OAuth2 Resource Owner Password Credentials Flow allows users to directly provide their username and password to an application, which then uses these credentials to obtain an access token from the authorization server. This flow is suitable for trusted applications where the resource owner has a high degree of confidence in the client, minimizing redirect complexity. Explore the rest of the article to understand when and how to implement this flow securely for your applications.
Table of Comparison
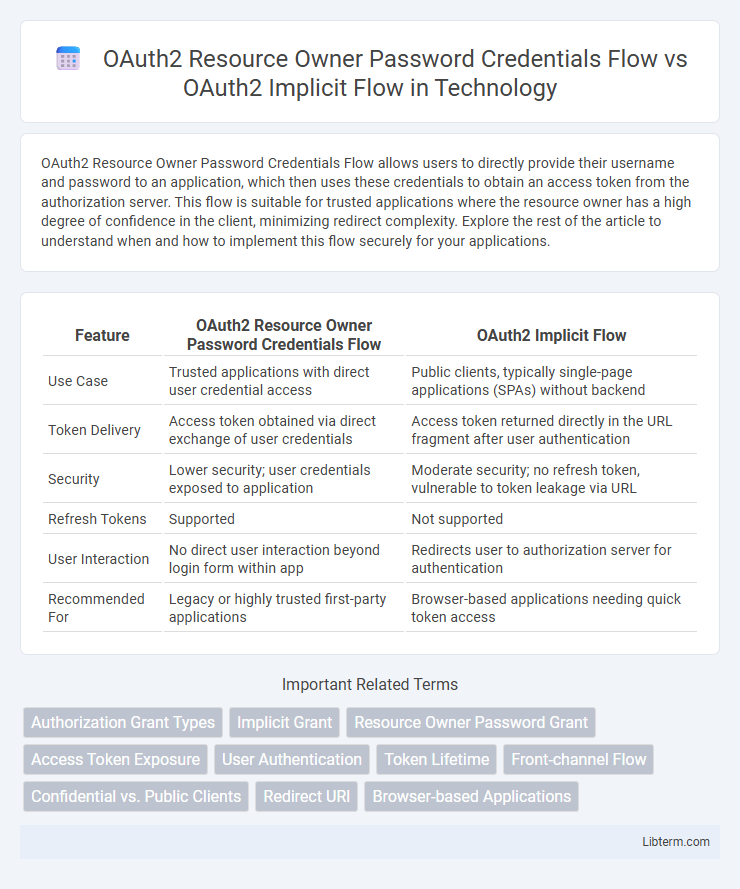
| Feature | OAuth2 Resource Owner Password Credentials Flow | OAuth2 Implicit Flow |
|---|---|---|
| Use Case | Trusted applications with direct user credential access | Public clients, typically single-page applications (SPAs) without backend |
| Token Delivery | Access token obtained via direct exchange of user credentials | Access token returned directly in the URL fragment after user authentication |
| Security | Lower security; user credentials exposed to application | Moderate security; no refresh token, vulnerable to token leakage via URL |
| Refresh Tokens | Supported | Not supported |
| User Interaction | No direct user interaction beyond login form within app | Redirects user to authorization server for authentication |
| Recommended For | Legacy or highly trusted first-party applications | Browser-based applications needing quick token access |
Introduction to OAuth2 Flows
OAuth2 Resource Owner Password Credentials Flow allows a client application to directly obtain user credentials to request an access token, primarily used in highly trusted applications. OAuth2 Implicit Flow, designed for single-page applications, provides access tokens directly without exchanging authorization codes, reducing backend server involvement but increasing exposure risk. Both flows serve distinct purposes within OAuth2 protocols, emphasizing trade-offs in security and user experience during authorization.
What is Resource Owner Password Credentials Flow?
Resource Owner Password Credentials (ROPC) Flow in OAuth2 allows an application to directly obtain an access token by using the resource owner's username and password, bypassing the standard authorization grant process. This flow is typically used in highly trusted applications, such as first-party clients, where collecting user credentials is secure and acceptable. ROPC grants access tokens without requiring user interaction, but it poses higher security risks by exposing user credentials to the client application.
Understanding the Implicit Flow
OAuth2 Implicit Flow is designed for public clients like single-page applications where client secrets cannot be securely stored, enabling the client to receive tokens directly from the authorization endpoint without an intermediate authorization code. This flow reduces the number of steps compared to Resource Owner Password Credentials Flow, which requires user credentials to be handled directly by the client, increasing security risks. Token exposure in Implicit Flow is mitigated using short-lived access tokens and secure communication channels, but it is generally recommended to use Authorization Code Flow with PKCE for enhanced security.
Core Differences Between Resource Owner Password and Implicit Flow
OAuth2 Resource Owner Password Credentials Flow involves directly exchanging user credentials (username and password) for an access token, making it suitable for highly trusted applications but posing security risks if misused. In contrast, OAuth2 Implicit Flow grants tokens via redirection without exposing user credentials, designed primarily for client-side web applications where maintaining secret confidentiality is challenging. The core difference lies in credential handling: Resource Owner Password Flow requires user credentials, while Implicit Flow relies on browser-based token retrieval without sharing passwords, impacting security and use case suitability.
Security Considerations for Each Flow
The OAuth2 Resource Owner Password Credentials Flow requires clients to handle user credentials directly, increasing the risk of credential exposure and necessitating strict security measures such as secure storage and transmission. The OAuth2 Implicit Flow avoids direct credential handling by issuing tokens via browser redirects but remains vulnerable to token interception through malicious scripts or unsecured URLs, making token expiration and secure token storage critical. Both flows demand rigorous implementation of HTTPS, scope limitations, and token revocation capabilities to mitigate security threats inherent in their designs.
Use Cases: When to Use Resource Owner Password Flow
The OAuth2 Resource Owner Password Credentials Flow is best suited for highly trusted applications, such as first-party mobile or desktop apps, where the user has a direct relationship with the application and can safely share their credentials. This flow enables the app to exchange username and password directly for an access token, making it useful in legacy systems or secure enterprise environments where seamless authentication is needed without redirecting the user. In contrast, the Implicit Flow is designed primarily for browser-based single-page applications where the access token is obtained directly from the authorization endpoint without exposing user credentials.
Use Cases: When to Use Implicit Flow
OAuth2 Implicit Flow is designed for single-page applications (SPAs) and public clients where storing client secrets securely is challenging, enabling direct token issuance in the browser without a backend server. It is suitable when minimizing round-trips to the authorization server is critical, and applications require fast, seamless user authentication without exposing sensitive credentials. This flow is ideal for use cases like JavaScript-based web apps that need immediate access tokens for API calls without involving client-side secret management or server-side code.
Deprecation and Industry Best Practices
OAuth2 Resource Owner Password Credentials Flow is deprecated due to inherent security risks of handling user credentials directly by clients, while OAuth2 Implicit Flow is discouraged because it exposes tokens in the front channel, increasing vulnerability to interception. Industry best practices now recommend using OAuth2 Authorization Code Flow with PKCE for enhanced security, as it mitigates risks associated with token leakage and client authentication. The OAuth 2.1 specification consolidates these guidelines by removing support for deprecated flows and reinforcing secure token exchange methodologies.
Alternatives to Resource Owner Password and Implicit Flow
OAuth2 Resource Owner Password Credentials Flow is considered less secure due to direct handling of user credentials, making it less recommended for modern applications. Alternatives like Authorization Code Flow with PKCE provide enhanced security by exchanging authorization codes and avoiding exposing tokens to user agents. The Implicit Flow, previously common for single-page applications, has largely been replaced by Authorization Code Flow with PKCE, which mitigates token leakage risks and supports secure token management in browser-based environments.
Conclusion: Choosing the Right OAuth2 Flow
The OAuth2 Resource Owner Password Credentials Flow suits highly trusted applications like first-party mobile apps where direct user credentials access is viable, offering streamlined authentication but raising security risks if mishandled. OAuth2 Implicit Flow, designed primarily for browser-based apps without a backend server, avoids exposing client secrets but risks token interception due to its reliance on front-channel transmission. Selecting the right OAuth2 flow depends on the application architecture and security context: use Resource Owner Password Credentials Flow for secure, trusted environments and Implicit Flow for public clients requiring minimal backend involvement.
OAuth2 Resource Owner Password Credentials Flow Infographic
 libterm.com
libterm.com