Hashed technology secures data by converting information into a fixed-size string of characters, making it nearly impossible to reverse-engineer the original input. This process strengthens your data protection against cyber threats and is widely used in password storage and blockchain systems. Discover how hashed functions enhance your digital security by exploring the rest of the article.
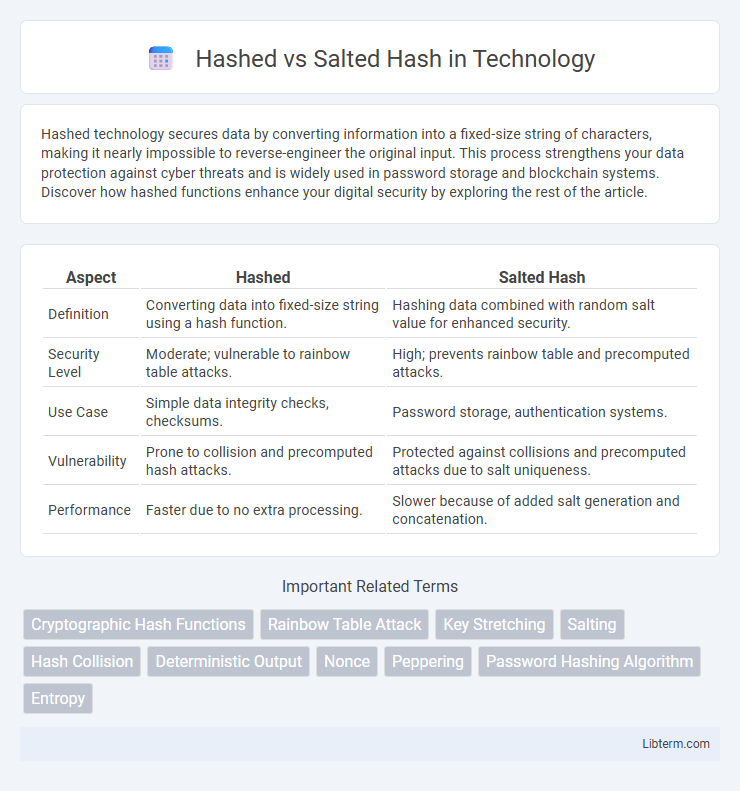
Table of Comparison
| Aspect | Hashed | Salted Hash |
|---|---|---|
| Definition | Converting data into fixed-size string using a hash function. | Hashing data combined with random salt value for enhanced security. |
| Security Level | Moderate; vulnerable to rainbow table attacks. | High; prevents rainbow table and precomputed attacks. |
| Use Case | Simple data integrity checks, checksums. | Password storage, authentication systems. |
| Vulnerability | Prone to collision and precomputed hash attacks. | Protected against collisions and precomputed attacks due to salt uniqueness. |
| Performance | Faster due to no extra processing. | Slower because of added salt generation and concatenation. |
Understanding Hashing: The Basics
Hashing transforms data into a fixed-length string of characters, providing a unique digital fingerprint for each input. Salted hash adds random data, called a salt, to the input before hashing, enhancing security against rainbow table attacks by ensuring identical inputs produce distinct hashes. Understanding the difference between basic hashing and salted hashing is crucial for implementing robust password protection and data integrity measures.
What is a Hashed Password?
A hashed password is a cryptographic representation of a plaintext password created by applying a hash function that converts the original password into a fixed-length string of characters, which is typically irreversible. This process ensures that the password is stored securely, preventing direct access to the original password if the hash is exposed. Hashing passwords is fundamental in cybersecurity to protect user credentials against theft and unauthorized access.
The Concept of Salting in Cryptography
Salting in cryptography involves adding a unique, random value known as a salt to each password before hashing to enhance security by preventing hash collisions and rainbow table attacks. This technique ensures that even identical passwords generate distinct hashed outputs, making it significantly harder for attackers to reverse-engineer or identify password matches. The use of salts in password hashing algorithms like bcrypt, scrypt, or Argon2 is crucial in safeguarding stored credentials against brute-force and precomputed hash attacks.
Key Differences Between Hashed and Salted Hash
Hashed data transforms original input into a fixed-length string using a cryptographic algorithm, while salted hash introduces unique random data (salt) to the input before hashing to enhance security. The key difference lies in salt preventing identical inputs from generating the same hash, thus protecting against rainbow table attacks and precomputed hash vulnerabilities. Salted hashes are crucial for securing passwords, ensuring each hash is unique even if users share identical passwords.
Why Simple Hashing Isn’t Enough
Simple hashing lacks the necessary security for password protection because it produces deterministic outputs, making it vulnerable to rainbow table attacks and precomputed hash lookups. Salted hashing incorporates a unique, random value--called a salt--into each password before hashing, vastly increasing resistance to these attacks by ensuring identical passwords result in different hash values. Hashed passwords without salts also suffer from decreased entropy, allowing attackers to exploit hash collisions and dictionary attacks more effectively.
How Salting Enhances Password Security
Salting enhances password security by adding a unique, random value to each password before hashing, preventing attackers from using precomputed hash tables like rainbow tables. This process ensures that identical passwords generate distinct hashes, significantly improving the resilience against dictionary and brute-force attacks. By incorporating salts, systems effectively mitigate vulnerabilities associated with unsalted hashed passwords, strengthening overall authentication security.
Common Hashing Algorithms Used Today
Common hashing algorithms used today include MD5, SHA-1, and SHA-256, each serving as the foundation for creating hashed values. Hashed values are typically generated by applying these algorithms directly to data, while salted hashes involve appending or prepending a unique random value (salt) to the input before hashing, enhancing security by protecting against rainbow table attacks. SHA-256 is widely preferred for its balance of speed and cryptographic strength, whereas MD5 and SHA-1 are now considered weak due to vulnerabilities to collision attacks.
Real-World Examples of Hashed vs Salted Hash
In cybersecurity, hashed passwords are commonly stored in databases using algorithms like SHA-256, but without salting, they remain vulnerable to rainbow table attacks, as seen in the 2012 LinkedIn data breach where millions of unsalted hashed passwords were exposed. Salting enhances security by adding unique random data to each password before hashing, an approach used by platforms such as Dropbox and Facebook to defend against precomputed hash attacks. Real-world implementations demonstrate that salted hashes significantly reduce the risk of password recovery and credential stuffing compared to simple hashed passwords.
Best Practices for Secure Password Storage
Salted hash involves adding a unique random value, called a salt, to each password before hashing, significantly enhancing security by preventing attacks using precomputed hash tables like rainbow tables. Best practices for secure password storage include using strong, adaptive hashing algorithms such as bcrypt, Argon2, or PBKDF2 combined with a unique salt for every password. Implementing these techniques ensures resistance against brute-force attacks and unauthorized access by making it computationally expensive to crack stored passwords.
Future Trends in Hashing and Salting Techniques
Future trends in hashing and salting techniques emphasize enhanced security measures such as adaptive hashing algorithms like Argon2 and scrypt, which resist GPU and ASIC-based attacks through increased computational cost and memory hardness. The integration of quantum-resistant hashing schemes is gaining traction to prepare for post-quantum cryptographic challenges, securing hashed passwords against emerging quantum computing threats. Salting methods are evolving to include unique, per-user salts combined with peppering strategies to strengthen defenses against rainbow table and precomputed hash attacks, ensuring robust protection for sensitive data.
Hashed Infographic
 libterm.com
libterm.com