A hash function transforms input data into a fixed-size string of characters, typically a sequence of numbers and letters, which acts as a unique identifier or fingerprint. It plays a crucial role in data security, computer science, and blockchain technology by ensuring data integrity and enabling efficient data retrieval. Explore the rest of this article to understand how hash functions impact your digital security and everyday technology.
Table of Comparison
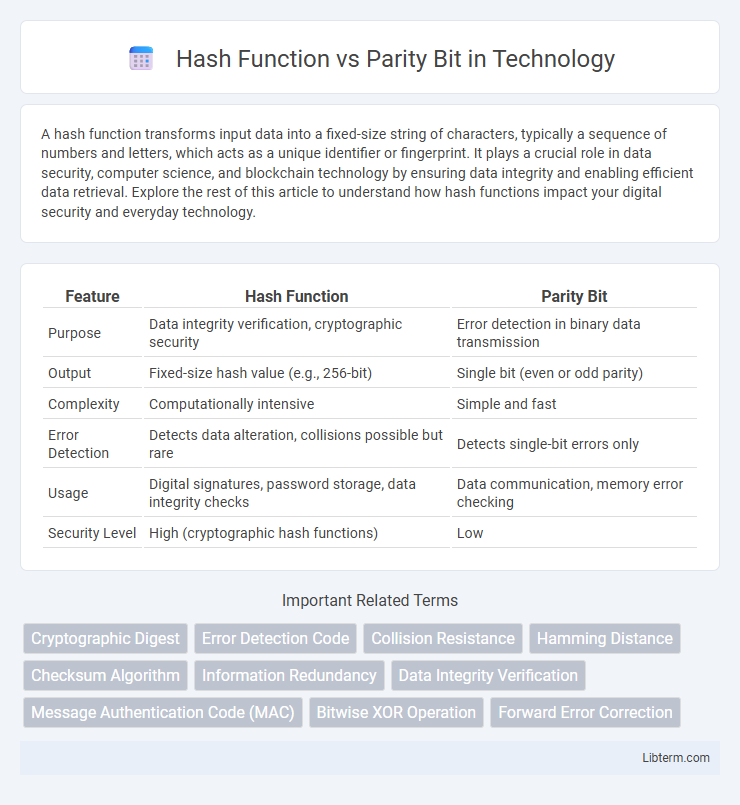
| Feature | Hash Function | Parity Bit |
|---|---|---|
| Purpose | Data integrity verification, cryptographic security | Error detection in binary data transmission |
| Output | Fixed-size hash value (e.g., 256-bit) | Single bit (even or odd parity) |
| Complexity | Computationally intensive | Simple and fast |
| Error Detection | Detects data alteration, collisions possible but rare | Detects single-bit errors only |
| Usage | Digital signatures, password storage, data integrity checks | Data communication, memory error checking |
| Security Level | High (cryptographic hash functions) | Low |
Introduction to Hash Functions and Parity Bits
Hash functions generate fixed-size output values from variable-length input data to accurately verify data integrity and enable quick data retrieval in computing systems. Parity bits serve as simple error-detection mechanisms by appending a single bit to data units to indicate whether the number of set bits is odd or even. Hash functions provide more robust and collision-resistant data verification compared to the basic error-checking capabilities of parity bits.
Fundamental Concepts: What is a Hash Function?
A hash function is a mathematical algorithm that transforms input data of arbitrary size into a fixed-size string of characters, typically a sequence of numbers and letters, known as a hash value or digest. This function is designed to be fast, deterministic, and irreversible, making it crucial for data integrity verification, cryptographic applications, and indexing in data structures. Unlike parity bits that detect single-bit errors through simple binary checksums, hash functions provide comprehensive data fingerprinting with high sensitivity to input changes, ensuring robust data authentication and error detection.
Defining Parity Bits: Basics and Purpose
Parity bits serve as a simple error detection method by adding a single binary digit to data, ensuring the total number of 1s is even (even parity) or odd (odd parity). They help identify single-bit errors during data transmission by verifying parity consistency but cannot detect multiple-bit errors or correct them. Hash functions, by contrast, generate fixed-size output from input data for integrity verification and authentication, offering stronger error detection and collision resistance than parity bits.
Key Differences Between Hash Functions and Parity Bits
Hash functions generate fixed-size, unique hash codes from variable-length input data, ensuring data integrity and authentication in cryptographic applications. Parity bits add a single binary digit to data for simple error detection during transmission, identifying whether an odd or even number of bits have changed. Unlike parity bits, hash functions offer collision resistance, data tampering detection, and are widely used in security protocols, while parity bits serve basic error-checking without cryptographic strength.
Applications of Hash Functions in Data Security
Hash functions are fundamental in data security, enabling password hashing, data integrity verification, and digital signatures by converting input data into fixed-size, unique hash values. Unlike parity bits, which only detect simple errors in a single bit of data, hash functions provide robust protection against tampering and ensure authenticity in secure communications. Their applications extend to blockchain technology, secure file storage, and cryptographic protocols, highlighting their critical role in modern cybersecurity.
Use Cases for Parity Bits in Error Detection
Parity bits serve as a simple and efficient error detection method in digital communication and memory systems by appending a single bit to data to indicate even or odd parity. They are commonly used in hardware-level error detection such as in RAM modules, serial communication protocols, and storage devices where rapid identification of single-bit errors is critical. Unlike hash functions that generate unique fixed-size digests for data integrity and cryptographic applications, parity bits provide a lightweight mechanism focused primarily on detecting basic transmission errors.
Strengths and Limitations of Hash Functions
Hash functions provide robust data integrity verification by producing fixed-size outputs from variable-length inputs, enabling efficient detection of accidental or intentional data changes. Their strength lies in collision resistance and rapid computation, making them suitable for cryptographic applications and error detection beyond simple parity checks. However, hash functions can be vulnerable to sophisticated collision attacks and do not inherently pinpoint the location of errors, unlike parity bits which are limited to detecting single-bit errors but offer immediate error localization.
Advantages and Drawbacks of Parity Bits
Parity bits provide a simple and low-overhead error detection method by adding a single bit to data to indicate whether the number of set bits is even or odd, which helps identify single-bit errors efficiently. However, parity bits cannot detect multi-bit errors or correct any errors, limiting their reliability for complex data integrity needs. Their simplicity and minimal computational cost make them suitable for basic error checking but less effective compared to hash functions for comprehensive data verification.
Choosing Between Hash Functions and Parity Bits
Choosing between hash functions and parity bits depends on the required error detection strength and computational resources. Hash functions offer robust data integrity verification by generating unique fixed-size outputs for variable inputs, suitable for secure applications, while parity bits provide a simple, low-overhead method for single-bit error detection in data transmission. Selecting hash functions is optimal for complex data validation, whereas parity bits excel in real-time error checking with minimal processing.
Conclusion: Hash Functions vs Parity Bits in Modern Computing
Hash functions offer superior data integrity verification compared to parity bits by providing strong cryptographic security and detecting a wider range of errors, including complex data manipulations. Parity bits, limited to single-bit error detection, are efficient for simple error checking but insufficient for modern computing needs where data authenticity and tamper resistance are critical. Consequently, hash functions are the preferred choice for ensuring data integrity and security in contemporary digital environments.
Hash Function Infographic
 libterm.com
libterm.com