Purple Team bridges the gap between offensive red teams and defensive blue teams by promoting collaboration and continuous feedback for enhanced cybersecurity. This integrated approach helps organizations identify vulnerabilities and strengthen defenses more effectively. Discover how implementing a Purple Team strategy can elevate your security posture in the rest of the article.
Table of Comparison
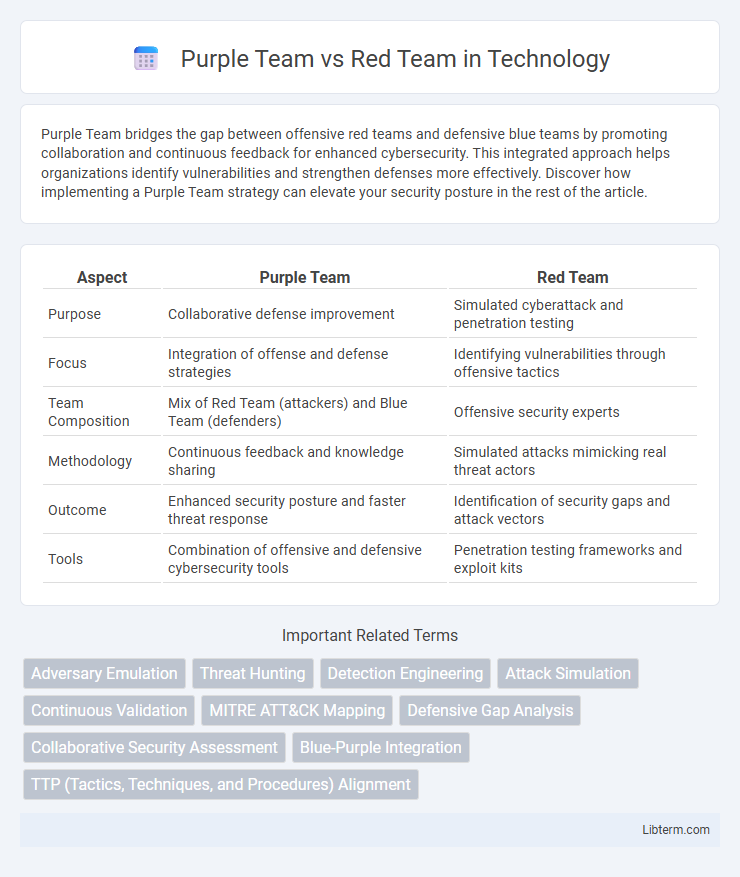
| Aspect | Purple Team | Red Team |
|---|---|---|
| Purpose | Collaborative defense improvement | Simulated cyberattack and penetration testing |
| Focus | Integration of offense and defense strategies | Identifying vulnerabilities through offensive tactics |
| Team Composition | Mix of Red Team (attackers) and Blue Team (defenders) | Offensive security experts |
| Methodology | Continuous feedback and knowledge sharing | Simulated attacks mimicking real threat actors |
| Outcome | Enhanced security posture and faster threat response | Identification of security gaps and attack vectors |
| Tools | Combination of offensive and defensive cybersecurity tools | Penetration testing frameworks and exploit kits |
Understanding Red Team and Purple Team Roles
Red Team members simulate realistic cyberattacks, identifying vulnerabilities and testing an organization's defenses to improve security posture. Purple Team integrates both offensive tactics of the Red Team and defensive strategies of the Blue Team, facilitating continuous collaboration and knowledge sharing to enhance overall threat detection and response. Understanding the distinct roles helps organizations optimize their cybersecurity efforts, leveraging Red Team's adversarial mindset and Purple Team's coordination to strengthen resilience against cyber threats.
Key Objectives of Red Team Operations
Red Team operations focus on simulating realistic cyberattacks to identify vulnerabilities within an organization's security posture. Their key objectives include testing detection and response capabilities, uncovering hidden weaknesses in defenses, and providing actionable insights to improve overall cybersecurity resilience. By mimicking adversarial tactics, Red Teams help organizations strengthen their threat mitigation strategies and reduce potential risks.
The Evolution and Purpose of Purple Teams
Purple Teams have evolved as a collaborative approach combining Red Teams' offensive tactics with Blue Teams' defensive strategies to enhance overall cybersecurity posture. Their purpose centers on continuous threat simulation and real-time feedback integration to identify vulnerabilities and strengthen defenses effectively. This evolution addresses the gap between isolated attack simulations and defense mechanisms, fostering proactive security improvements through shared insights.
Core Differences: Red Team vs Purple Team
Red Teams simulate real-world cyber attacks to identify vulnerabilities in an organization's security by adopting an adversarial approach. Purple Teams integrate both offensive tactics of Red Teams and defensive strategies of Blue Teams to enhance collaboration, improve threat detection, and accelerate response times. The core difference lies in Red Teams operating independently to test defenses, while Purple Teams foster continuous interaction between attackers and defenders for proactive security improvement.
Collaboration Between Red and Purple Teams
Collaboration between Red and Purple Teams enhances cybersecurity by combining offensive tactics with continuous feedback to improve defense mechanisms. Red Teams simulate real-world attacks while Purple Teams analyze these efforts, fostering a dynamic environment where vulnerabilities are identified and mitigated efficiently. This synergy strengthens organizational resilience by ensuring proactive threat detection and adaptive security strategies.
Tools and Techniques Used by Each Team
Purple Teams leverage collaboration tools like ThreatConnect and attack simulation platforms such as Cobalt Strike to bridge the gap between offense and defense, combining Red Team's adversarial tactics with Blue Team's defensive monitoring techniques. Red Teams predominantly use penetration testing frameworks like Metasploit and custom scripts for exploiting vulnerabilities, focusing on stealth, lateral movement, and persistence to mimic real-world attackers. Meanwhile, Purple Teams emphasize integrated threat intelligence sharing and continuous feedback loops, deploying automated detection tuning and incident response tools to enhance security posture through synchronized efforts.
Benefits of Integrating Purple Teams into Security Programs
Integrating Purple Teams into security programs enhances collaboration between offensive Red Teams and defensive Blue Teams, leading to more comprehensive threat detection and mitigation strategies. This synergy accelerates vulnerability identification and remediation by combining attack simulation insights with real-time defense improvements. Organizations benefit from increased security posture resilience and reduced incident response times through continuous feedback loops and shared expertise.
Common Challenges in Red and Purple Team Engagements
Common challenges in Red and Purple Team engagements include difficulties in communication and alignment of objectives between offensive and defensive teams, which often leads to misinterpretation of findings and delayed mitigation efforts. Another significant issue is the lack of standardized metrics and reporting frameworks, making it harder to measure progress and effectiveness of security controls. Limited resources and expertise also hamper sustained collaboration, reducing the overall impact of security testing and incident response initiatives.
Measuring Success in Purple and Red Team Assessments
Measuring success in Purple Team assessments hinges on the effective collaboration between Red Team attackers and Blue Team defenders, emphasizing improved detection, response times, and fortified security controls. Red Team success is evaluated through the extent of undetected breaches, exploitation of vulnerabilities, and the ability to simulate real-world attack techniques that expose security gaps. Key metrics include incident response improvements, reduction in dwell time, enhanced threat intelligence sharing, and strengthened organizational resilience against cyber threats.
Future Trends in Cybersecurity Team Strategies
Purple Team strategies are evolving to integrate advanced AI-driven analytics and automated threat detection, enhancing collaboration between offensive Red Team tactics and defensive Blue Team measures. Future cybersecurity teams will emphasize continuous real-time feedback loops and adaptive learning systems to anticipate and neutralize emerging threats more efficiently. The convergence of machine learning with human expertise is set to redefine vulnerability assessments and incident response protocols in Red and Purple Team operations.
Purple Team Infographic
 libterm.com
libterm.com