A firewall serves as a critical barrier that protects your network by monitoring and controlling incoming and outgoing traffic based on predetermined security rules. It helps prevent unauthorized access, cyberattacks, and data breaches, ensuring your sensitive information remains secure. Explore the rest of the article to understand how implementing a firewall can enhance your overall cybersecurity strategy.
Table of Comparison
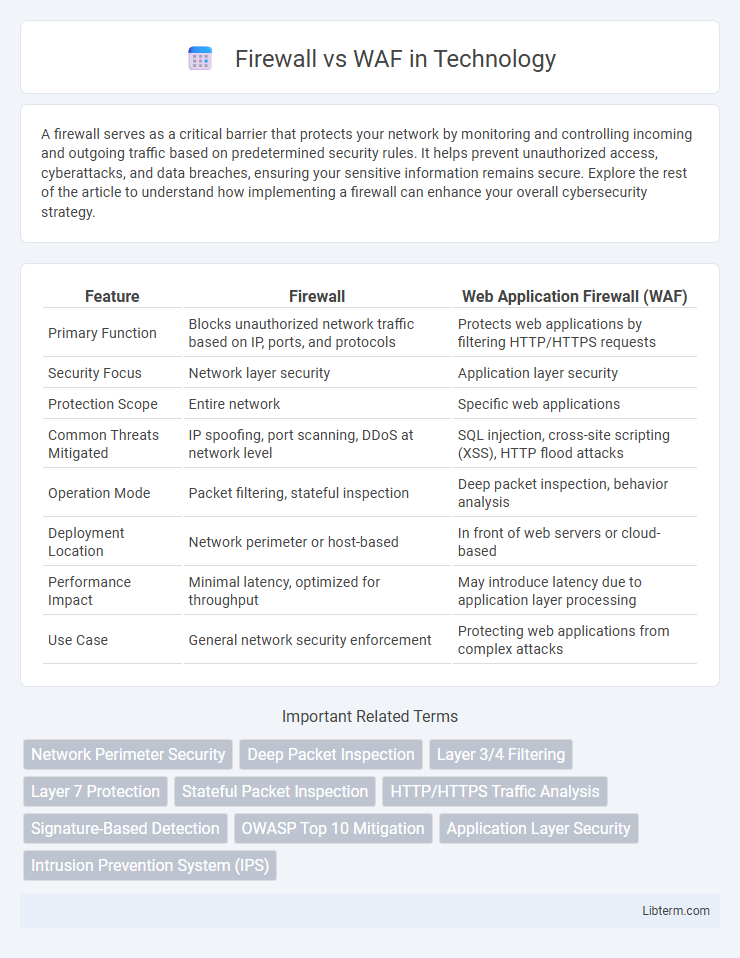
| Feature | Firewall | Web Application Firewall (WAF) |
|---|---|---|
| Primary Function | Blocks unauthorized network traffic based on IP, ports, and protocols | Protects web applications by filtering HTTP/HTTPS requests |
| Security Focus | Network layer security | Application layer security |
| Protection Scope | Entire network | Specific web applications |
| Common Threats Mitigated | IP spoofing, port scanning, DDoS at network level | SQL injection, cross-site scripting (XSS), HTTP flood attacks |
| Operation Mode | Packet filtering, stateful inspection | Deep packet inspection, behavior analysis |
| Deployment Location | Network perimeter or host-based | In front of web servers or cloud-based |
| Performance Impact | Minimal latency, optimized for throughput | May introduce latency due to application layer processing |
| Use Case | General network security enforcement | Protecting web applications from complex attacks |
Introduction to Firewalls and WAFs
Firewalls serve as network security systems that monitor and control incoming and outgoing traffic based on predetermined security rules, primarily protecting internal networks from unauthorized access. Web Application Firewalls (WAFs) specifically safeguard web applications by filtering, monitoring, and blocking HTTP traffic to and from a web service, targeting application-layer threats such as SQL injection and cross-site scripting. Both tools are crucial for comprehensive cyber defense, with firewalls focusing on broader network protection and WAFs concentrating on securing web applications against complex attacks.
Core Functions: Firewall vs WAF
Firewalls primarily enforce network security by monitoring and controlling incoming and outgoing traffic based on predefined security rules, protecting against unauthorized access and network threats. Web Application Firewalls (WAFs) specialize in filtering, monitoring, and blocking HTTP/HTTPS traffic to safeguard web applications from attacks such as SQL injection, cross-site scripting (XSS), and other application-layer threats. Firewalls operate at the network and transport layers, while WAFs provide granular security at the application layer, focusing on web application-specific vulnerabilities.
How Firewalls Protect Network Layers
Firewalls protect network layers by filtering incoming and outgoing traffic based on predefined security rules, blocking unauthorized access and preventing malicious data packets from entering the network. Operating primarily at the network and transport layers (Layers 3 and 4), firewalls analyze IP addresses, ports, and protocols to enforce access control policies. This layer-specific protection helps secure internal systems from external threats, ensuring data integrity and network availability.
WAFs and Application Layer Security
Web Application Firewalls (WAFs) are specialized security tools designed to protect web applications by filtering and monitoring HTTP traffic at the application layer, defending against threats such as SQL injection, cross-site scripting (XSS), and other code injection attacks. Unlike traditional firewalls that primarily guard network and transport layers, WAFs operate at Layer 7 of the OSI model, providing granular control over application-specific vulnerabilities and enhancing overall security posture for web applications. Effective WAF deployment reduces risk of data breaches and supports compliance with security standards by blocking malicious requests before they reach application servers.
Key Differences Between Firewalls and WAFs
Firewalls primarily protect networks by controlling incoming and outgoing traffic based on predefined security rules, while Web Application Firewalls (WAFs) specifically safeguard web applications by filtering and monitoring HTTP/HTTPS traffic to prevent attacks like SQL injection and cross-site scripting. Firewalls operate at the network and transport layers (OSI layers 3 and 4), whereas WAFs function at the application layer (layer 7), allowing them to inspect and block malicious payloads within web requests. The key difference lies in their scope and specificity: firewalls provide broad network perimeter security, while WAFs deliver targeted protection against web application vulnerabilities.
Deployment Scenarios: When to Use Which
Firewalls are essential for perimeter security, controlling incoming and outgoing traffic based on IP addresses and ports, making them ideal for protecting entire networks from unauthorized access. WAFs (Web Application Firewalls) specifically safeguard web applications by filtering and monitoring HTTP/HTTPS traffic to block attacks like SQL injection and cross-site scripting. Use firewalls for broad network-level security in traditional IT environments, while deploying WAFs when securing web applications exposed to the internet, especially in cloud or hybrid infrastructures.
Common Threats Blocked by Firewalls
Firewalls primarily block common threats such as unauthorized access attempts, malware infiltration, and network-based attacks like Distributed Denial of Service (DDoS). They filter incoming and outgoing traffic based on predefined security rules to prevent IP spoofing, port scanning, and protocol-based exploits. Unlike Web Application Firewalls (WAFs) that focus on application-layer attacks like SQL injection or cross-site scripting, firewalls provide a broader defense against network-level threats.
Attacks Mitigated by WAFs
WAFs (Web Application Firewalls) specifically mitigate attacks targeting web applications, such as SQL injection, cross-site scripting (XSS), and session hijacking by inspecting HTTP/HTTPS traffic for malicious payloads. Unlike traditional firewalls that primarily filter traffic based on IP addresses and ports, WAFs analyze application-layer protocols to detect and block Layer 7 attacks. This makes WAFs essential for protecting APIs, web forms, and other entry points vulnerable to sophisticated threats targeting application logic and data integrity.
Integration of Firewalls and WAFs for Maximum Security
Integrating firewalls and Web Application Firewalls (WAFs) enhances cybersecurity by combining network-level traffic filtering with application-layer protection, effectively mitigating a broader range of threats. Firewalls manage perimeter defense by blocking unauthorized access based on IP addresses and ports, while WAFs analyze HTTP/HTTPS traffic to detect and prevent attacks like SQL injection and cross-site scripting. Deploying both in a coordinated security architecture enables organizations to achieve comprehensive protection, reducing vulnerabilities and ensuring robust defense against sophisticated cyber threats.
Choosing the Right Solution for Your Needs
Choosing the right solution between a firewall and a Web Application Firewall (WAF) depends on the specific security requirements of your network and applications. Traditional firewalls protect networks by filtering traffic based on IP addresses and protocols, while WAFs provide specialized protection by filtering, monitoring, and blocking HTTP/S traffic to web applications, defending against SQL injection, cross-site scripting, and other web-based attacks. Organizations must assess factors like the complexity of their web applications, regulatory compliance needs, and the nature of cyber threats they face to determine whether a firewall, WAF, or a combination of both provides the most effective security posture.
Firewall Infographic
 libterm.com
libterm.com