Encrypted data ensures your sensitive information remains protected from unauthorized access by converting it into unreadable code. This process is essential for maintaining privacy and securing communications across digital platforms. Discover how encryption works and why it is crucial for safeguarding your digital life in the rest of this article.
Table of Comparison
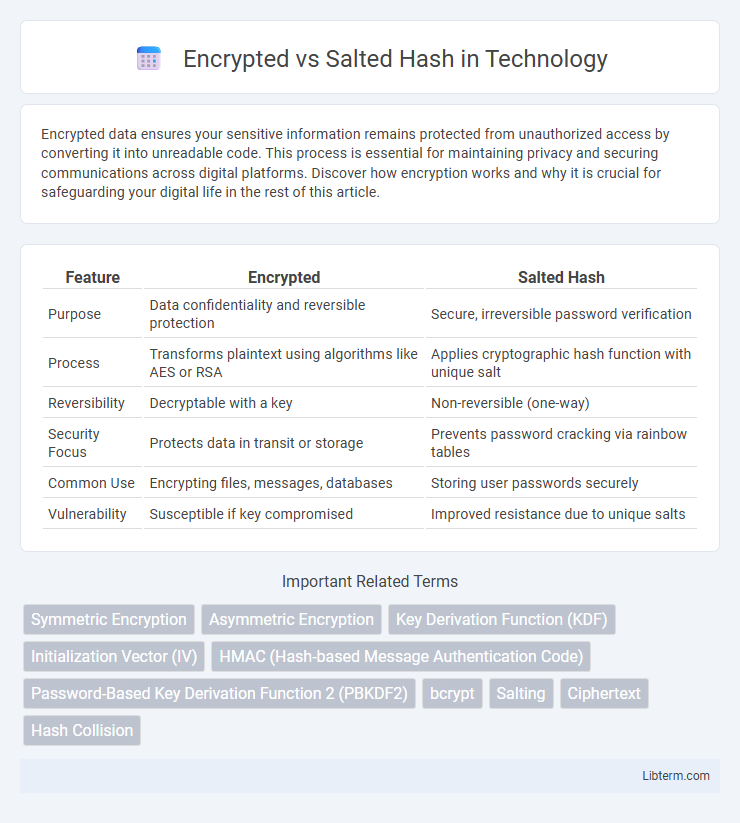
| Feature | Encrypted | Salted Hash |
|---|---|---|
| Purpose | Data confidentiality and reversible protection | Secure, irreversible password verification |
| Process | Transforms plaintext using algorithms like AES or RSA | Applies cryptographic hash function with unique salt |
| Reversibility | Decryptable with a key | Non-reversible (one-way) |
| Security Focus | Protects data in transit or storage | Prevents password cracking via rainbow tables |
| Common Use | Encrypting files, messages, databases | Storing user passwords securely |
| Vulnerability | Susceptible if key compromised | Improved resistance due to unique salts |
Introduction to Data Protection Techniques
Encrypted data transforms information into a secure format using algorithms and keys, ensuring confidentiality during transmission or storage. Salted hashing enhances password security by adding random data (salt) to the input before hashing, preventing attacks such as rainbow table lookups. Both techniques are essential in data protection, with encryption safeguarding data integrity and salted hashing strengthening authentication robustness.
What is Encryption?
Encryption transforms plaintext into ciphertext using algorithms and keys to prevent unauthorized access, ensuring data confidentiality. It differs from salted hashing, which irreversibly converts data into a fixed-length string combined with a unique salt to protect against precomputed attacks. Encryption allows for data decryption with the correct key, whereas salted hashes are designed to be one-way for secure password storage.
What is Hashing?
Hashing is a process that transforms input data into a fixed-length string of characters, which is typically a unique representation of the original data. Unlike encryption, hashing is a one-way function, meaning the original data cannot be easily recovered from the hash value. Salted hash adds random data, called a salt, to the input before hashing, enhancing security by protecting against rainbow table attacks and ensuring unique hash outputs even for identical inputs.
Understanding Salted Hashing
Salted hashing enhances security by adding a unique random value, called a salt, to a password before hashing, preventing attackers from using precomputed hash tables like rainbow tables. This technique ensures that identical passwords produce different hash outputs, complicating brute-force attacks and reducing the risk of password collisions. Salts must be stored securely alongside the hash to verify passwords during authentication while maintaining robust protection against common cryptographic attacks.
Key Differences: Encryption vs. Hashing
Encryption transforms plaintext into ciphertext using a reversible algorithm and a secret key, allowing data to be decrypted back to its original form. Hashing generates a fixed-length output from input data via a one-way function, making it computationally infeasible to reverse the hash back to the original data. Salting a hash involves adding a unique random value to the input before hashing to defend against rainbow table attacks and ensure hash uniqueness even for identical inputs.
Why Use Salted Hashes?
Salted hashes enhance password security by adding a unique random value (salt) to each password before hashing, preventing attackers from using precomputed rainbow tables to crack passwords efficiently. This method ensures that even identical passwords generate distinct hash outputs, significantly reducing the risk of hash collisions and brute force attacks. Salted hashing is essential for protecting sensitive user data and maintaining robust authentication systems against modern cyber threats.
Security Benefits and Use Cases
Encrypted data provides confidentiality by converting plaintext into ciphertext using algorithms like AES, ensuring secure communication and data storage. Salted hash enhances password security by adding a unique random value (salt) before hashing with functions like bcrypt or SHA-256, protecting against rainbow table and brute-force attacks. Encryption suits data transmission and confidentiality needs, while salted hashes are critical for secure password storage and authentication systems.
Vulnerabilities and Attack Vectors
Encrypted data can be vulnerable to attacks such as brute force or key-recovery if weak encryption algorithms or poor key management are used. Salted hashes defend against rainbow table attacks by adding unique random data (salt) before hashing, significantly increasing the difficulty for attackers attempting to reverse hashes or detect duplicate inputs. However, salted hashes remain susceptible to brute force and dictionary attacks if hashing algorithms are outdated or salts are improperly implemented.
Best Practices for Encryption and Salted Hashes
Best practices for encryption emphasize using strong, standardized algorithms such as AES with adequate key management and regular key rotation, ensuring data confidentiality. Salted hashes require the use of unique, cryptographically secure salts combined with hashing algorithms like bcrypt or Argon2 to protect against rainbow table attacks and enhance password security. Implementing proper entropy sources for salt generation and avoiding deprecated hash functions like MD5 or SHA-1 are critical for maintaining robust data protection.
Choosing the Right Approach for Your Data
Choosing between encrypted and salted hash depends on the data's sensitivity and intended use; encrypted data can be decrypted for recovery, while salted hashes are irreversible, ideal for securely storing passwords. Salting adds unique random values to each hash, preventing attacks from precomputed rainbow tables and enhancing security. For authentication systems, salted hashing is preferred; for sensitive data requiring decryption, strong encryption algorithms ensure confidentiality and integrity.
Encrypted Infographic
 libterm.com
libterm.com