Replay attacks involve intercepting and retransmitting valid data to gain unauthorized access or disrupt communication systems. Protecting against these attacks requires robust encryption, secure authentication protocols, and time-stamping mechanisms to ensure message freshness. Explore this article to understand how to safeguard your systems from replay attacks effectively.
Table of Comparison
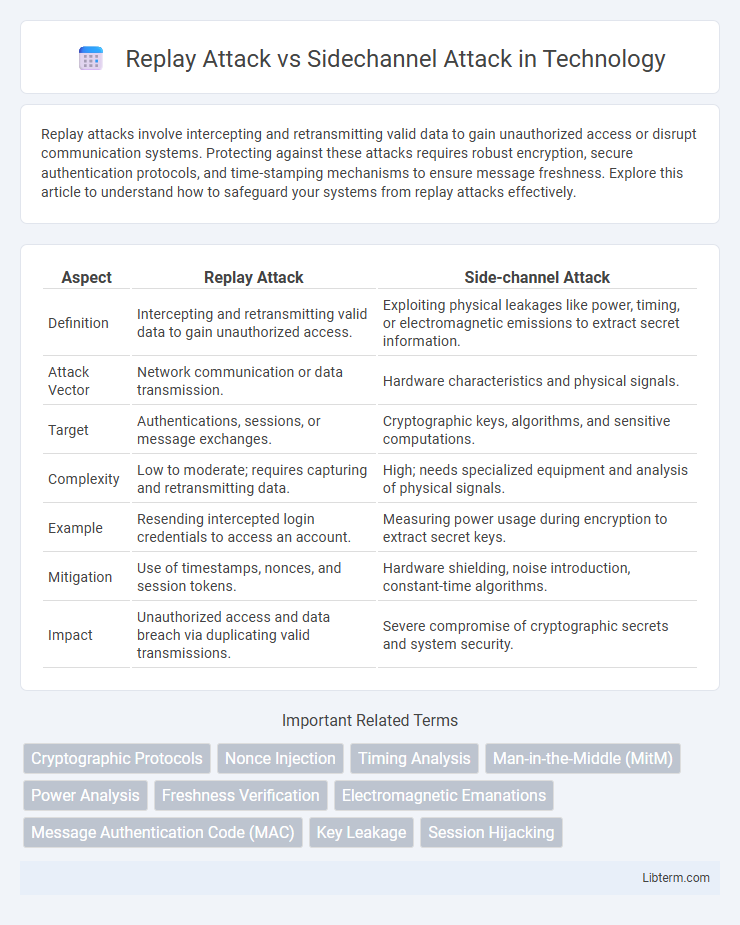
| Aspect | Replay Attack | Side-channel Attack |
|---|---|---|
| Definition | Intercepting and retransmitting valid data to gain unauthorized access. | Exploiting physical leakages like power, timing, or electromagnetic emissions to extract secret information. |
| Attack Vector | Network communication or data transmission. | Hardware characteristics and physical signals. |
| Target | Authentications, sessions, or message exchanges. | Cryptographic keys, algorithms, and sensitive computations. |
| Complexity | Low to moderate; requires capturing and retransmitting data. | High; needs specialized equipment and analysis of physical signals. |
| Example | Resending intercepted login credentials to access an account. | Measuring power usage during encryption to extract secret keys. |
| Mitigation | Use of timestamps, nonces, and session tokens. | Hardware shielding, noise introduction, constant-time algorithms. |
| Impact | Unauthorized access and data breach via duplicating valid transmissions. | Severe compromise of cryptographic secrets and system security. |
Understanding Replay Attacks
Replay attacks involve intercepting valid data transmissions and fraudulently retransmitting them to gain unauthorized access or privileges in a system. These attacks exploit the lack of freshness in authentication protocols, allowing attackers to reuse previously captured credentials or messages to mimic legitimate users. Effective countermeasures include implementing nonce values, timestamps, and challenge-response mechanisms to ensure each transaction remains unique and verifiable.
What is a Sidechannel Attack?
A Sidechannel Attack exploits physical or operational characteristics of a cryptographic system, such as timing information, power consumption, or electromagnetic leaks, to extract secret data. Unlike Replay Attacks that involve retransmitting valid data to deceive a system, Sidechannel Attacks target the indirect information emitted during cryptographic operations. These attacks require analyzing hardware behavior rather than intercepting or altering the transmitted messages.
Key Differences Between Replay and Sidechannel Attacks
Replay attacks target the repetition of valid data transmissions to gain unauthorized access or disrupt communication, exploiting protocol weaknesses without needing cryptographic key exposure. Sidechannel attacks extract sensitive information like cryptographic keys by analyzing physical leakages such as timing, power consumption, or electromagnetic emissions during device operation. The key difference lies in replay attacks manipulating data flow for unauthorized access, whereas sidechannel attacks focus on extracting secret information through physical observation.
How Replay Attacks Work
Replay attacks involve capturing valid data transmissions and retransmitting them to gain unauthorized access or duplicate a transaction, exploiting a lack of freshness or uniqueness in authentication protocols. These attacks work by intercepting session tokens, authentication credentials, or commands, then reusing them to trick the system into accepting the repeated data as legitimate. Unlike side-channel attacks that extract secret information from physical implementations, replay attacks exploit protocol vulnerabilities related to the reuse of valid communication data.
Mechanisms Behind Sidechannel Attacks
Replay attacks involve capturing and retransmitting valid data to gain unauthorized access, relying on intercepting communication. Sidechannel attacks exploit physical or implementation-based leaks, such as timing information, power consumption, or electromagnetic emissions, to extract sensitive data from cryptographic devices. Techniques like differential power analysis and electromagnetic analysis reveal secret keys by analyzing these indirect information channels without breaking underlying algorithms.
Common Targets of Replay Attacks
Replay attacks commonly target authentication systems, including login protocols, payment transactions, and secure communication channels, where intercepted data can be reused to gain unauthorized access. These attacks exploit vulnerabilities in session tokens, authentication credentials, and cryptographic handshakes, often impacting banking systems, IoT devices, and mobile networks. Unlike side-channel attacks that extract secrets through physical leakages, replay attacks strictly rely on capturing and retransmitting valid message sequences to deceive systems.
Typical Vectors for Sidechannel Attacks
Sidechannel attacks exploit physical leakages such as electromagnetic emissions, power consumption, or timing information from cryptographic devices to extract secret keys or sensitive data. Typical vectors for sidechannel attacks include monitoring power traces during encryption operations, analyzing electromagnetic radiation patterns emitted by hardware, and measuring timing variations caused by different computational paths. These attacks contrast with replay attacks, which involve capturing and retransmitting valid data to deceive a system without exploiting hardware vulnerabilities.
Techniques for Detecting Replay Attacks
Techniques for detecting replay attacks often involve analyzing timestamps, sequence numbers, or cryptographic nonces to identify duplicated or delayed messages. Network intrusion detection systems (NIDS) utilize pattern recognition and anomaly detection algorithms to spot repeated data packets indicative of replay attacks. Implementing challenge-response protocols and monitoring traffic for inconsistencies in expected communication patterns enhances the ability to detect and prevent replay attacks effectively.
Mitigation Strategies for Sidechannel Attacks
Mitigation strategies for sidechannel attacks primarily include implementing constant-time algorithms, deploying hardware-based countermeasures like noise generation and electromagnetic shielding, and utilizing masking and blinding techniques to obscure sensitive data. Robust encryption protocols combined with secure key management further enhance resistance to information leakage through timing, power consumption, or electromagnetic emissions. Regular security audits and sidechannel leakage testing are essential to identify vulnerabilities and ensure the effectiveness of these protective measures.
Comparing Security Implications: Replay vs Sidechannel Attacks
Replay attacks undermine system security by reusing valid data transmissions to gain unauthorized access, exploiting communication protocols without needing to break encryption. Side-channel attacks extract sensitive information by analyzing physical leakages like timing, power consumption, or electromagnetic emissions, often bypassing cryptographic strength. While replay attacks primarily target authentication processes, side-channel attacks threaten cryptographic key confidentiality, making them critical concerns in hardware and embedded security environments.
Replay Attack Infographic
 libterm.com
libterm.com