Asymmetric encryption uses a pair of keys--a public key for encryption and a private key for decryption--to secure data transmissions effectively. This method enhances security by ensuring that only the intended recipient can access the encrypted information, making it essential for protecting sensitive communications and online transactions. Explore this article to understand how asymmetric encryption safeguards your digital interactions and why it's crucial in today's cybersecurity landscape.
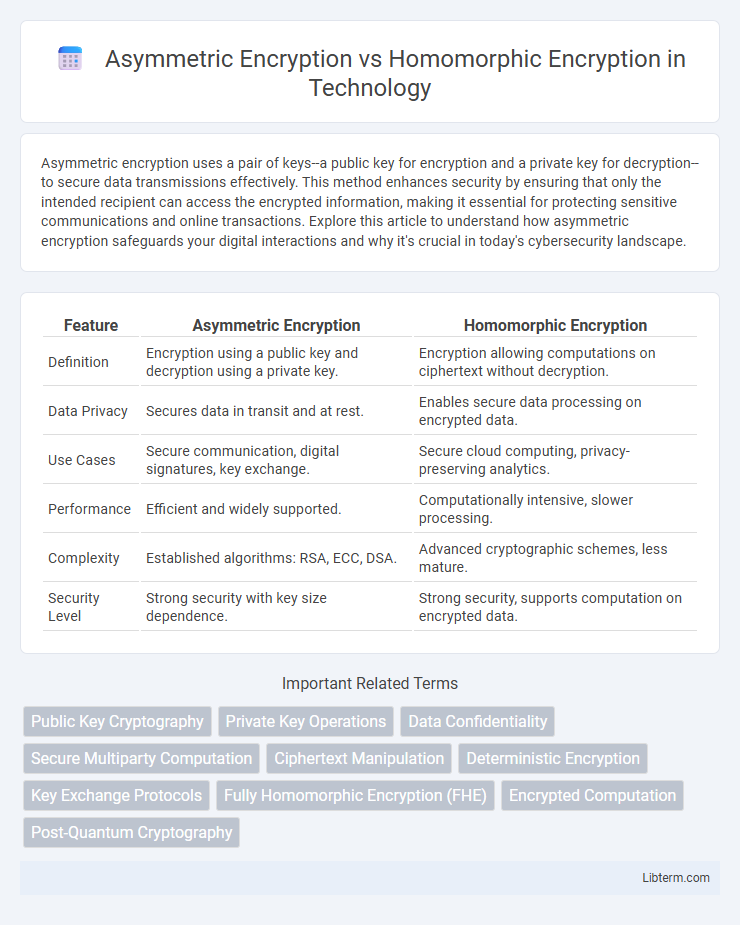
Table of Comparison
| Feature | Asymmetric Encryption | Homomorphic Encryption |
|---|---|---|
| Definition | Encryption using a public key and decryption using a private key. | Encryption allowing computations on ciphertext without decryption. |
| Data Privacy | Secures data in transit and at rest. | Enables secure data processing on encrypted data. |
| Use Cases | Secure communication, digital signatures, key exchange. | Secure cloud computing, privacy-preserving analytics. |
| Performance | Efficient and widely supported. | Computationally intensive, slower processing. |
| Complexity | Established algorithms: RSA, ECC, DSA. | Advanced cryptographic schemes, less mature. |
| Security Level | Strong security with key size dependence. | Strong security, supports computation on encrypted data. |
Introduction to Encryption Methods
Asymmetric encryption uses paired public and private keys to secure data, enabling safe communication by encrypting data with a public key and decrypting it with a private one. Homomorphic encryption allows computations directly on encrypted data without decryption, preserving privacy while enabling data processing in cloud environments. Both methods address data security but differ in operation and application scope, with asymmetric encryption focusing on secure data exchange and homomorphic encryption enabling encrypted data manipulation.
Understanding Asymmetric Encryption
Asymmetric encryption uses a pair of mathematically linked keys--a public key for encryption and a private key for decryption--enabling secure communication without sharing secret keys. Widely implemented in protocols like RSA and ECC, it ensures data confidentiality and authentication in applications such as SSL/TLS and digital signatures. Its reliance on complex mathematical problems provides strong security but requires careful key management and computational resources for encryption and decryption processes.
Overview of Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy while processing sensitive information. Unlike asymmetric encryption, which primarily secures data transmission through public and private keys, homomorphic encryption allows mathematical operations to be performed directly on ciphertexts, producing encrypted results equivalent to operations on plaintext. This encryption method is critical for secure data analytics, cloud computing, and privacy-preserving machine learning.
Key Differences Between Asymmetric and Homomorphic Encryption
Asymmetric encryption uses a pair of keys--public and private--for secure data encryption and decryption, enabling secure communication and digital signatures. Homomorphic encryption allows computations to be performed directly on encrypted data without revealing the plaintext, preserving privacy during data processing. The key difference lies in functionality: asymmetric encryption focuses on secure data transmission, while homomorphic encryption emphasizes secure data computation on encrypted information.
Security Strengths: Asymmetric vs Homomorphic
Asymmetric encryption relies on a pair of public and private keys to secure data, offering strong protection against unauthorized access and widely deployed for secure communications and digital signatures. Homomorphic encryption enables computations on encrypted data without decryption, preserving data privacy during processing but often with higher computational complexity and performance overhead. While asymmetric encryption balances security and efficiency for data transmission, homomorphic encryption excels in maintaining confidentiality in cloud computing and secure data analysis environments.
Use Cases for Asymmetric Encryption
Asymmetric encryption is widely used for securing data transmission, enabling secure key exchange, digital signatures, and authentication in protocols such as SSL/TLS and PGP. It protects sensitive information in email communication, online banking, and e-commerce by allowing public keys for encryption and private keys for decryption. Industries including finance, healthcare, and government rely on asymmetric encryption for secure identity verification and confidential data sharing across untrusted networks.
Practical Applications of Homomorphic Encryption
Homomorphic encryption enables secure computations on encrypted data without exposing the underlying information, making it ideal for privacy-preserving data analysis in cloud computing, healthcare, and financial services. Unlike traditional asymmetric encryption, which only secures data during transmission or storage, homomorphic encryption allows complex operations such as searching, aggregating, and machine learning directly on ciphertext. This capability addresses regulatory compliance challenges by protecting sensitive data while maintaining functionality in outsourced or multi-party environments.
Performance and Efficiency Comparison
Asymmetric encryption typically offers faster encryption and decryption times due to its reliance on well-established algorithms like RSA and ECC, but it requires secure key management and is less efficient for processing large datasets. Homomorphic encryption enables computation on encrypted data without decryption, preserving privacy during processing, yet it incurs significant computational overhead and slower performance, often resulting in inefficient processing speeds for complex operations. Performance trade-offs favor asymmetric encryption for standard secure communication, while homomorphic encryption excels in scenarios demanding privacy-preserving computation despite its higher resource consumption.
Challenges and Limitations
Asymmetric encryption faces challenges such as slower processing speeds and larger key sizes compared to symmetric methods, limiting its efficiency in real-time applications. Homomorphic encryption, while enabling computations on encrypted data, suffers from high computational overhead and significant performance degradation, making it impractical for complex, large-scale tasks. Both encryption techniques confront scalability issues and require advances in algorithm optimization to balance security with operational feasibility.
Future Trends in Encryption Technologies
Future trends in encryption technologies emphasize the integration of asymmetric encryption with homomorphic encryption to enhance data security and privacy in cloud computing and decentralized applications. Advances in quantum-resistant algorithms are driving the evolution of asymmetric encryption schemes, while homomorphic encryption continues to improve in efficiency, enabling secure computation on encrypted data without decryption. Emerging frameworks aim to combine these methods to support secure multiparty computations and privacy-preserving machine learning, addressing increasing demands for data confidentiality in AI and IoT ecosystems.
Asymmetric Encryption Infographic
 libterm.com
libterm.com