Spoofing involves disguising communication from an unknown source as being from a known, trusted source to gain access to your personal information or systems. This cyberattack technique can lead to identity theft, financial loss, and compromised security if not properly addressed. Read on to understand how spoofing works and how you can protect yourself from these deceptive threats.
Table of Comparison
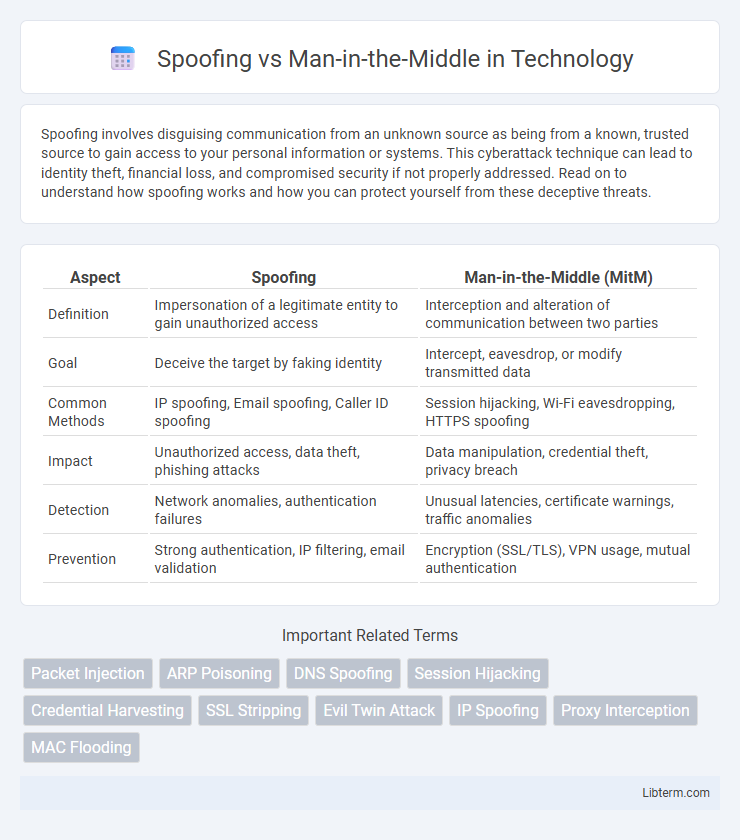
| Aspect | Spoofing | Man-in-the-Middle (MitM) |
|---|---|---|
| Definition | Impersonation of a legitimate entity to gain unauthorized access | Interception and alteration of communication between two parties |
| Goal | Deceive the target by faking identity | Intercept, eavesdrop, or modify transmitted data |
| Common Methods | IP spoofing, Email spoofing, Caller ID spoofing | Session hijacking, Wi-Fi eavesdropping, HTTPS spoofing |
| Impact | Unauthorized access, data theft, phishing attacks | Data manipulation, credential theft, privacy breach |
| Detection | Network anomalies, authentication failures | Unusual latencies, certificate warnings, traffic anomalies |
| Prevention | Strong authentication, IP filtering, email validation | Encryption (SSL/TLS), VPN usage, mutual authentication |
Introduction: Understanding Spoofing and Man-in-the-Middle
Spoofing involves impersonating a legitimate entity to gain unauthorized access or deceive users, often through falsified IP addresses, emails, or websites. Man-in-the-Middle (MitM) attacks intercept and potentially alter communications between two parties without their knowledge, compromising data integrity and confidentiality. Both threats exploit trust vulnerabilities in network protocols and are critical targets for cybersecurity defenses.
Defining Spoofing Attacks
Spoofing attacks involve impersonating a legitimate entity by falsifying data, such as IP addresses, email headers, or login credentials, to gain unauthorized access or deceive users. These attacks manipulate trust relationships within network communications, enabling attackers to intercept, alter, or redirect sensitive information. Common types include email spoofing, IP spoofing, and DNS spoofing, each targeting specific points in the communication process to exploit vulnerabilities.
What is a Man-in-the-Middle Attack?
A Man-in-the-Middle (MitM) attack occurs when an attacker intercepts and alters communication between two parties without their knowledge, enabling data theft or manipulation. This attack exploits vulnerabilities in network security protocols, allowing the intruder to eavesdrop, inject malicious content, or impersonate one of the communicating entities. MitM attacks are commonly executed through techniques such as packet sniffing, session hijacking, or rogue Wi-Fi hotspots, posing significant risks to sensitive information and online transactions.
Key Differences Between Spoofing and MITM
Spoofing involves an attacker masquerading as a legitimate entity by falsifying data such as IP addresses or email headers to deceive victims, whereas Man-in-the-Middle (MITM) attacks intercept and manipulate communication between two parties without their knowledge. Spoofing is often a preliminary step to facilitate MITM attacks, which enable eavesdropping, data alteration, or session hijacking. Key differences include spoofing's focus on impersonation and data fabrication, while MITM centers on real-time interception and manipulation of ongoing communications.
Common Techniques Used in Spoofing
Spoofing commonly involves techniques such as IP address spoofing, email spoofing, DNS spoofing, and ARP spoofing, each designed to deceive systems by impersonating legitimate entities. Attackers manipulate these protocols to intercept data, gain unauthorized access, or redirect traffic, enabling further exploitation in man-in-the-middle attacks. These spoofing methods serve as foundational tactics that facilitate the interception and alteration of communications in network security breaches.
Popular Methods of Man-in-the-Middle Attacks
Man-in-the-Middle (MitM) attacks exploit communication channels by intercepting or altering messages between two parties without their knowledge. Popular methods include ARP spoofing, where attackers send falsified ARP messages to link their MAC address with a legitimate IP address, and DNS spoofing, which redirects traffic by providing fake DNS responses. HTTPS stripping downgrades secure connections to insecure HTTP, enabling attackers to capture sensitive data transmitted over the network.
Real-World Examples: Spoofing vs MITM
Spoofing attacks, such as email spoofing in the notorious 2016 Democratic National Committee hack, manipulate sender identities to deceive recipients and gain unauthorized access or information. Man-in-the-Middle (MITM) attacks, exemplified by the 2011 DigiNotar breach, intercept and alter communications between parties without their knowledge, compromising data integrity and confidentiality. Real-world cases highlight that while spoofing exploits false identity presentation, MITM attacks leverage interception techniques to control communication channels covertly.
Security Vulnerabilities and Risks
Spoofing involves impersonating a trusted entity to gain unauthorized access or deceive users, often exploiting weaknesses in authentication protocols. Man-in-the-Middle (MitM) attacks intercept and manipulate communications between parties without their knowledge, targeting data integrity and confidentiality. Both vulnerabilities expose networks to risks such as data breaches, credential theft, and unauthorized transaction alterations, demanding robust encryption and authentication measures.
Detection and Prevention Strategies
Spoofing detection relies on methods such as IP address validation, email authentication protocols like SPF, DKIM, and DMARC, and hardware-based security modules that verify device identities. Man-in-the-Middle (MitM) attack prevention emphasizes the use of strong encryption protocols including TLS/SSL, mutual authentication, and certificate pinning to ensure secure communication channels. Network monitoring tools and anomaly detection systems play critical roles in identifying abnormal traffic patterns indicative of spoofing or MitM attempts, enhancing overall cybersecurity defenses.
Conclusion: Protecting Against These Cyber Threats
Protecting against spoofing and man-in-the-middle attacks requires implementing multi-factor authentication, encryption protocols such as TLS, and continuous network monitoring to detect suspicious activity. Employing endpoint security solutions, maintaining up-to-date software patches, and educating users about phishing tactics significantly reduce the risk of these cyber threats. A comprehensive security strategy combining technical controls and user awareness is essential to safeguard sensitive data and maintain network integrity.
Spoofing Infographic
 libterm.com
libterm.com