A Trusted Execution Environment (TEE) provides a secure area within a device's main processor to protect sensitive data and code from unauthorized access or tampering. By isolating critical operations, TEEs ensure enhanced security for applications such as digital payments, biometric authentication, and confidential data processing. Discover how this technology fortifies your device and why it's essential for modern security in the full article.
Table of Comparison
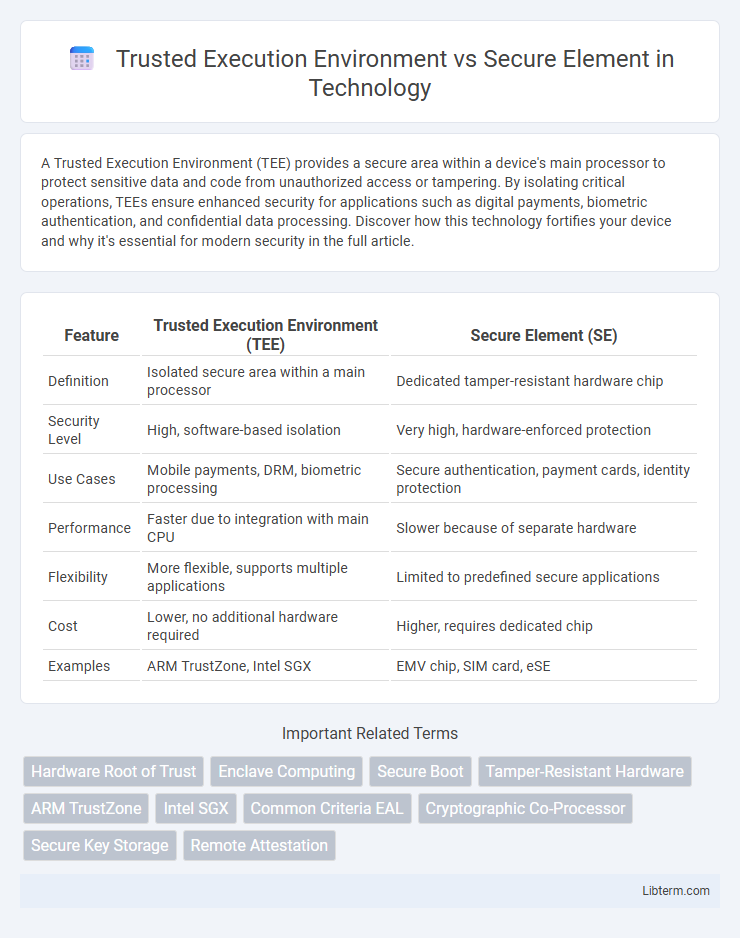
| Feature | Trusted Execution Environment (TEE) | Secure Element (SE) |
|---|---|---|
| Definition | Isolated secure area within a main processor | Dedicated tamper-resistant hardware chip |
| Security Level | High, software-based isolation | Very high, hardware-enforced protection |
| Use Cases | Mobile payments, DRM, biometric processing | Secure authentication, payment cards, identity protection |
| Performance | Faster due to integration with main CPU | Slower because of separate hardware |
| Flexibility | More flexible, supports multiple applications | Limited to predefined secure applications |
| Cost | Lower, no additional hardware required | Higher, requires dedicated chip |
| Examples | ARM TrustZone, Intel SGX | EMV chip, SIM card, eSE |
Introduction to Trusted Execution Environment (TEE) and Secure Element (SE)
Trusted Execution Environment (TEE) is a secure area within a main processor that runs code in an isolated environment, safeguarding sensitive data and operations from the regular operating system. Secure Element (SE) is a tamper-resistant hardware component designed to securely store cryptographic keys and execute trusted applications independently from the main processor. Both TEE and SE enhance device security by protecting confidential information and enabling secure transactions, but TEE leverages processor isolation while SE relies on dedicated hardware.
Core Concepts: What is a Trusted Execution Environment (TEE)?
A Trusted Execution Environment (TEE) is a secure area within a main processor that ensures sensitive data and code are isolated from the regular operating system, providing a protected environment for trusted applications. It uses hardware-based security features to enforce confidentiality and integrity, preventing unauthorized access even if the main OS is compromised. TEEs are often implemented using technologies like ARM TrustZone and provide a balanced approach to security and performance for mobile and embedded devices.
Understanding Secure Elements (SE): Definition and Types
Secure Elements (SE) are tamper-resistant hardware components designed to securely store cryptographic keys and execute sensitive operations within a protected environment. Types of SEs include embedded Secure Elements integrated into device chips, Universal Integrated Circuit Cards (UICC) used in SIM cards, and external Secure Elements found in smart cards or NFC devices. SEs provide a high level of security by isolating critical data from the main processor, making them essential for payment systems, identity verification, and digital rights management.
Key Differences Between TEE and SE Architectures
Trusted Execution Environment (TEE) is a secure area within the main processor that runs code in an isolated environment, providing security for sensitive data and operations without requiring separate hardware. Secure Element (SE) is a tamper-resistant hardware chip designed to securely store cryptographic keys and execute related security functions independently of the main processor. Key differences include TEE's reliance on software isolation within the main CPU versus SE's physical isolation, and SE's superior resistance to physical attacks compared to the software-based protection mechanisms of TEE.
Security Features: TEE vs Secure Element
Trusted Execution Environment (TEE) provides a secure area within the main processor, isolating sensitive operations and data from the rest of the system to protect against software attacks. Secure Element (SE) offers dedicated tamper-resistant hardware designed to securely store cryptographic keys and execute sensitive applications independently from the main device processor. While TEE protects runtime integrity and confidentiality through hardware and software isolation, Secure Element emphasizes physical security and robust resistance to physical attacks.
Application Use Cases: When to Use TEE or Secure Element
Trusted Execution Environment (TEE) is ideal for mobile payments, biometric authentication, and secure app execution where flexibility and integration within the device CPU are critical. Secure Element (SE) excels in scenarios requiring isolated hardware security, such as SIM-based authentication, payment cards, and access control systems, ensuring tamper-resistant storage of cryptographic keys. Choosing between TEE and SE depends on the required security level, performance constraints, and the application's need for isolation versus integration.
Performance Comparison: Speed, Scalability, and Resource Management
Trusted Execution Environments (TEEs) typically offer faster execution speeds compared to Secure Elements (SEs) due to their integration with the main processor, enabling low-latency access to system resources and efficient scalability across applications. Secure Elements, while highly secure with dedicated hardware, exhibit slower processing speeds and limited scalability because of their isolated and resource-constrained design. Resource management in TEEs benefits from shared system resources and dynamic allocation, whereas SEs maintain strict hardware isolation, resulting in higher security at the cost of reduced flexibility and performance efficiency.
Integration Challenges: TEE vs Secure Element Deployment
Trusted Execution Environment (TEE) deployment faces integration challenges due to compatibility issues with various operating systems and hardware architectures, often requiring close cooperation with device manufacturers and OS developers. Secure Element (SE) integration demands dedicated hardware design, leading to increased costs and complexity in embedding SE chips within devices, alongside ensuring secure communication between SE and the main processor. Balancing security requirements with seamless user experience remains a critical challenge for both TEE and SE deployment in mobile and IoT ecosystems.
Industry Standards and Compliance for TEE and SE
Trusted Execution Environment (TEE) complies with GlobalPlatform standards, ensuring interoperability and security certification such as Common Criteria EAL4+ or higher, widely adopted in mobile and IoT devices. Secure Element (SE) follows ISO/IEC 7816 and 14443 standards, with compliance to Payment Card Industry Data Security Standard (PCI-DSS) and FIPS 140-2 for hardware-based cryptographic protection. Both TEE and SE are critical for meeting regulatory requirements in sectors like finance, healthcare, and telecommunications, providing certified secure environments for sensitive data processing.
Choosing the Right Solution: TEE or Secure Element for Your Needs
Choosing between a Trusted Execution Environment (TEE) and a Secure Element (SE) depends on the specific security requirements and device constraints. TEEs provide isolated environments within the main processor for flexible, software-based security, ideal for applications needing dynamic protection and secure app execution. Secure Elements offer dedicated hardware security with tamper-resistant features, best suited for high-assurance use cases requiring robust key storage and cryptographic operations.
Trusted Execution Environment Infographic
 libterm.com
libterm.com