SAML 2.0 is a widely adopted open standard for single sign-on (SSO) that enables secure exchange of authentication and authorization data between identity providers and service providers. It enhances security by allowing users to access multiple applications with one set of credentials, reducing password fatigue and improving user experience. Discover how SAML 2.0 can streamline your authentication processes by reading the rest of the article.
Table of Comparison
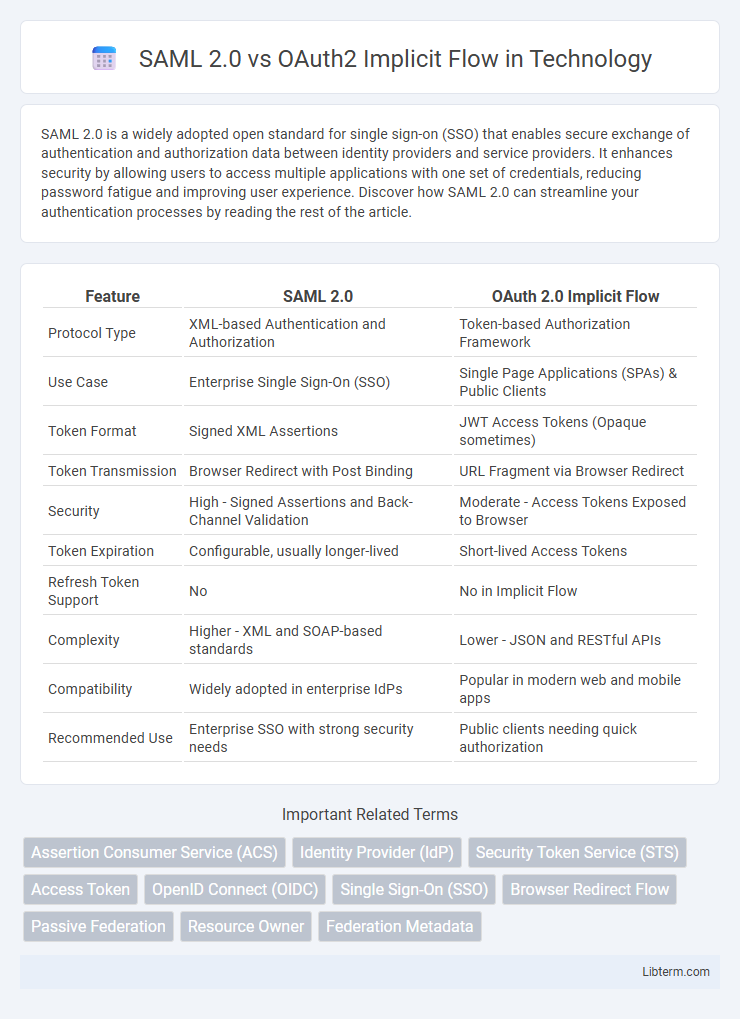
| Feature | SAML 2.0 | OAuth 2.0 Implicit Flow |
|---|---|---|
| Protocol Type | XML-based Authentication and Authorization | Token-based Authorization Framework |
| Use Case | Enterprise Single Sign-On (SSO) | Single Page Applications (SPAs) & Public Clients |
| Token Format | Signed XML Assertions | JWT Access Tokens (Opaque sometimes) |
| Token Transmission | Browser Redirect with Post Binding | URL Fragment via Browser Redirect |
| Security | High - Signed Assertions and Back-Channel Validation | Moderate - Access Tokens Exposed to Browser |
| Token Expiration | Configurable, usually longer-lived | Short-lived Access Tokens |
| Refresh Token Support | No | No in Implicit Flow |
| Complexity | Higher - XML and SOAP-based standards | Lower - JSON and RESTful APIs |
| Compatibility | Widely adopted in enterprise IdPs | Popular in modern web and mobile apps |
| Recommended Use | Enterprise SSO with strong security needs | Public clients needing quick authorization |
Introduction to SAML 2.0 and OAuth2 Implicit Flow
SAML 2.0 (Security Assertion Markup Language) is an XML-based protocol used primarily for single sign-on (SSO) in enterprise environments, enabling secure exchange of authentication and authorization data between identity providers and service providers. OAuth2 Implicit Flow is an authorization framework designed for mobile and web applications, allowing clients to obtain access tokens directly from the authorization server without exposing client secrets. Both protocols facilitate user authentication and authorization but serve different use cases, with SAML 2.0 emphasizing enterprise SSO and OAuth2 Implicit Flow focusing on delegated authorization in client-side applications.
Core Principles of SAML 2.0
SAML 2.0 operates on core principles of secure token exchange, enabling single sign-on (SSO) through XML-based assertions that authenticate users between identity providers and service providers. It emphasizes trust and integrity via digital signatures and encryption, ensuring federated identity management across domains. Unlike OAuth2 Implicit Flow, which focuses on delegated authorization and token handling in browser-based apps, SAML 2.0 targets robust authentication using standardized protocols for identity assertion.
Key Concepts Behind OAuth2 Implicit Flow
OAuth2 Implicit Flow is designed for public clients, such as single-page applications, where tokens are issued directly to the client without an intermediate authorization code, optimizing for reduced latency. It relies on the authorization endpoint to obtain access tokens through URL fragments, enhancing responsiveness but posing security risks due to exposure of tokens in the browser. Key concepts include token issuance without client authentication, reliance on bearer tokens, and short-lived access tokens to mitigate potential token leakage.
Authentication vs Authorization: Clarifying the Difference
SAML 2.0 primarily handles authentication by enabling secure identity assertions between an identity provider and service provider, ensuring users are who they claim to be. OAuth2 Implicit Flow focuses on authorization, allowing clients to obtain access tokens to perform actions on behalf of the user without directly verifying their identity. Understanding that SAML 2.0 verifies identity while OAuth2 Implicit Flow grants delegated access clarifies their distinct roles in secure digital interactions.
Protocol Workflows: SAML 2.0 vs OAuth2 Implicit Flow
SAML 2.0 protocol workflow involves an identity provider (IdP) issuing an XML-based SAML assertion after authenticating the user, which is then sent to the service provider (SP) to grant access, relying heavily on browser redirects and POST bindings. OAuth2 Implicit Flow, designed mainly for single-page applications, issues an access token directly from the authorization server to the client without a back-channel, using URL fragments, which simplifies token delivery but exposes tokens in the browser. The key difference lies in SAML's reliance on XML and signed assertions for secure identity verification, whereas OAuth2 Implicit Flow emphasizes token-based authorization with faster, but less secure, token transmission.
Security Considerations and Vulnerabilities
SAML 2.0 provides robust security through XML-based assertions and strong message signing, reducing susceptibility to token substitution attacks commonly seen in older protocols. OAuth2 Implicit Flow, while streamlined for single-page applications, has notable vulnerabilities including exposure of access tokens in the URL, increasing risks of token leakage via browser history or network interception. Security best practices recommend migrating from OAuth2 Implicit Flow to Authorization Code Flow with PKCE to mitigate these vulnerabilities and enhance token security.
Use Cases for SAML 2.0
SAML 2.0 is primarily used in enterprise environments to enable single sign-on (SSO) for web applications, especially where secure exchange of user authentication and authorization data between identity providers and service providers is crucial. It excels in federated identity scenarios across organizational boundaries, such as between corporate intranets and third-party cloud services. Use cases include employee access to multiple SaaS applications through a centralized identity provider and integration of legacy systems requiring robust authentication standards.
Use Cases for OAuth2 Implicit Flow
OAuth2 Implicit Flow is primarily designed for client-side web applications like single-page apps (SPAs) where maintaining client secrets securely is impractical. It enables users to authenticate quickly and obtain tokens directly from the authorization endpoint without an intermediate code exchange, reducing latency and improving user experience. Use cases include public clients running in browsers or mobile apps requiring immediate access tokens for API calls without back-end server involvement.
Advantages and Limitations of Each Protocol
SAML 2.0 offers robust single sign-on (SSO) capabilities with strong security features, making it ideal for enterprise environments requiring extensive interoperability and assertion-based authentication; however, its complexity can hinder implementation in lightweight or mobile applications. OAuth2 Implicit Flow enables simpler, faster authentication for browser-based and mobile apps by issuing tokens directly to the client without backend exchanges, but it is less secure due to token exposure risks and has been deprecated in favor of Authorization Code Flow with PKCE. Each protocol suits different scenarios: SAML 2.0 excels in secure, enterprise SSO use cases, while OAuth2 Implicit Flow targets user-agent-based applications with faster, though less secure, token issuance.
Choosing the Right Protocol for Your Application
SAML 2.0 excels in enterprise environments requiring robust single sign-on (SSO) capabilities with strong authentication and detailed attribute sharing, making it ideal for web-based applications with established identity providers. OAuth2 Implicit Flow suits modern single-page applications (SPAs) needing rapid token acquisition and efficient authorization without backend server involvement, though it offers less security compared to Authorization Code Flow. Selecting the right protocol depends on factors like application architecture, security requirements, user experience, and whether identity federation or delegated authorization is the primary goal.
SAML 2.0 Infographic
 libterm.com
libterm.com