Zero Trust Architecture eliminates implicit trust by verifying every user and device before granting access to resources, minimizing security risks in modern networks. It employs strict access controls, continuous monitoring, and segmentation to protect sensitive data from cyber threats. Explore the rest of the article to understand how Zero Trust can enhance Your organization's cybersecurity framework.
Table of Comparison
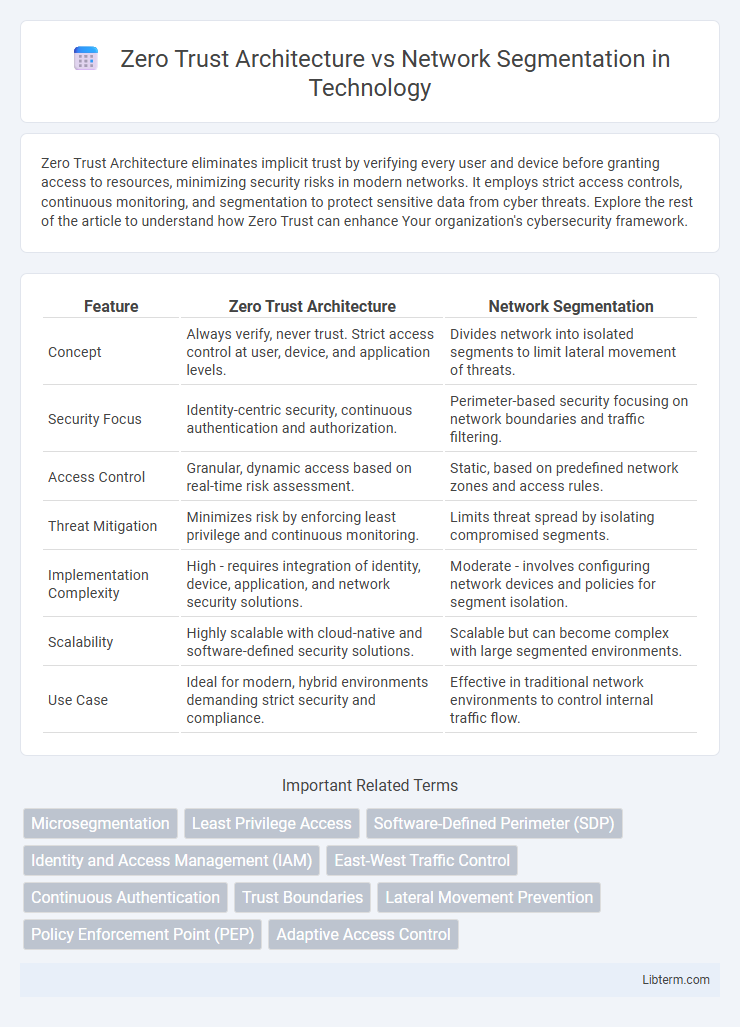
| Feature | Zero Trust Architecture | Network Segmentation |
|---|---|---|
| Concept | Always verify, never trust. Strict access control at user, device, and application levels. | Divides network into isolated segments to limit lateral movement of threats. |
| Security Focus | Identity-centric security, continuous authentication and authorization. | Perimeter-based security focusing on network boundaries and traffic filtering. |
| Access Control | Granular, dynamic access based on real-time risk assessment. | Static, based on predefined network zones and access rules. |
| Threat Mitigation | Minimizes risk by enforcing least privilege and continuous monitoring. | Limits threat spread by isolating compromised segments. |
| Implementation Complexity | High - requires integration of identity, device, application, and network security solutions. | Moderate - involves configuring network devices and policies for segment isolation. |
| Scalability | Highly scalable with cloud-native and software-defined security solutions. | Scalable but can become complex with large segmented environments. |
| Use Case | Ideal for modern, hybrid environments demanding strict security and compliance. | Effective in traditional network environments to control internal traffic flow. |
Introduction to Zero Trust Architecture and Network Segmentation
Zero Trust Architecture (ZTA) is a cybersecurity framework that requires strict identity verification for every user and device attempting to access resources within a network, minimizing implicit trust and reducing breach risks. Network segmentation divides a larger network into smaller, isolated segments to limit unauthorized lateral movement and contain potential threats. Both strategies enhance security by controlling access and minimizing attack surfaces, but ZTA emphasizes continuous verification while network segmentation focuses on structural isolation.
Core Principles of Zero Trust Architecture
Zero Trust Architecture (ZTA) emphasizes continuous verification, strict access controls, and the principle of least privilege to minimize trust zones within a network environment. Unlike traditional Network Segmentation, which primarily divides the network into isolated segments to contain breaches, ZTA enforces identity-based and device-centric authentication at every access request. Core principles of ZTA include verifying explicit identity, enforcing policy consistency, and assuming breach to reduce attack surfaces and prevent lateral movement.
Fundamentals of Network Segmentation
Network segmentation involves dividing a computer network into smaller, isolated segments to improve security and performance by limiting lateral movement of threats and controlling traffic flow between segments. Unlike Zero Trust Architecture, which continuously verifies trust regardless of network location, network segmentation focuses on establishing secure zones within a network based on predefined security policies. Fundamentals of network segmentation include creating secure boundaries with firewalls or VLANs, enforcing access controls at segment levels, and monitoring inter-segment traffic to detect and prevent unauthorized access.
Key Differences Between Zero Trust and Network Segmentation
Zero Trust Architecture enforces continuous verification of user identity and device trustworthiness regardless of network location, while Network Segmentation divides the network into isolated segments to limit lateral movement. Zero Trust operates on a "never trust, always verify" principle requiring strict access controls and real-time monitoring, whereas Network Segmentation primarily relies on firewall rules and access controls at network boundaries. The key difference lies in Zero Trust's comprehensive identity-centric security approach contrasted with Network Segmentation's focus on reducing attack surface through infrastructure separation.
Security Strengths of Zero Trust Architecture
Zero Trust Architecture (ZTA) enhances security by verifying every user and device continuously, regardless of their location, eliminating implicit trust within the network. Unlike traditional network segmentation, ZTA employs granular access controls and real-time monitoring to prevent lateral movement and reduce the risk of insider threats. Its dynamic policy enforcement and multi-factor authentication provide stronger protection against advanced cyberattacks and data breaches.
Advantages and Limitations of Network Segmentation
Network segmentation enhances security by dividing a network into isolated segments, minimizing lateral movement of threats and containing potential breaches. It improves performance through traffic management and limits access to sensitive data, but its complexity can increase administrative overhead and may require significant upfront configuration and maintenance. While effective in reducing attack surfaces, network segmentation alone cannot fully prevent advanced threats without complementary strategies like Zero Trust Architecture.
Implementation Challenges: Zero Trust vs Network Segmentation
Implementing Zero Trust Architecture demands continuous authentication and granular access controls across all users and devices, which can strain existing IT resources and require significant cultural shifts within organizations. Network segmentation, while more straightforward, presents challenges in correctly defining and maintaining boundary policies to prevent lateral movement of threats without impeding network performance. Both approaches require comprehensive visibility and monitoring, but Zero Trust's dynamic enforcement imposes higher complexity and integration demands compared to the static nature of traditional network segmentation.
Use Cases and Real-World Applications
Zero Trust Architecture (ZTA) enhances security by continuously verifying user identity and device trustworthiness, making it ideal for cloud environments and remote workforces where perimeter defenses are insufficient. Network segmentation limits lateral movement by dividing a network into isolated zones, commonly used in data centers and industrial control systems to contain breaches and protect sensitive assets. Combining ZTA with network segmentation enables granular access control and micro-segmentation, improving threat detection and minimizing attack surfaces in complex enterprise networks.
Integrating Zero Trust with Network Segmentation Strategies
Integrating Zero Trust Architecture with Network Segmentation enhances cybersecurity by enforcing strict access controls and minimizing lateral movement within a network. Zero Trust leverages continuous verification and least privilege principles, while network segmentation divides the infrastructure into isolated zones, reducing attack surfaces and containing breaches effectively. Combining these strategies ensures granular policy enforcement and improved threat detection, creating a robust defense-in-depth approach for enterprise environments.
Future Trends in Network Security Approaches
Zero Trust Architecture (ZTA) prioritizes continuous verification and granular access controls, emerging as a dominant future trend over traditional Network Segmentation that mainly relies on perimeter defenses. Advanced machine learning and AI-driven analytics within ZTA enhance threat detection and response, offering adaptive security models tailored to dynamic cloud and hybrid environments. The convergence of ZTA with micro-segmentation techniques promises more resilient, scalable network security frameworks designed to counter sophisticated cyber threats and insider risks.
Zero Trust Architecture Infographic
 libterm.com
libterm.com