An encrypted container secures your sensitive data by using advanced encryption algorithms to prevent unauthorized access. This technology ensures that your files remain confidential even if the storage device is compromised. Explore the rest of this article to learn how encrypted containers can protect your information effectively.
Table of Comparison
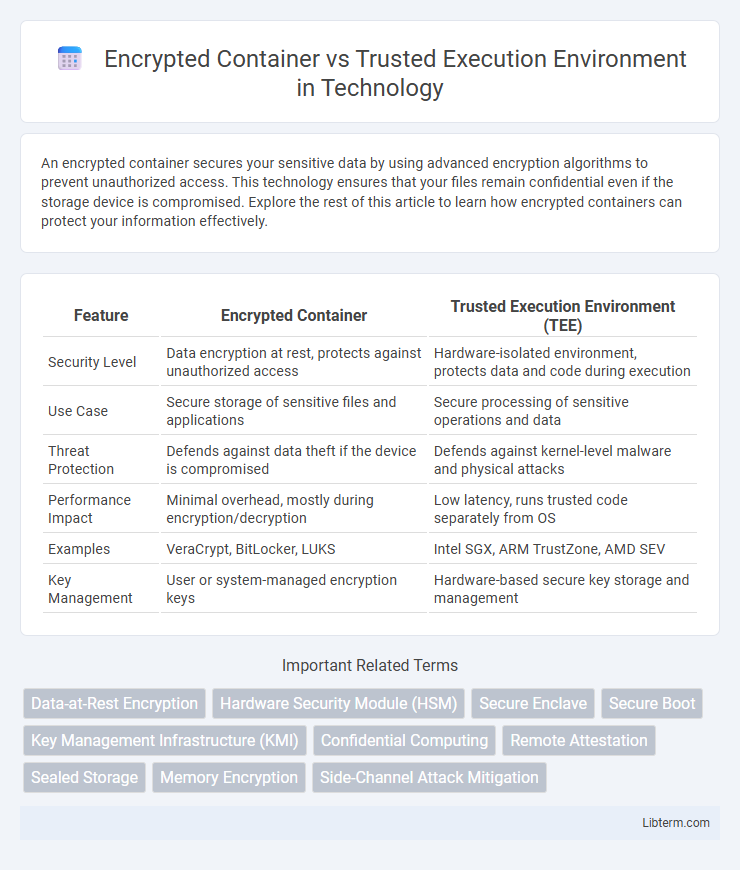
| Feature | Encrypted Container | Trusted Execution Environment (TEE) |
|---|---|---|
| Security Level | Data encryption at rest, protects against unauthorized access | Hardware-isolated environment, protects data and code during execution |
| Use Case | Secure storage of sensitive files and applications | Secure processing of sensitive operations and data |
| Threat Protection | Defends against data theft if the device is compromised | Defends against kernel-level malware and physical attacks |
| Performance Impact | Minimal overhead, mostly during encryption/decryption | Low latency, runs trusted code separately from OS |
| Examples | VeraCrypt, BitLocker, LUKS | Intel SGX, ARM TrustZone, AMD SEV |
| Key Management | User or system-managed encryption keys | Hardware-based secure key storage and management |
Introduction to Secure Data Storage Solutions
Encrypted containers provide secure data storage by encrypting files and folders within a virtual container, protecting data at rest with strong cryptographic algorithms such as AES-256. Trusted Execution Environments (TEEs) enhance data security by isolating and executing sensitive code and data in hardware-protected areas, mitigating risks from compromised operating systems. Both solutions address data confidentiality and integrity, with encrypted containers focusing on protecting stored data, while TEEs ensure secure processing and runtime protection within devices.
What is an Encrypted Container?
An encrypted container is a secure storage solution that uses strong cryptographic algorithms to protect data within a virtualized file or disk volume. It creates an isolated environment where sensitive information is encrypted and accessible only through authorized keys or credentials, ensuring confidentiality and integrity. Unlike Trusted Execution Environments (TEEs), encrypted containers focus primarily on data-at-rest protection rather than secure computation or runtime environment isolation.
Understanding Trusted Execution Environments (TEE)
Trusted Execution Environments (TEEs) provide a secure area within a processor, ensuring sensitive data and code are isolated from the main operating system and potential threats. Unlike encrypted containers that protect data at rest by encrypting files, TEEs enable secure processing by executing code in a hardened, tamper-resistant environment. This hardware-based isolation significantly enhances protection against malware and privileged attacks, making TEEs critical for trustworthy computation in modern devices.
Core Differences: Encrypted Container vs TEE
Encrypted containers protect data by encrypting files or storage volumes, ensuring confidentiality and access control at rest and during transmission. Trusted Execution Environments (TEE) create isolated, secure areas within a device's main processor to run sensitive code and processes, providing hardware-level attestation and protection against privileged software attacks. Unlike encrypted containers, TEEs offer runtime integrity and secure execution alongside data confidentiality, making them suitable for complex trust-sensitive applications.
Security Models and Threat Landscapes
Encrypted containers isolate sensitive data by encrypting files at rest, ensuring confidentiality even if storage is compromised, with security relying on robust key management and encryption algorithms. Trusted Execution Environments (TEEs) provide hardware-based isolation, protecting code and data during execution from privileged software attacks, including OS and hypervisor compromises. The threat landscape for encrypted containers centers on key leakage and unauthorized decryption, while TEEs face threats such as side-channel attacks and vulnerabilities in hardware firmware or microcode.
Performance and Resource Impact
Encrypted containers provide robust data protection by encrypting storage volumes, but they often introduce latency due to constant encryption and decryption processes, impacting I/O performance and increasing CPU usage. Trusted Execution Environments (TEEs) operate within isolated hardware-protected areas, offering secure execution with lower overhead on system resources and minimal impact on overall performance compared to encrypted containers. TEEs optimize sensitive computations by reducing data exposure while maintaining faster processing speeds, making them preferable for performance-critical applications.
Use Cases and Application Scenarios
Encrypted containers safeguard sensitive data by isolating it within a secure, encrypted file system, commonly used in cloud storage, secure backups, and data-at-rest protection for enterprises. Trusted Execution Environments (TEEs) provide a hardware-isolated environment for running code and processing data securely, making them ideal for secure key management, digital rights management (DRM), and confidential computing in edge devices and smartphones. Encrypted containers excel in protecting stored data from unauthorized access, while TEEs offer dynamic protection during data processing and execution, enabling secure multi-party computations and confidential machine learning applications.
Challenges and Limitations
Encrypted containers face challenges in key management and performance overhead during data encryption and decryption, limiting efficiency for large-scale applications. Trusted Execution Environments (TEEs) encounter limitations such as hardware dependency, potential vulnerabilities to side-channel attacks, and restricted memory size, which constrain their scalability and broader adoption. Both solutions struggle with seamless integration into existing infrastructures and require specialized expertise for secure implementation.
Industry Adoption and Real-World Examples
Encrypted containers offer widespread industry adoption for securing data-at-rest by encapsulating sensitive information within virtualized storage, prominently utilized in cloud storage services like AWS S3 and Microsoft Azure Blob Storage. Trusted Execution Environments (TEEs) provide hardware-isolated secure memory regions used by major technology companies such as Intel with SGX and ARM with TrustZone, enabling confidential computing in sectors like finance and healthcare to process sensitive workloads securely. Real-world implementations of TEEs include Intel's use in secure multi-party computation and ARM's deployment in mobile payment systems, contrasting with encrypted containers' prevalent role in securing cloud-native applications and database encryption.
Choosing the Right Solution: Key Considerations
Selecting between an encrypted container and a trusted execution environment requires evaluating data sensitivity, performance requirements, and threat models. Encrypted containers provide strong data-at-rest protection and portability, ideal for securing files on untrusted storage, while trusted execution environments offer hardware-based isolation that safeguards data and code during execution against sophisticated attacks. Key considerations include compliance needs, ease of deployment, and the specific security guarantees demanded by the application's operational context.
Encrypted Container Infographic
 libterm.com
libterm.com