Static code analysis identifies potential bugs, security vulnerabilities, and code quality issues by examining source code without executing it. This method enhances software reliability and maintainability, saving time and costs in the development lifecycle. Explore the article to learn how static code analysis can improve your coding process and product quality.
Table of Comparison
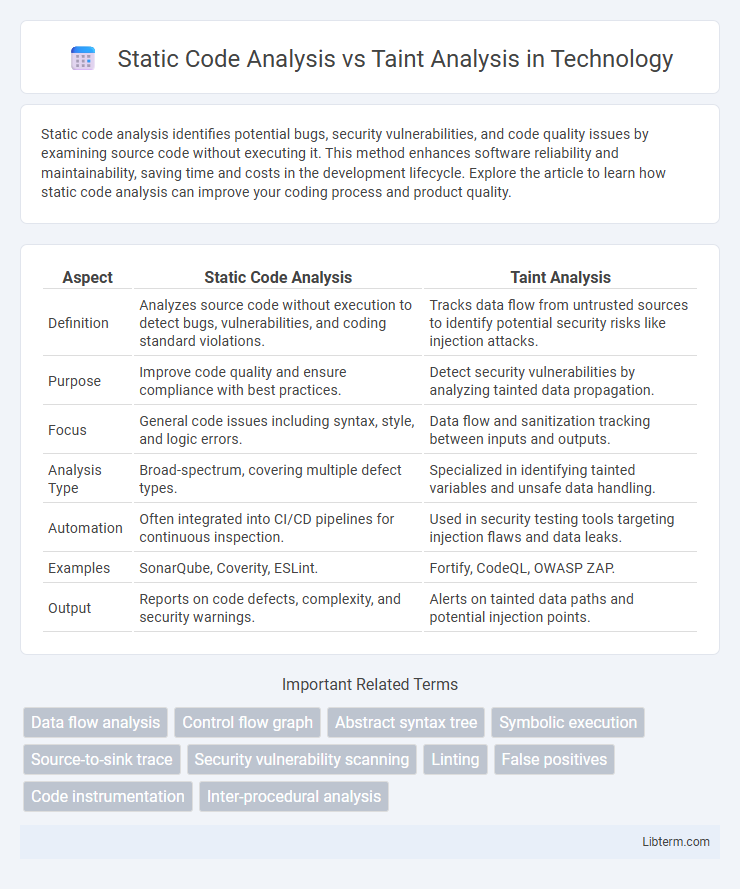
| Aspect | Static Code Analysis | Taint Analysis |
|---|---|---|
| Definition | Analyzes source code without execution to detect bugs, vulnerabilities, and coding standard violations. | Tracks data flow from untrusted sources to identify potential security risks like injection attacks. |
| Purpose | Improve code quality and ensure compliance with best practices. | Detect security vulnerabilities by analyzing tainted data propagation. |
| Focus | General code issues including syntax, style, and logic errors. | Data flow and sanitization tracking between inputs and outputs. |
| Analysis Type | Broad-spectrum, covering multiple defect types. | Specialized in identifying tainted variables and unsafe data handling. |
| Automation | Often integrated into CI/CD pipelines for continuous inspection. | Used in security testing tools targeting injection flaws and data leaks. |
| Examples | SonarQube, Coverity, ESLint. | Fortify, CodeQL, OWASP ZAP. |
| Output | Reports on code defects, complexity, and security warnings. | Alerts on tainted data paths and potential injection points. |
Introduction to Static Code Analysis
Static code analysis is a method used to examine source code for potential errors, vulnerabilities, and coding standard violations without executing the program. It employs automated tools that parse code to detect syntax issues, insecure coding practices, and structural flaws, enhancing software quality and security early in the development cycle. Unlike taint analysis, which tracks data flow to identify security risks, static code analysis provides a broad inspection of the entire codebase for defects and compliance.
What is Taint Analysis?
Taint analysis is a specialized form of static code analysis that tracks the flow of untrusted or potentially harmful data through a program to identify security vulnerabilities such as injection attacks and data leaks. It marks data originating from untrusted sources as "tainted" and monitors how this data propagates, ensuring it does not reach sensitive parts of the application without proper sanitization. This technique is crucial for detecting exploitable paths in software, especially in web applications and systems handling user input.
Key Differences Between Static Code Analysis and Taint Analysis
Static code analysis evaluates the entire codebase for potential errors, coding standard violations, and security vulnerabilities without executing the program, emphasizing overall code quality and safety. Taint analysis is a specialized subset of static analysis that tracks the flow of untrusted input (tainted data) through the program to identify potential injection points and security risks such as SQL injection or cross-site scripting (XSS). The key difference lies in scope and focus: static code analysis covers broad code correctness and security issues, while taint analysis specifically targets data flow vulnerabilities caused by untrusted inputs.
Core Principles of Static Code Analysis
Static code analysis examines source code without execution, identifying potential vulnerabilities by parsing syntactic structures and control flows. It relies on pattern matching, data flow analysis, and abstract interpretation to detect coding errors, security flaws, and adherence to standards before runtime. In contrast, taint analysis specifically tracks the flow of untrusted input through variables to prevent injection attacks, representing a focused subset within the broader static analysis framework.
Workflow of Taint Analysis
Taint analysis workflow starts by identifying taint sources, such as user inputs, and propagates taint marks through the program's data flows to detect vulnerabilities. It tracks how tainted data influences variables and functions, flagging potential security risks like SQL injection or cross-site scripting. The process concludes with sink detection, where unsafe usage of tainted data triggers alerts for security review.
Common Use Cases for Static Code Analysis
Static code analysis is extensively used for identifying security vulnerabilities, detecting code bugs, and enforcing coding standards across diverse programming languages in early development stages. It enables continuous integration pipelines to automatically flag potential defects and improve code quality before deployment. Common applications include vulnerability scanning in web applications, compliance verification in regulated industries, and optimization of legacy code maintenance.
Security Vulnerability Detection with Taint Analysis
Static code analysis identifies security vulnerabilities by examining source code without executing it, detecting issues such as buffer overflows and injection flaws. Taint analysis enhances vulnerability detection by tracking the flow of untrusted data through the program, exposing injection attacks and sensitive data leaks. By focusing on tainted data propagation, taint analysis provides more precise identification of exploitable weaknesses in software security.
Advantages and Limitations of Static Code Analysis
Static code analysis offers the advantage of early detection of bugs, security vulnerabilities, and compliance issues without executing the program, enhancing software quality and reducing debugging time. It can analyze all possible execution paths and is scalable to large codebases, making it efficient for continuous integration environments. However, static code analysis may produce false positives, lacks runtime context sensitivity, and often requires fine-tuning to balance precision and performance, limiting its effectiveness in detecting certain dynamic or data-flow-specific issues that taint analysis can reveal.
Challenges in Implementing Taint Analysis
Implementing taint analysis faces challenges such as managing high computational overhead and handling complex data flows across multiple program components accurately. False positives and false negatives frequently arise due to implicit data flows and dynamic language features, complicating precise taint tracking. Scalability issues also emerge when analyzing large codebases, requiring sophisticated heuristics and optimization techniques to maintain performance.
Choosing Between Static Code Analysis and Taint Analysis
Choosing between static code analysis and taint analysis depends on the specific security goals and codebase complexity. Static code analysis offers broad vulnerability detection by examining all code paths without execution, making it effective for identifying syntax errors, dead code, and potential bugs early in the development cycle. Taint analysis specializes in tracking the flow of untrusted input through the application to pinpoint injection vulnerabilities and data leaks, which is crucial when securing applications handling sensitive data or user input.
Static Code Analysis Infographic
 libterm.com
libterm.com