OAuth 2.0 is a widely used authorization framework that enables applications to obtain limited access to user accounts on HTTP services securely. It allows users to grant third-party applications access to their resources without sharing their passwords, enhancing security and user experience. Discover how OAuth 2.0 works and why it's essential for modern web and mobile app security in the rest of this article.
Table of Comparison
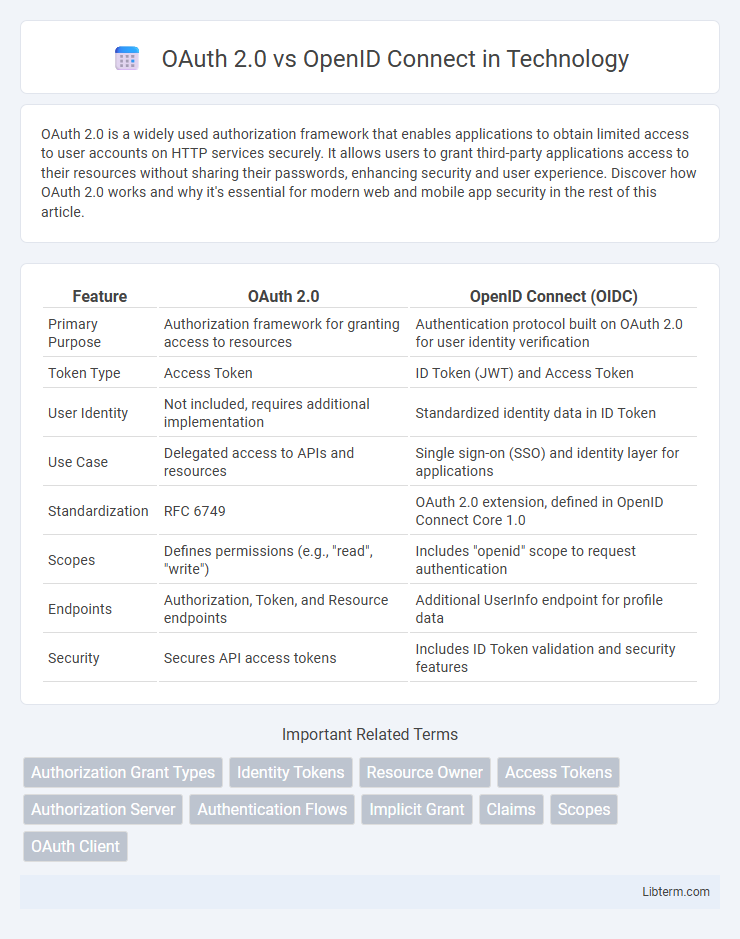
| Feature | OAuth 2.0 | OpenID Connect (OIDC) |
|---|---|---|
| Primary Purpose | Authorization framework for granting access to resources | Authentication protocol built on OAuth 2.0 for user identity verification |
| Token Type | Access Token | ID Token (JWT) and Access Token |
| User Identity | Not included, requires additional implementation | Standardized identity data in ID Token |
| Use Case | Delegated access to APIs and resources | Single sign-on (SSO) and identity layer for applications |
| Standardization | RFC 6749 | OAuth 2.0 extension, defined in OpenID Connect Core 1.0 |
| Scopes | Defines permissions (e.g., "read", "write") | Includes "openid" scope to request authentication |
| Endpoints | Authorization, Token, and Resource endpoints | Additional UserInfo endpoint for profile data |
| Security | Secures API access tokens | Includes ID Token validation and security features |
Introduction to OAuth 2.0 and OpenID Connect
OAuth 2.0 is an authorization framework that enables third-party applications to obtain limited access to user resources without exposing credentials, relying on access tokens for delegated permissions. OpenID Connect builds on OAuth 2.0 by adding an identity layer, allowing clients to verify the user's identity and obtain profile information through standardized ID tokens. Both protocols enhance secure authentication and authorization processes across modern web and mobile applications.
Core Concepts of OAuth 2.0
OAuth 2.0 is an authorization framework that enables third-party applications to obtain limited access to user resources on a server without exposing user credentials by using access tokens. It defines core concepts such as authorization grants, including authorization code, implicit, resource owner password credentials, and client credentials flows, which specify different methods for obtaining access tokens. The framework distinguishes roles like resource owner, client, authorization server, and resource server to securely manage and validate access permissions.
Fundamentals of OpenID Connect
OpenID Connect builds on the OAuth 2.0 framework by adding an identity layer that enables clients to verify the end user's authentication and obtain profile information through standardized ID tokens. It uses JSON Web Tokens (JWT) to securely transmit user details, enhancing OAuth 2.0's authorization capabilities with authentication features. This protocol supports single sign-on (SSO) and federation, making it a robust solution for both identity verification and authorization in modern applications.
Key Differences Between OAuth 2.0 and OpenID Connect
OAuth 2.0 is an authorization framework that allows third-party applications to obtain limited access to user resources without exposing credentials, while OpenID Connect extends OAuth 2.0 by adding an identity layer that provides authentication and user profile information via ID tokens. OAuth 2.0 focuses solely on delegated access control, whereas OpenID Connect enables clients to verify user identity and obtain standardized claims such as name and email. This key difference makes OpenID Connect ideal for Single Sign-On (SSO) solutions, combining both authentication and authorization capabilities.
Use Cases: When to Use OAuth 2.0 vs OpenID Connect
OAuth 2.0 is primarily used for delegated authorization, granting third-party applications limited access to user resources without exposing credentials, making it ideal for API access and resource sharing scenarios. OpenID Connect builds on OAuth 2.0 by adding an identity layer that enables authentication, enabling single sign-on (SSO) and user identity verification across applications. Choose OAuth 2.0 when you need to authorize access without user authentication, and OpenID Connect when authentication and identity management are required alongside authorization.
Security Implications and Best Practices
OAuth 2.0 provides authorization by issuing limited access tokens to third-party applications without exposing user credentials, but it lacks built-in authentication, which can lead to security risks like token interception and replay attacks. OpenID Connect extends OAuth 2.0 by adding an identity layer using ID tokens, enabling secure user authentication with features such as nonce values to prevent token reuse and claims to verify user identity. Best practices include implementing secure token storage, using HTTPS to protect token transmission, validating ID and access tokens, and employing scopes and audience restrictions to minimize privileges and reduce attack surfaces.
Token Types: Access, ID, and Refresh Tokens
OAuth 2.0 primarily issues Access Tokens to grant client applications limited access to user resources on a resource server, while OpenID Connect extends OAuth 2.0 by introducing ID Tokens to authenticate users and provide details about their identity. Refresh Tokens, supported by both OAuth 2.0 and OpenID Connect, enable clients to obtain new Access Tokens without requiring the user to re-authenticate, enhancing session continuity and security. The ID Token in OpenID Connect is a JSON Web Token (JWT) containing user claims, distinguishing it from OAuth 2.0's Access Token, which primarily serves authorization purposes.
Implementation Workflows and Protocol Flows
OAuth 2.0 primarily facilitates authorization through flows like Authorization Code, Implicit, Client Credentials, and Resource Owner Password Credentials, enabling applications to obtain limited access tokens for protected resources. OpenID Connect builds on OAuth 2.0 by adding an identity layer using ID tokens and introduces specialized flows such as the Hybrid Flow that combines authorization and authentication. Implementation workflows for OpenID Connect require handling user authentication, session management, and token validation, while OAuth 2.0 focuses on delegated access and token issuance without defining user identity details.
Popular Providers and Real-World Examples
OAuth 2.0 is widely adopted by providers such as Google, Facebook, and Microsoft for delegated authorization, allowing third-party apps to access user resources without sharing credentials. OpenID Connect, built on OAuth 2.0, adds an identity layer and is implemented by providers like Google and Apple to enable secure user authentication and single sign-on across multiple platforms. Real-world examples include Google's use of OAuth 2.0 for Google Drive access and OpenID Connect for signing into Google services, while Microsoft uses OAuth 2.0 for Azure resource access and OpenID Connect for Microsoft 365 authentication.
Conclusion: Choosing the Right Protocol for Your Needs
OAuth 2.0 excels in authorization by granting third-party applications controlled access to user resources without exposing credentials. OpenID Connect builds on OAuth 2.0, offering robust authentication and identity verification alongside authorization, ideal for applications requiring user identity management. Selecting the right protocol depends on whether your primary need is secure resource authorization (OAuth 2.0) or user authentication and identity assurance (OpenID Connect).
OAuth 2.0 Infographic
 libterm.com
libterm.com