OAuth is a widely adopted authorization framework that enables secure third-party applications to access user resources without sharing passwords. It enhances online security by allowing users to grant limited access to their information while maintaining control over their data. Discover how OAuth can safeguard Your digital interactions and streamline authentication in the rest of this article.
Table of Comparison
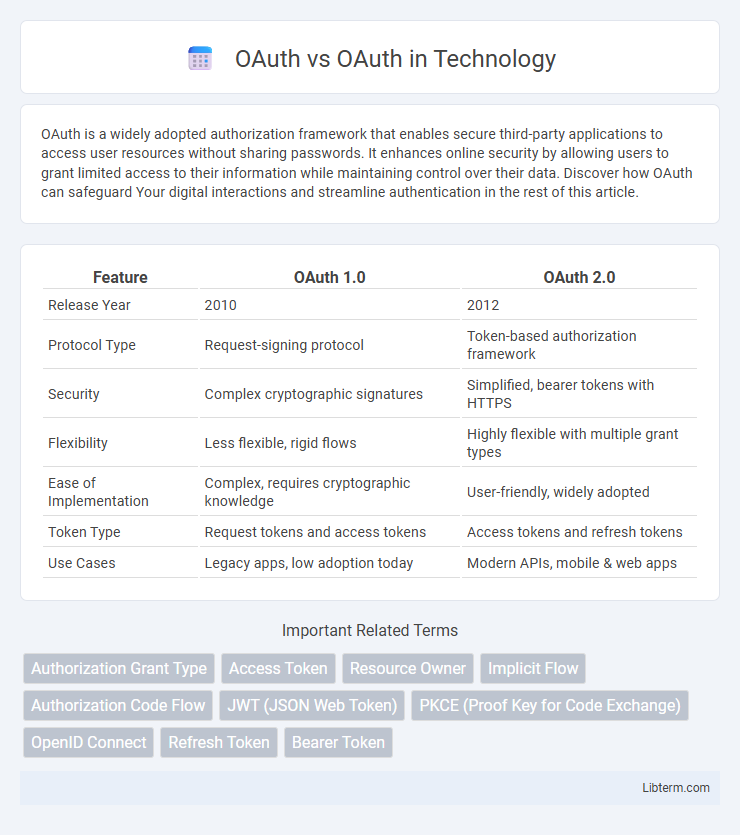
| Feature | OAuth 1.0 | OAuth 2.0 |
|---|---|---|
| Release Year | 2010 | 2012 |
| Protocol Type | Request-signing protocol | Token-based authorization framework |
| Security | Complex cryptographic signatures | Simplified, bearer tokens with HTTPS |
| Flexibility | Less flexible, rigid flows | Highly flexible with multiple grant types |
| Ease of Implementation | Complex, requires cryptographic knowledge | User-friendly, widely adopted |
| Token Type | Request tokens and access tokens | Access tokens and refresh tokens |
| Use Cases | Legacy apps, low adoption today | Modern APIs, mobile & web apps |
Understanding OAuth: An Overview
OAuth is an open standard for access delegation commonly used to grant websites or applications limited access to user information without exposing passwords. It operates through token-based authentication, enabling secure authorization between different services by issuing access tokens with defined scopes and lifetimes. Understanding OAuth involves recognizing its key roles: resource owner, client, authorization server, and resource server, which collectively facilitate secure and efficient third-party access management.
The Evolution of OAuth: OAuth 1.0 vs OAuth 2.0
OAuth 1.0 introduced a complex protocol requiring cryptographic signatures to ensure secure authorization, emphasizing strict message signing and token exchange mechanisms. OAuth 2.0 evolved into a more flexible framework, simplifying development by using bearer tokens and supporting various grant types suitable for web, mobile, and desktop applications. Enhanced security features, reduced complexity, and broader adoption highlight the critical differences between OAuth 1.0 and OAuth 2.0 in modern authentication and authorization systems.
Key Concepts in OAuth Authentication
OAuth authentication revolves around key concepts such as resource owner, client, authorization server, and resource server, enabling secure delegated access. Access tokens issued by the authorization server allow clients to access protected resources without exposing user credentials. Scopes define the extent of access granted, ensuring precise permission management within OAuth workflows.
Security Mechanisms: OAuth 1.0 Compared to OAuth 2.0
OAuth 1.0 employs complex cryptographic signatures and requires client-side key management to ensure message integrity and authentication, making its security model stringent but harder to implement. OAuth 2.0, while more flexible and easier to implement, relies primarily on TLS/SSL for transport security and introduces diverse authorization flows to accommodate various client types, increasing usability but potentially expanding attack surfaces if not properly configured. Understanding the fundamental differences in token management, signature requirements, and reliance on transport security highlights the evolution in security mechanisms from OAuth 1.0 to OAuth 2.0.
Differences in Token Handling and Encryption
OAuth 2.0 improves token handling by introducing access tokens and refresh tokens, allowing for better security and flexibility compared to OAuth 1.0's single token approach. OAuth 2.0 supports stronger encryption standards, utilizing HTTPS for token transmission, while OAuth 1.0 relies on cryptographic signatures for securing requests. The use of bearer tokens in OAuth 2.0 simplifies token management but emphasizes the importance of transport-layer security to prevent token leakage.
Use Cases for OAuth 1.0 and OAuth 2.0
OAuth 1.0 is primarily used in legacy applications requiring secure API authorization with cryptographic signatures and is suitable for server-to-server authentication where token confidentiality is critical. OAuth 2.0, on the other hand, dominates modern web and mobile applications by providing flexible authorization flows like authorization code and implicit grants, enhancing user experience with simplified token handling and broader support for delegated access. Use cases for OAuth 2.0 include single sign-on (SSO), third-party access to APIs, and integration with identity providers, making it the preferred choice for scalable, user-centric authorization in contemporary systems.
Implementation Complexity: OAuth 1.0 vs OAuth 2.0
OAuth 1.0 features a more complex implementation due to its reliance on cryptographic signatures for every request, which requires careful handling of keys and tokens. OAuth 2.0 streamlines the process by using bearer tokens and does not require cryptographic signing, significantly reducing development effort and simplifying client-server interactions. The simplified token management and greater flexibility of OAuth 2.0 have made it the preferred protocol for modern web and mobile application authentication.
Vulnerabilities and Threats in Each OAuth Version
OAuth 1.0 relies on cryptographic signatures, which offer strong security but require complex implementation, increasing the risk of misconfiguration and replay attacks. OAuth 2.0 simplifies token usage with bearer tokens, making it more susceptible to token interception and injection attacks if transport security (HTTPS) is not strictly enforced. Threats common to both include token leakage, improper token revocation, and open redirect vulnerabilities, underscoring the importance of secure token handling and authorization flows in each OAuth version.
Best Practices for Securing OAuth Integrations
Implementing OAuth securely involves using short-lived tokens and enforcing the use of Proof Key for Code Exchange (PKCE) to prevent authorization code interception. Regularly rotating client secrets and employing scopes to limit token permissions reduce the risk of excessive access and breaches. Monitoring OAuth token usage with real-time logging and anomaly detection enables prompt identification and mitigation of unauthorized activities.
Choosing the Right OAuth Version for Your Application
Choosing the right OAuth version for your application depends on security needs and compatibility requirements. OAuth 2.0 is widely adopted for its flexibility, supporting various grant types and modern features like token scopes and refresh tokens, making it ideal for most web and mobile applications. OAuth 1.0a offers robust message-level security with cryptographic signatures but is more complex and less commonly used in new implementations.
OAuth Infographic
 libterm.com
libterm.com