Penetration testing evaluates your organization's security by simulating cyberattacks to identify vulnerabilities before malicious hackers exploit them. This proactive approach ensures robust defenses against potential breaches, safeguarding your sensitive data and network infrastructure. Discover how a thorough penetration test can enhance your cybersecurity strategy by exploring the rest of this article.
Table of Comparison
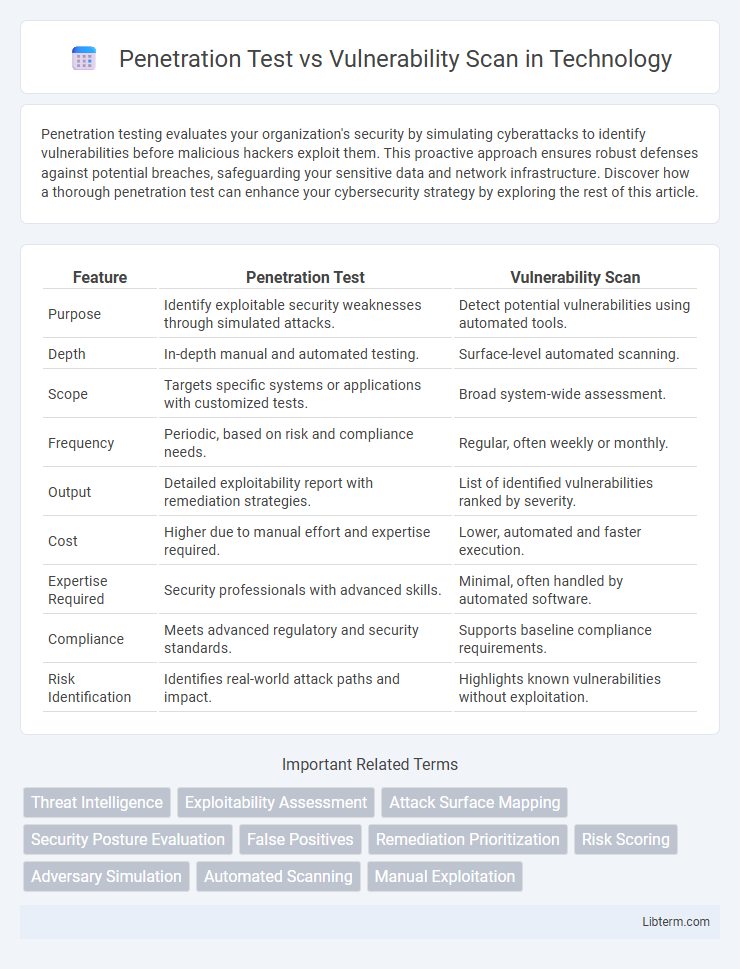
| Feature | Penetration Test | Vulnerability Scan |
|---|---|---|
| Purpose | Identify exploitable security weaknesses through simulated attacks. | Detect potential vulnerabilities using automated tools. |
| Depth | In-depth manual and automated testing. | Surface-level automated scanning. |
| Scope | Targets specific systems or applications with customized tests. | Broad system-wide assessment. |
| Frequency | Periodic, based on risk and compliance needs. | Regular, often weekly or monthly. |
| Output | Detailed exploitability report with remediation strategies. | List of identified vulnerabilities ranked by severity. |
| Cost | Higher due to manual effort and expertise required. | Lower, automated and faster execution. |
| Expertise Required | Security professionals with advanced skills. | Minimal, often handled by automated software. |
| Compliance | Meets advanced regulatory and security standards. | Supports baseline compliance requirements. |
| Risk Identification | Identifies real-world attack paths and impact. | Highlights known vulnerabilities without exploitation. |
Introduction to Penetration Testing and Vulnerability Scanning
Penetration testing involves simulating real-world cyber-attacks to identify exploitable security weaknesses within systems, networks, or applications, providing a deep assessment of organizational defenses. Vulnerability scanning utilizes automated tools to systematically detect known security flaws and misconfigurations, offering a broad overview of potential risks without exploiting them. Both methods are critical in comprehensive cybersecurity strategies, with penetration testing delivering actionable insights through hands-on probing and vulnerability scanning enabling continuous monitoring through automated discovery.
Defining Penetration Testing
Penetration testing involves simulating real-world cyberattacks to actively exploit security weaknesses in systems, networks, or applications, providing a comprehensive assessment of an organization's security posture. Unlike vulnerability scanning, which identifies potential security flaws through automated tools, penetration testing uses manual and automated techniques to validate vulnerabilities and determine their impact. This hands-on approach delivers actionable insights for enhancing defenses and reducing the risk of successful cyber intrusions.
Defining Vulnerability Scanning
Vulnerability scanning is an automated process that identifies and classifies security weaknesses in networks, systems, and applications by comparing known vulnerabilities against a specific environment. This method provides a broad assessment of potential risks, enabling organizations to prioritize remediation efforts based on severity and exploitability. Unlike penetration testing, vulnerability scanning does not exploit vulnerabilities but serves as an essential first step in the overall security assessment lifecycle.
Key Objectives: Penetration Test vs Vulnerability Scan
Penetration tests aim to simulate real-world cyberattacks to identify exploitable security weaknesses, validate the effectiveness of existing defenses, and assess the potential impact of breaches. Vulnerability scans focus on automatically detecting known security flaws and misconfigurations across systems and networks to provide a broad overview of potential risks. The key objective of penetration testing is to exploit vulnerabilities to measure actual risk, while vulnerability scanning prioritizes rapid identification and reporting of security issues for remediation.
Methodologies and Approaches
Penetration testing involves simulated cyberattacks using manual and automated techniques to exploit vulnerabilities, assessing security by demonstrating potential real-world impacts. Vulnerability scanning employs automated tools to identify known security weaknesses across systems without exploiting them, providing a broad overview of potential risks. While penetration tests provide in-depth, targeted analysis through active exploitation, vulnerability scans offer continuous, large-scale detection of security issues through signature-based assessments.
Depth and Scope of Assessments
Penetration tests provide an in-depth analysis by simulating real-world attacks to exploit vulnerabilities, revealing the potential impact and security weaknesses beyond surface-level issues. Vulnerability scans offer broader scope assessments by rapidly identifying known vulnerabilities across systems and networks but lack the detailed exploitation and context provided by penetration tests. Combining both methods enhances overall security posture by balancing comprehensive coverage with focused, actionable insights.
Tools Used in Penetration Testing and Vulnerability Scanning
Penetration testing utilizes tools like Metasploit, Burp Suite, and Kali Linux to simulate cyber attacks and exploit vulnerabilities in a controlled environment, providing a comprehensive security assessment. Vulnerability scanning relies on automated tools such as Nessus, Qualys, and OpenVAS to identify and report known security weaknesses across networks and systems without exploiting them. Both toolsets serve distinct purposes: penetration testing tools enable in-depth attack simulation and manual testing, while vulnerability scanners offer broad, automated detection of potential security gaps.
Benefits and Limitations
Penetration tests provide in-depth security assessments by simulating real-world attacks to identify exploitable vulnerabilities, offering detailed insights into an organization's defense gaps, while vulnerability scans quickly detect known security weaknesses across systems with extensive coverage. Penetration tests uncover complex, chained exploits and assess the effectiveness of security controls but are time-consuming and costly. Vulnerability scans offer faster, automated identification of common issues but may generate false positives and cannot assess the actual risk or exploitability of vulnerabilities.
Choosing the Right Solution for Your Organization
Selecting between a penetration test and a vulnerability scan depends on your organization's security goals and risk tolerance. Penetration testing provides in-depth, simulated cyberattacks to identify exploitable weaknesses, ideal for organizations seeking comprehensive threat assessments. Vulnerability scanning offers automated, regular checks for known flaws and is suitable for ongoing monitoring to maintain baseline security posture.
Conclusion: Penetration Test vs Vulnerability Scan
Penetration tests provide in-depth analysis by actively exploiting security weaknesses, offering a realistic assessment of potential threats and enabling tailored remediation strategies. Vulnerability scans deliver broad, automated identification of known security issues but often generate false positives and lack the contextual analysis penetration tests offer. Combining both approaches ensures comprehensive security coverage, balancing efficiency with detailed risk evaluation.
Penetration Test Infographic
 libterm.com
libterm.com