Implicit Grant is an OAuth 2.0 authorization flow designed for client-side web applications where storing client secrets securely is impractical. It enables your browser-based app to receive access tokens directly from the authorization server without requiring an intermediate authorization code. Explore the rest of the article to understand how the Implicit Grant functions and when to implement it securely.
Table of Comparison
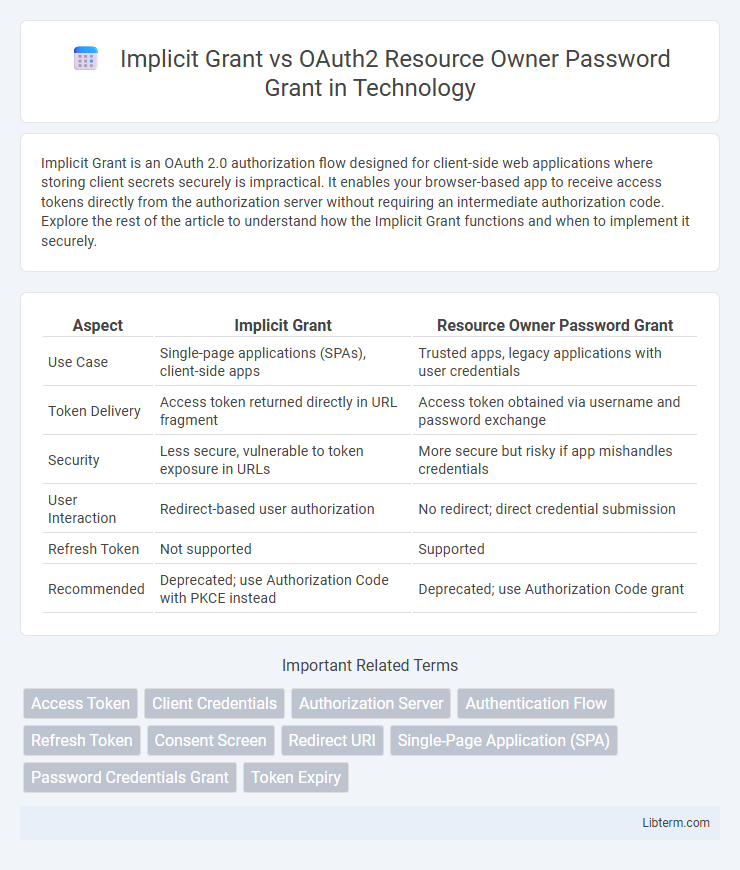
| Aspect | Implicit Grant | Resource Owner Password Grant |
|---|---|---|
| Use Case | Single-page applications (SPAs), client-side apps | Trusted apps, legacy applications with user credentials |
| Token Delivery | Access token returned directly in URL fragment | Access token obtained via username and password exchange |
| Security | Less secure, vulnerable to token exposure in URLs | More secure but risky if app mishandles credentials |
| User Interaction | Redirect-based user authorization | No redirect; direct credential submission |
| Refresh Token | Not supported | Supported |
| Recommended | Deprecated; use Authorization Code with PKCE instead | Deprecated; use Authorization Code grant |
Understanding OAuth2: An Overview
OAuth2 defines multiple grant types for secure authorization, with Implicit Grant designed for public clients like single-page applications, enabling token issuance directly through the user agent without client authentication. Resource Owner Password Grant allows trusted applications to obtain access tokens by directly handling user credentials, making it less secure but useful in legacy or highly trusted environments. Understanding OAuth2 involves recognizing these grants' security implications, token handling methods, and appropriate use cases within an overall authorization framework.
What is the Implicit Grant?
The Implicit Grant is an OAuth 2.0 authorization flow designed for public clients such as single-page applications where client secrets cannot be securely stored. It grants access tokens directly through the browser without an intermediate authorization code exchange, improving speed but reducing security. This flow avoids exposing client credentials by relying on the user agent to receive tokens immediately upon user authorization.
What is the Resource Owner Password Grant?
The Resource Owner Password Grant in OAuth2 allows users to provide their username and password directly to a client application, enabling the client to obtain an access token on their behalf. This grant type is typically used in trusted applications where the user has a high level of confidence in the client, such as first-party apps, and it bypasses the need for redirection to an authorization server. Unlike the Implicit Grant, which is designed for public clients and issues access tokens via browser redirects, the Resource Owner Password Grant relies on direct credential exchange, making it less suitable for third-party applications due to security risks.
Key Differences Between Implicit Grant and Password Grant
The Implicit Grant in OAuth2 is designed for public clients, such as single-page applications, where tokens are directly returned via the browser without intermediate authorization code exchange, prioritizing simplicity over security. In contrast, the Resource Owner Password Grant requires users to provide credentials directly to the client, which then exchanges them for tokens, posing higher security risks but enabling more trusted client applications like first-party apps. Key differences include token delivery method--implicit grant delivers tokens in the URL fragment, while password grant involves direct credential submission--and security considerations, with implicit grant being vulnerable to token exposure and password grant requiring secure handling of user credentials.
Security Considerations: Implicit vs Password Grant
The Implicit Grant in OAuth2 exposes access tokens directly in the URL, increasing vulnerability to interception attacks and token leakage, making it less secure for single-page applications compared to other flows. Resource Owner Password Credentials Grant requires users to share their credentials with the client, raising significant security concerns due to potential credential compromise and lack of user trust. Security best practices recommend avoiding Implicit Grant and Password Grant in favor of Authorization Code Grant with PKCE, which enhances token confidentiality and user credential protection.
Use Cases for Implicit Grant
Implicit Grant is primarily used for single-page applications (SPAs) and mobile apps where the client-side code cannot securely store secrets, enabling direct token acquisition from the authorization server. It allows quick access tokens without the need for an intermediate authorization code, improving user experience in public clients with limited backend components. This grant type suits scenarios requiring immediate user authentication and authorization without backend server involvement, unlike the Resource Owner Password Grant, which requires handling user credentials and is more suitable for trusted applications.
Use Cases for Resource Owner Password Grant
The Resource Owner Password Grant in OAuth2 is primarily used in trusted applications where the user's credentials are securely handled, such as legacy systems or first-party apps with high trust levels. It enables direct exchange of username and password for access tokens, facilitating seamless user authentication without redirecting to a separate authorization server. This grant type is less suitable for third-party clients due to security risks but remains effective for internal applications requiring quick, straightforward access.
Deprecation and Best Practices in Modern OAuth2
The Implicit Grant flow is deprecated in OAuth2 due to security vulnerabilities like exposure of access tokens in URLs, making it unsuitable for modern applications. The Resource Owner Password Grant, while not deprecated, is discouraged because it requires users to share credentials with the client, violating best practices around user privacy and security. Modern OAuth2 implementations favor Authorization Code Grant with PKCE for improved security and compliance with current standards.
Choosing the Right Grant Type for Your Application
Choosing the right grant type for your application depends on the security requirements and client capabilities; the Implicit Grant is ideal for single-page applications (SPAs) where tokens are obtained directly via the browser without server-side code, though it has higher security risks due to exposure of access tokens. The OAuth2 Resource Owner Password Grant requires users to provide credentials directly to the application, suitable for trusted applications with secure backend support but discouraged for third-party clients due to the risk of credential leakage. Evaluating factors like client trust level, token exposure risk, and user experience will guide the selection between these two OAuth2 grant types.
Conclusion: Implicit or Password Grant?
The Implicit Grant is best suited for single-page applications requiring quick access tokens without client secret storage, while the Resource Owner Password Grant allows trusted applications to directly handle user credentials for enhanced security and obtain refresh tokens. Choosing between them depends on the application's trust level and security needs, with the Password Grant favored in confidential clients and Implicit for public clients. Since the Password Grant provides better security measures and token refresh capabilities, it is generally recommended over the Implicit Grant for modern OAuth2 implementations.
Implicit Grant Infographic
 libterm.com
libterm.com