasize enhancing End-to-End Encryption (E2EE) to provide stronger user-centric data protection compared to Transport Layer Security (TLS), which primarily secures data in transit between devices. Advances in quantum-resistant algorithms and zero-knowledge proofs are expected to bolster E2EE, ensuring confidentiality even against emerging quantum computing threats. Integration of decentralized identity management and blockchain technology further supports secure, transparent, and user-controlled data privacy frameworks beyond traditional TLS implementations.
Transport Layer Security Infographic
 libterm.com
libterm.com