Homomorphic encryption allows computation on encrypted data without needing to decrypt it first, preserving privacy and security in sensitive applications. This technology enables secure data analysis and processing in cloud computing, healthcare, and finance, where confidentiality is paramount. Explore the rest of the article to understand how homomorphic encryption can protect your information while enabling powerful data operations.
Table of Comparison
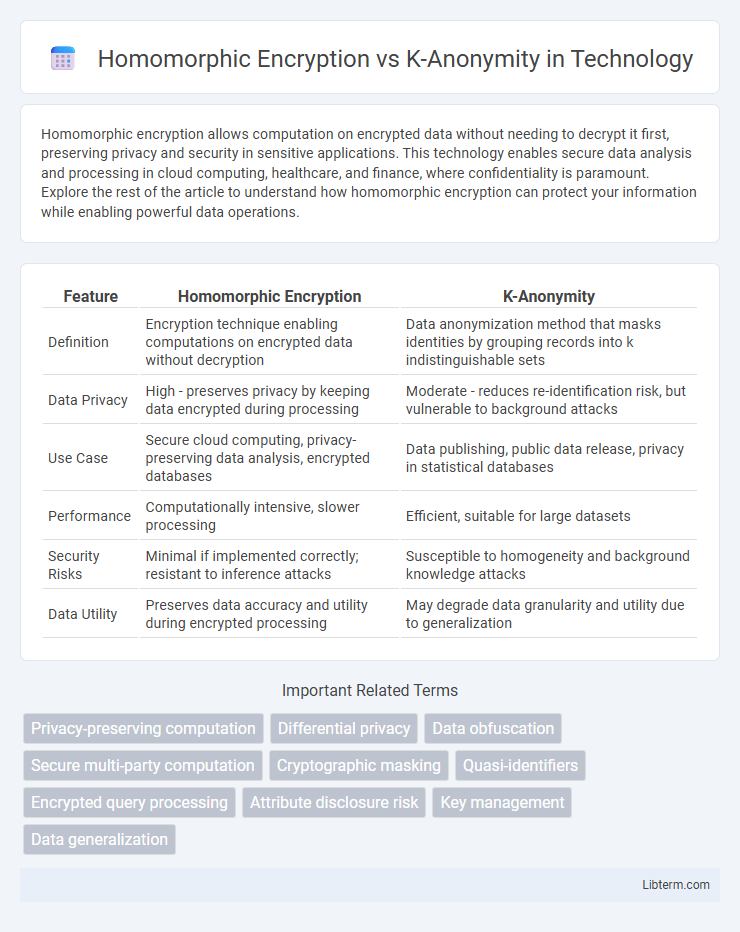
| Feature | Homomorphic Encryption | K-Anonymity |
|---|---|---|
| Definition | Encryption technique enabling computations on encrypted data without decryption | Data anonymization method that masks identities by grouping records into k indistinguishable sets |
| Data Privacy | High - preserves privacy by keeping data encrypted during processing | Moderate - reduces re-identification risk, but vulnerable to background attacks |
| Use Case | Secure cloud computing, privacy-preserving data analysis, encrypted databases | Data publishing, public data release, privacy in statistical databases |
| Performance | Computationally intensive, slower processing | Efficient, suitable for large datasets |
| Security Risks | Minimal if implemented correctly; resistant to inference attacks | Susceptible to homogeneity and background knowledge attacks |
| Data Utility | Preserves data accuracy and utility during encrypted processing | May degrade data granularity and utility due to generalization |
Introduction to Data Privacy Techniques
Homomorphic encryption enables computations on encrypted data without exposing sensitive information, preserving confidentiality in cloud computing and data analysis. K-anonymity anonymizes datasets by ensuring each individual's data is indistinguishable from at least k-1 others, reducing re-identification risks in data publishing. Both techniques address data privacy but differ fundamentally in approach: homomorphic encryption secures data during processing, whereas k-anonymity protects data at rest by masking identifiable attributes.
Understanding Homomorphic Encryption
Homomorphic encryption enables computations on encrypted data without decryption, preserving privacy while allowing complex data analysis. Unlike k-anonymity, which anonymizes datasets by masking identities through generalization or suppression, homomorphic encryption ensures data remains secure throughout the entire processing lifecycle. This cryptographic method supports secure outsourcing of sensitive calculations to untrusted environments without compromising confidentiality.
What Is K-Anonymity?
K-Anonymity is a privacy-preserving technique that ensures individual data records cannot be distinguished from at least k-1 other records in a dataset, thereby protecting against identity disclosure. It works by generalizing or suppressing identifiable attributes to create groups of indistinguishable entries, effectively reducing the risk of re-identification. Unlike Homomorphic Encryption, which encrypts data for secure computation, K-Anonymity focuses on data anonymization to maintain privacy in shared datasets.
Core Principles: Homomorphic Encryption vs K-Anonymity
Homomorphic encryption enables computations on encrypted data without decryption, preserving data privacy during processing by applying mathematical operations directly to ciphertexts. K-anonymity protects individual privacy in datasets by ensuring each record is indistinguishable from at least k-1 others through data generalization or suppression techniques. While homomorphic encryption secures data confidentiality during active use, k-anonymity focuses on mitigating re-identification risks in published datasets through data anonymization.
Use Cases: When to Choose Homomorphic Encryption
Homomorphic encryption is essential for scenarios requiring secure computation on encrypted data without exposing sensitive information, such as privacy-preserving machine learning, secure multiparty computations, and confidential data analysis in healthcare and finance. Unlike k-anonymity, which focuses on data anonymization to prevent re-identification in published datasets, homomorphic encryption enables real-time data processing and analytics while maintaining end-to-end confidentiality. Choose homomorphic encryption when data privacy must be preserved during computation, especially in environments demanding high confidentiality and regulatory compliance like GDPR and HIPAA.
Use Cases: When to Use K-Anonymity
K-Anonymity is ideal for data publishing scenarios where anonymized datasets must be shared for research, statistical analysis, or public release, preserving individual privacy by ensuring each record is indistinguishable from at least k-1 others. It is particularly effective in environments with structured data requiring masking of direct and quasi-identifiers to prevent re-identification attacks. Use cases include healthcare data de-identification, census data publication, and location-based services where aggregated data privacy without complex computation is sufficient.
Security Strengths and Limitations
Homomorphic Encryption enables computations on encrypted data without decryption, providing strong data confidentiality and integrity during processing, making it highly secure against data breaches and insider threats. K-Anonymity protects privacy by generalizing or suppressing identifiers to prevent re-identification in datasets, but it is vulnerable to background knowledge attacks and lacks robustness against attribute linkage. While Homomorphic Encryption ensures end-to-end data security with cryptographic guarantees, K-Anonymity offers simpler, less computationally intensive anonymization but with weaker protection against advanced inference.
Performance and Scalability Comparison
Homomorphic encryption enables data processing on encrypted data without decryption, ensuring strong privacy but often incurs significant computational overhead and slower performance compared to K-anonymity. K-anonymity provides scalable data anonymization by generalizing or suppressing identifiers to achieve privacy, resulting in faster processing but with potential risks of re-identification and weaker data utility. Performance-wise, K-anonymity excels in large-scale datasets due to lower complexity, while homomorphic encryption offers superior security at the cost of limited scalability and higher resource consumption.
Regulatory Compliance Considerations
Homomorphic encryption enables data processing on encrypted information without exposing raw data, offering strong compliance with regulations like GDPR and HIPAA by minimizing data exposure risks. K-anonymity focuses on data anonymization by ensuring each individual's data cannot be distinguished from at least K-1 others, but it may still face challenges under strict data protection laws due to potential re-identification risks. Regulatory frameworks increasingly favor homomorphic encryption for its ability to maintain data utility while strictly preserving privacy throughout data processing workflows.
Choosing the Right Technique for Your Data Privacy Needs
Homomorphic encryption allows computation on encrypted data, ensuring strong data privacy without exposing raw information, making it ideal for secure data processing in cloud environments. K-anonymity protects privacy by generalizing or suppressing data to prevent re-identification, suitable for data publishing with less computational overhead. Choose homomorphic encryption for high-security analytics and k-anonymity for balancing data utility and simple privacy protection.
Homomorphic Encryption Infographic
 libterm.com
libterm.com