Peer-to-peer (P2P) technology allows computers to share resources and data directly without relying on a central server, enhancing efficiency and decentralization. This network model supports various applications, from file sharing to blockchain and distributed computing. Dive into the full article to discover how P2P can transform your digital interactions.
Table of Comparison
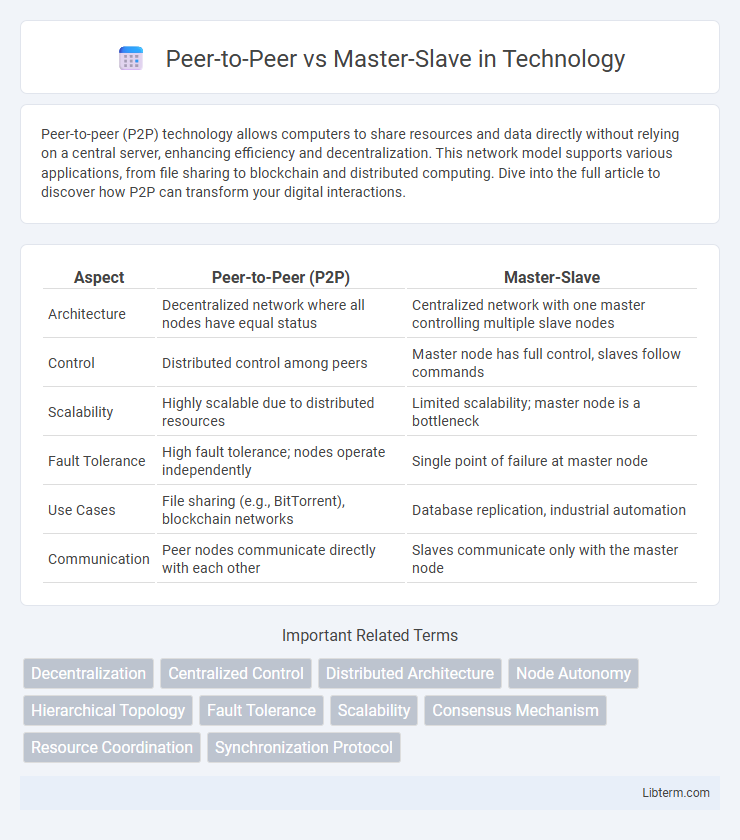
| Aspect | Peer-to-Peer (P2P) | Master-Slave |
|---|---|---|
| Architecture | Decentralized network where all nodes have equal status | Centralized network with one master controlling multiple slave nodes |
| Control | Distributed control among peers | Master node has full control, slaves follow commands |
| Scalability | Highly scalable due to distributed resources | Limited scalability; master node is a bottleneck |
| Fault Tolerance | High fault tolerance; nodes operate independently | Single point of failure at master node |
| Use Cases | File sharing (e.g., BitTorrent), blockchain networks | Database replication, industrial automation |
| Communication | Peer nodes communicate directly with each other | Slaves communicate only with the master node |
Understanding Peer-to-Peer Architecture
Peer-to-peer architecture distributes tasks and workloads across multiple nodes that share equal responsibilities and resources, enhancing system scalability and fault tolerance. Each node, or peer, can initiate or complete transactions independently without relying on a central controller, which differentiates it from the master-slave model where a single master node governs subordinate slaves. This decentralized structure enables efficient resource sharing, improved robustness against failures, and dynamic network configuration in applications like file sharing, blockchain, and distributed computing.
Master-Slave Model Explained
The Master-Slave model features a centralized control system where the master node manages and coordinates multiple slave nodes, ensuring task delegation and data consistency. This structure enhances reliability and performance in distributed systems by preventing conflicts and maintaining a clear hierarchy. Commonly used in database replication and industrial automation, the Master-Slave architecture supports synchronized operations and fault tolerance.
Key Differences Between Peer-to-Peer and Master-Slave
Peer-to-Peer (P2P) networks feature equal nodes that share resources and communicate directly without a centralized controller, enhancing fault tolerance and scalability. Master-Slave architecture relies on a single master node that controls multiple slave nodes, directing tasks and managing data flow, which centralizes control but can create a single point of failure. P2P excels in decentralized resource sharing, whereas Master-Slave is preferred for controlled coordination and simplified management in hierarchical systems.
Advantages of Peer-to-Peer Networks
Peer-to-Peer (P2P) networks offer decentralized communication, eliminating a single point of failure and ensuring greater network resilience compared to Master-Slave architectures. P2P networks improve resource sharing efficiency by allowing direct data exchange between nodes, enhancing overall system scalability and reducing latency. Enhanced fault tolerance and ease of network expansion make Peer-to-Peer models ideal for distributed computing and file-sharing applications.
Benefits of Master-Slave Systems
Master-slave systems offer centralized control, enabling simplified coordination and fault detection in complex networks. This architecture ensures consistent data synchronization and reduces conflicts by designating a primary controller that manages subordinate devices. Enhanced reliability and easier troubleshooting stem from the clear hierarchical structure inherent in master-slave configurations.
Common Use Cases for Peer-to-Peer
Peer-to-peer (P2P) networks are commonly used in file sharing applications, decentralized communication platforms, and blockchain technology due to their ability to distribute workloads evenly without relying on a central server. In contrast to master-slave architectures, P2P systems enhance fault tolerance and scalability by allowing each node to act both as a client and a server. Common use cases include BitTorrent for file distribution, cryptocurrency networks like Bitcoin, and collaborative platforms such as Skype and distributed computing projects.
Typical Applications of Master-Slave Architecture
Master-slave architecture is commonly used in industrial automation systems where a central controller (master) manages multiple devices or sensors (slaves) for coordinated operation. This configuration is prevalent in manufacturing plants for process control, data acquisition, and real-time monitoring. Additionally, it is widely applied in communication protocols such as Modbus and I2C, enabling synchronized data exchange between components.
Scalability and Performance Comparison
Peer-to-peer (P2P) architectures offer superior scalability by distributing workloads evenly across nodes, reducing bottlenecks common in master-slave models where a single master coordinates multiple slaves. Performance in P2P systems improves with the addition of more nodes, as tasks are processed in parallel, whereas master-slave systems often face diminished performance due to the master's centralized control and potential for overload. Consequently, P2P networks are more resilient and efficient in handling large-scale, dynamic environments compared to the limited scalability and performance constraints of master-slave configurations.
Security Considerations: P2P vs Master-Slave
Peer-to-Peer (P2P) networks offer decentralized communication, reducing single points of failure but increasing vulnerability to unauthorized data access and malicious nodes, requiring robust encryption and trust management protocols. Master-Slave architectures centralize control, enabling easier implementation of security policies and monitoring, yet they are susceptible to targeted attacks on the master node, risking entire system compromise. Effective security in P2P relies on consensus algorithms and distributed authentication, whereas Master-Slave systems prioritize access control and intrusion detection at the master level.
Choosing the Right Model for Your Project
Selecting the right communication model for your project depends on complexity, scalability, and control requirements. Peer-to-Peer (P2P) architectures offer decentralized control and enhanced fault tolerance, ideal for distributed applications and collaborative environments. Master-Slave models provide centralized management and simplified synchronization, best suited for systems needing strict coordination and predictable task execution.
Peer-to-Peer Infographic
 libterm.com
libterm.com