SQL injection attack exploits vulnerabilities in web applications by inserting malicious SQL code into input fields, allowing attackers to manipulate databases and access unauthorized information. Preventing SQL injection requires using prepared statements, parameterized queries, and rigorous input validation to safeguard your data. Explore the rest of the article to learn how to identify, prevent, and mitigate SQL injection threats effectively.
Table of Comparison
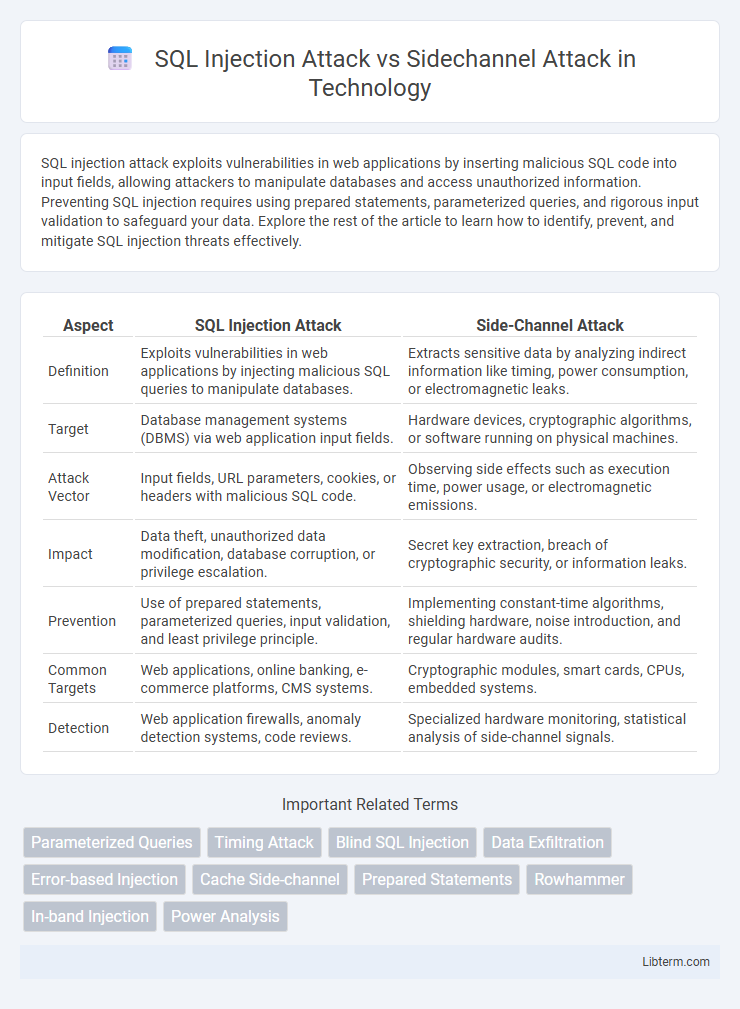
| Aspect | SQL Injection Attack | Side-Channel Attack |
|---|---|---|
| Definition | Exploits vulnerabilities in web applications by injecting malicious SQL queries to manipulate databases. | Extracts sensitive data by analyzing indirect information like timing, power consumption, or electromagnetic leaks. |
| Target | Database management systems (DBMS) via web application input fields. | Hardware devices, cryptographic algorithms, or software running on physical machines. |
| Attack Vector | Input fields, URL parameters, cookies, or headers with malicious SQL code. | Observing side effects such as execution time, power usage, or electromagnetic emissions. |
| Impact | Data theft, unauthorized data modification, database corruption, or privilege escalation. | Secret key extraction, breach of cryptographic security, or information leaks. |
| Prevention | Use of prepared statements, parameterized queries, input validation, and least privilege principle. | Implementing constant-time algorithms, shielding hardware, noise introduction, and regular hardware audits. |
| Common Targets | Web applications, online banking, e-commerce platforms, CMS systems. | Cryptographic modules, smart cards, CPUs, embedded systems. |
| Detection | Web application firewalls, anomaly detection systems, code reviews. | Specialized hardware monitoring, statistical analysis of side-channel signals. |
Introduction to Cybersecurity Threats
SQL Injection Attack exploits vulnerabilities in web applications by inserting malicious SQL queries to manipulate databases, leading to unauthorized data access or corruption. Sidechannel Attacks target physical implementations of systems, extracting sensitive information through indirect means such as timing, power consumption, or electromagnetic leaks. Both represent critical cybersecurity threats requiring robust defenses to protect data integrity and confidentiality.
What is an SQL Injection Attack?
An SQL Injection Attack exploits vulnerabilities in web applications by injecting malicious SQL code into input fields, enabling unauthorized access to databases and manipulation of sensitive data. Attackers can retrieve, modify, or delete database information, leading to data breaches and compromised system integrity. This method targets the application's improper input validation and insufficient parameterized query usage.
How SQL Injection Attacks Work
SQL Injection attacks exploit vulnerabilities in a web application's input fields to inject malicious SQL code, manipulating the backend database to retrieve, modify, or delete sensitive data. Attackers craft input that alters the intended SQL query logic, bypassing authentication or extracting confidential information without authorization. These attacks specifically target poorly sanitized or improperly parameterized SQL queries, enabling unauthorized database access and data breaches.
Understanding Sidechannel Attacks
Sidechannel attacks exploit indirect information leakage from physical implementations of systems, such as timing, power consumption, or electromagnetic emissions, revealing sensitive data like cryptographic keys. Unlike SQL injection attacks that manipulate database queries through input vulnerabilities, sidechannel attacks require analyzing hardware behavior or system responses outside typical input channels. Understanding sidechannel attacks involves grasping how attackers monitor unintended physical signals to bypass traditional software defenses and compromise security.
Mechanics of Sidechannel Attacks
Sidechannel attacks exploit indirect information leakage from physical implementations of systems, such as electromagnetic emissions, power consumption, or timing variations, to extract sensitive data without directly interacting with the software code like SQL Injection attacks do. Unlike SQL Injection, which manipulates input parameters to execute malicious queries, sidechannel attacks analyze hardware behavior to infer encryption keys or passwords. Techniques such as differential power analysis and timing analysis enable attackers to gain unauthorized access by monitoring these physical side effects.
Key Differences Between SQL Injection and Sidechannel Attacks
SQL Injection attacks exploit vulnerabilities in web application input fields to manipulate database queries, aiming to extract or modify sensitive data through unauthorized SQL commands. Sidechannel attacks target hardware or software implementation flaws, using indirect information such as timing, power consumption, or electromagnetic leaks to infer secret data like encryption keys. The key difference lies in SQL Injection attacking software-level input validation weaknesses, whereas Sidechannel attacks leverage physical or operational characteristics of systems to compromise security.
Impact of SQL Injection vs Sidechannel Attacks
SQL Injection attacks primarily compromise database integrity by allowing attackers to manipulate or extract sensitive data, often leading to unauthorized data disclosure, loss, or corruption. Sidechannel attacks exploit physical implementation vulnerabilities, such as timing or power consumption, to indirectly gain confidential information like cryptographic keys without direct database access. The impact of SQL Injection typically results in direct data breaches and control loss over database systems, whereas Sidechannel attacks threaten data confidentiality by leaking sensitive information through indirect, non-invasive means.
Detection Techniques for SQL Injection and Sidechannel Attacks
SQL Injection detection techniques primarily rely on input validation, parameterized queries, and anomaly-based intrusion detection systems that monitor query patterns for unusual behavior. Sidechannel attack detection involves monitoring physical or timing-related anomalies using power analysis, electromagnetic emission sensors, or time-based side channel metrics to identify deviations from standard operation. Machine learning algorithms enhance detection accuracy in both attacks by analyzing behavioral signatures and correlation patterns in data access or execution timing.
Prevention and Mitigation Strategies
SQL injection attack prevention relies on parameterized queries, input validation, and regular security audits to eliminate injection flaws. Side-channel attack mitigation involves implementing constant-time algorithms, hardware shielding, and noise generation to prevent information leakage through physical characteristics. Employing multi-layered defenses tailored to each attack vector enhances overall system security and reduces exploitation risks.
Conclusion: Choosing the Right Security Measures
Selecting the appropriate security measures requires understanding the distinct nature of SQL Injection and Sidechannel Attacks. SQL Injection defenses prioritize input validation and parameterized queries to prevent malicious data manipulation within databases. In contrast, Sidechannel Attack mitigation focuses on hardware-level protections, constant-time algorithms, and shielding sensitive information from indirect leakages.
SQL Injection Attack Infographic
 libterm.com
libterm.com