Access control is a critical security measure that restricts entry to authorized users, safeguarding sensitive information and resources from unauthorized access. Implementing robust access control systems ensures your data remains protected while maintaining operational efficiency. Discover key strategies and technologies that enhance access control in the rest of this article.
Table of Comparison
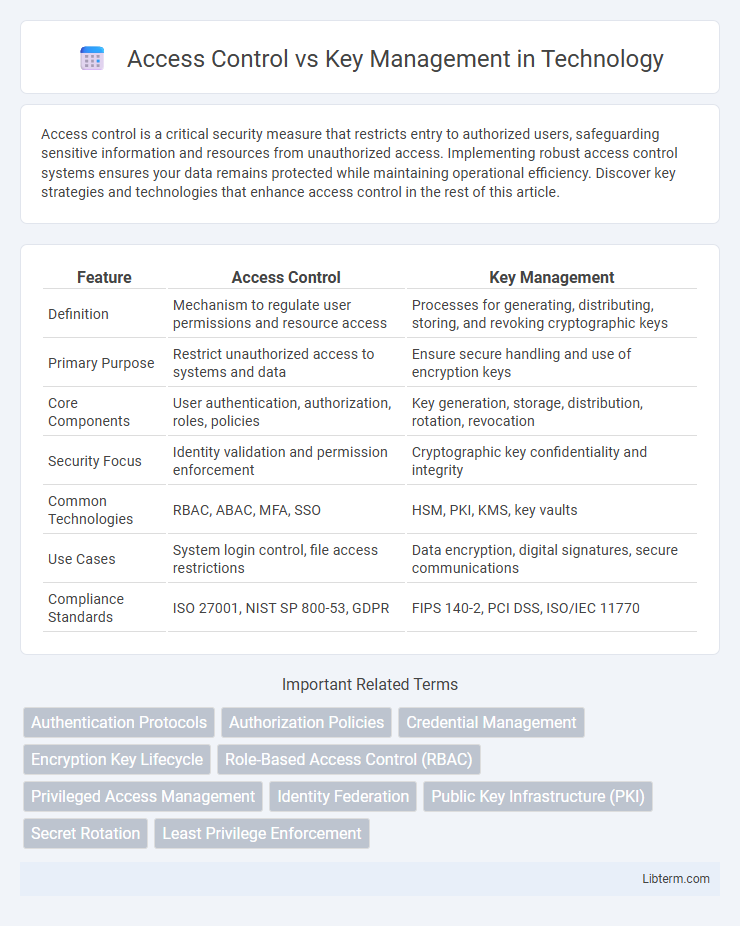
| Feature | Access Control | Key Management |
|---|---|---|
| Definition | Mechanism to regulate user permissions and resource access | Processes for generating, distributing, storing, and revoking cryptographic keys |
| Primary Purpose | Restrict unauthorized access to systems and data | Ensure secure handling and use of encryption keys |
| Core Components | User authentication, authorization, roles, policies | Key generation, storage, distribution, rotation, revocation |
| Security Focus | Identity validation and permission enforcement | Cryptographic key confidentiality and integrity |
| Common Technologies | RBAC, ABAC, MFA, SSO | HSM, PKI, KMS, key vaults |
| Use Cases | System login control, file access restrictions | Data encryption, digital signatures, secure communications |
| Compliance Standards | ISO 27001, NIST SP 800-53, GDPR | FIPS 140-2, PCI DSS, ISO/IEC 11770 |
Introduction to Access Control and Key Management
Access Control regulates user permissions to secure resources, defining who can access specific data or systems under what conditions, while Key Management involves generating, distributing, storing, and revoking cryptographic keys essential for encryption and decryption processes. Effective Access Control enforces policies such as role-based access control (RBAC) and attribute-based access control (ABAC) to maintain authorization integrity. Key Management ensures cryptographic keys remain confidential and secure throughout their lifecycle, supporting data confidentiality, integrity, and authentication in secure communication systems.
Core Concepts: Defining Access Control
Access control is the process of regulating who or what can view or use resources in a computing environment, defining permissions based on user identity, roles, or attributes. It enforces policies to restrict unauthorized access, ensuring data confidentiality, integrity, and availability. Key management, by contrast, handles the creation, distribution, and storage of cryptographic keys that underpin secure access control mechanisms.
Key Management Explained
Key management involves the generation, distribution, storage, and lifecycle maintenance of cryptographic keys essential for secure communication and data protection. Effective key management ensures that keys remain confidential, are accessible only to authorized entities, and are regularly rotated or revoked to prevent unauthorized access. Advanced key management systems employ automated policies, encryption standards like AES, and hardware security modules (HSMs) to safeguard keys against compromise and ensure compliance with security frameworks such as NIST SP 800-57.
Types of Access Control Systems
Types of access control systems include discretionary access control (DAC), mandatory access control (MAC), role-based access control (RBAC), and attribute-based access control (ABAC), each offering varying levels of security and flexibility. DAC allows users to control access to their resources, while MAC enforces strict policies determined by administrators, often used in military environments. RBAC assigns permissions based on user roles within an organization, and ABAC evaluates attributes and context to make dynamic access decisions, enhancing fine-grained security management compared to traditional key management systems.
Methods of Key Management
Effective key management methods include centralized, decentralized, and hierarchical approaches, each optimizing the distribution, storage, and lifecycle of cryptographic keys. Centralized key management provides a single authority for key generation and distribution, enhancing control but posing a single point of failure risk. Decentralized methods distribute key management tasks across multiple nodes, improving resilience and scalability, while hierarchical key management organizes keys in a tiered structure to streamline access and enforce layered security policies.
Security Risks: Access Control vs Key Management
Access control systems primarily address the security risk of unauthorized access by enforcing policies that restrict user permissions based on roles, but they can be vulnerable to credential theft or privilege escalation attacks. Key management involves the secure generation, distribution, storage, and rotation of cryptographic keys, with risks including key exposure, improper key lifecycle management, and weak encryption protocols that can lead to data breaches. Effective security architecture integrates robust access control mechanisms with stringent key management practices to mitigate risks such as insider threats, man-in-the-middle attacks, and cryptographic key compromise.
Implementation Challenges and Solutions
Access control implementation faces challenges such as ensuring granular user permissions, preventing unauthorized access, and integrating with diverse systems, which can be mitigated by deploying role-based access control (RBAC) models and using multi-factor authentication (MFA). Key management struggles with secure key generation, distribution, storage, and rotation, necessitating hardware security modules (HSMs) and automated key lifecycle management solutions to reduce human error and enhance security. Combining strong policy enforcement with centralized management platforms addresses both access control and key management complexities in enterprise environments.
Integration with Other Security Measures
Access control systems integrate with authentication protocols such as biometrics and multi-factor authentication to ensure precise identity verification and access permissions. Key management solutions synchronize with encryption frameworks and secure key storage to maintain confidentiality and integrity of sensitive data. Both access control and key management contribute to a robust security architecture by enabling seamless interoperability with intrusion detection systems and security information and event management (SIEM) platforms.
Cost and Scalability Considerations
Access control systems generally have lower upfront costs but can incur higher maintenance expenses as user base scales, while key management solutions often require significant initial investment due to hardware and encryption technologies but provide more predictable scaling costs. Scalability in access control may become complex and expensive in large organizations due to credential provisioning and revocation processes, whereas key management systems benefit from automated key distribution, reducing administrative overhead. Cost efficiency in both depends on organizational size and security requirements, with key management favored in environments demanding high security and rapid scalability.
Choosing the Right Solution for Your Organization
Access control defines who can enter or use resources within an organization, while key management focuses on securely generating, storing, and distributing cryptographic keys. Choosing the right solution involves assessing organizational needs such as user scalability, security compliance, and infrastructure compatibility. Integrating both systems enhances security by ensuring that only authorized users have access while maintaining strong cryptographic protection of sensitive data.
Access Control Infographic
 libterm.com
libterm.com