Intrusion Detection Systems (IDS) are critical for identifying unauthorized access or attacks on your network by monitoring and analyzing traffic in real-time. These systems use signature-based and anomaly-based detection methods to promptly alert you to potential security breaches. Explore the rest of the article to understand how IDS can strengthen your cybersecurity defenses effectively.
Table of Comparison
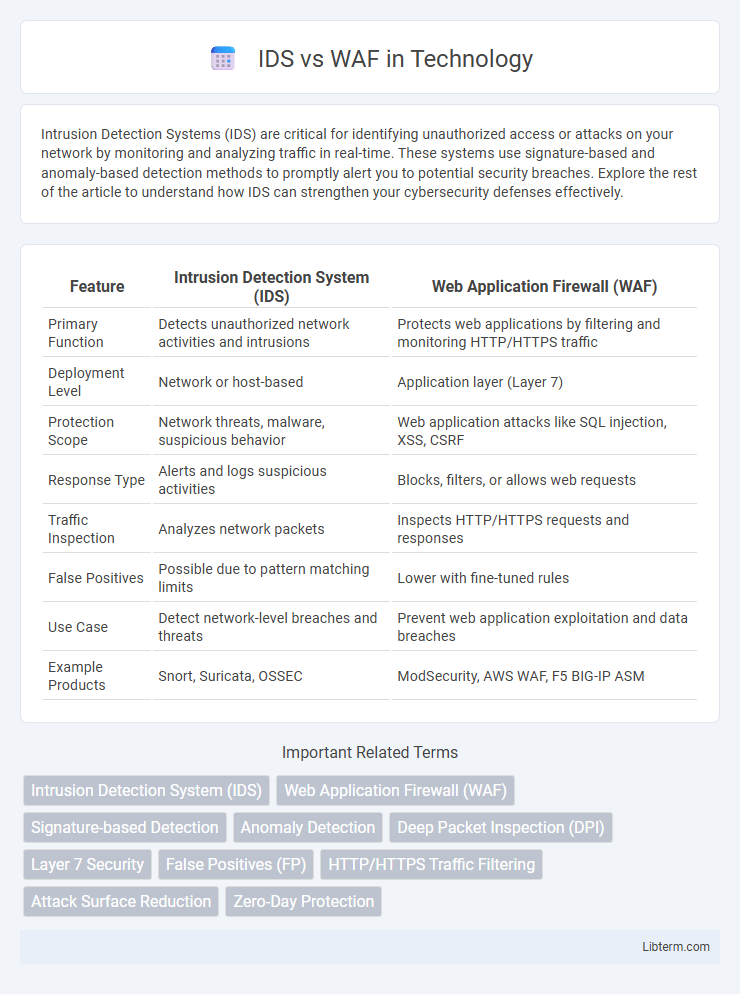
| Feature | Intrusion Detection System (IDS) | Web Application Firewall (WAF) |
|---|---|---|
| Primary Function | Detects unauthorized network activities and intrusions | Protects web applications by filtering and monitoring HTTP/HTTPS traffic |
| Deployment Level | Network or host-based | Application layer (Layer 7) |
| Protection Scope | Network threats, malware, suspicious behavior | Web application attacks like SQL injection, XSS, CSRF |
| Response Type | Alerts and logs suspicious activities | Blocks, filters, or allows web requests |
| Traffic Inspection | Analyzes network packets | Inspects HTTP/HTTPS requests and responses |
| False Positives | Possible due to pattern matching limits | Lower with fine-tuned rules |
| Use Case | Detect network-level breaches and threats | Prevent web application exploitation and data breaches |
| Example Products | Snort, Suricata, OSSEC | ModSecurity, AWS WAF, F5 BIG-IP ASM |
Understanding IDS: Definition and Key Functions
Intrusion Detection Systems (IDS) monitor network traffic and system activities for suspicious behavior, generating alerts upon detecting potential security threats. Key functions of IDS include identifying unauthorized access attempts, detecting malware or policy violations, and providing detailed logs for forensic analysis. Unlike Web Application Firewalls (WAF), IDS focuses broadly on network and host-based threats to enhance overall security posture.
What is a WAF? Core Features and Purpose
A Web Application Firewall (WAF) is a security solution designed to protect web applications by filtering, monitoring, and blocking malicious HTTP/S traffic based on predefined security rules. Core features of a WAF include protection against SQL injection, cross-site scripting (XSS), and other common web attacks, real-time traffic analysis, and customizable rule sets tailored to specific application needs. Its primary purpose is to safeguard web applications from vulnerabilities and ensure compliance with security standards while maintaining optimal performance and user experience.
IDS vs WAF: How They Work
Intrusion Detection Systems (IDS) monitor network traffic for suspicious activity and generate alerts without blocking the traffic, relying on signature-based or anomaly-based detection methods. Web Application Firewalls (WAF) specifically protect web applications by filtering, monitoring, and blocking malicious HTTP/HTTPS requests in real-time using predefined security rules and policies. IDS operates passively to detect threats across the network, while WAF actively intercepts and prevents attacks targeting web application vulnerabilities.
Detection Techniques: Anomaly vs. Signature-Based Approaches
Intrusion Detection Systems (IDS) primarily leverage signature-based detection, matching network traffic against known patterns of malicious behavior to identify threats quickly and with high accuracy. Web Application Firewalls (WAF) focus on anomaly-based detection, analyzing web traffic for irregularities that deviate from established baselines to protect against novel or sophisticated attacks. Combining signature-based IDS with anomaly-based WAF enhances overall security by providing comprehensive coverage against both known exploits and emerging threats.
Deployment Differences: Network vs. Application Layer
Intrusion Detection Systems (IDS) are primarily deployed at the network layer, analyzing traffic patterns and packet data to identify potential threats across entire networks. Web Application Firewalls (WAF) operate at the application layer, focusing specifically on HTTP/S traffic to protect web applications by filtering and monitoring requests. This fundamental deployment difference enables IDS to detect broader network threats while WAFs provide granular security against application-specific vulnerabilities such as SQL injection and cross-site scripting (XSS).
Types of Threats Prevented by IDS and WAF
IDS (Intrusion Detection Systems) primarily prevent threats such as unauthorized access attempts, malware infections, and network-based attacks by monitoring traffic for suspicious activity and alerting administrators in real time. WAF (Web Application Firewalls) specifically safeguard against web-based threats like SQL injection, cross-site scripting (XSS), and other application layer attacks by filtering and monitoring HTTP/HTTPS traffic to web applications. Both technologies address different security layers, with IDS focusing on network and host-based intrusions, while WAF concentrates on protecting web applications from malicious inputs.
Use Cases: When to Choose IDS or WAF
An IDS (Intrusion Detection System) is ideal for monitoring network traffic and identifying suspicious activities or potential threats within an internal network, making it suitable for organizations requiring comprehensive threat detection without direct intervention. A WAF (Web Application Firewall) specifically protects web applications by filtering and monitoring HTTP traffic, preventing attacks such as SQL injection and cross-site scripting, which is essential for businesses prioritizing web application security. Choose IDS for broad, network-wide intrusion detection and WAF when safeguarding web applications from known vulnerabilities and targeted attacks.
Pros and Cons: IDS vs. WAF
Intrusion Detection Systems (IDS) excel at identifying suspicious network activity and providing real-time alerts, enhancing threat visibility but often generate false positives and lack blocking capabilities. Web Application Firewalls (WAF) specialize in filtering and blocking HTTP attacks like SQL injection and cross-site scripting, improving application security but may impact performance and require extensive tuning. Choosing between IDS and WAF depends on whether network-level monitoring or application-layer protection is the primary security goal.
Integration with Other Security Tools
IDS seamlessly integrates with SIEM platforms and firewalls, enabling real-time threat detection and comprehensive network monitoring. WAFs work alongside API gateways and content delivery networks to protect web applications from attacks like SQL injection or cross-site scripting. Both tools enhance overall cybersecurity posture by complementing endpoint protection and threat intelligence systems.
Best Practices for Implementing IDS and WAF
Implementing Intrusion Detection Systems (IDS) and Web Application Firewalls (WAF) effectively requires continuous monitoring and regular updating of threat signatures to detect emerging vulnerabilities and attacks. IDS should be deployed with network segmentation to limit exposure while ensuring comprehensive traffic analysis, whereas WAFs must be configured with precise rule sets tailored to protect specific web applications without disrupting legitimate traffic. Integrating IDS and WAF with centralized security information and event management (SIEM) systems enhances real-time threat correlation and response, optimizing overall network and application security posture.
IDS Infographic
 libterm.com
libterm.com