OAuth is a secure authorization framework that enables third-party applications to access user data without sharing passwords. By delegating permissions, it enhances security and user control across various online services. Discover how OAuth can protect Your digital identity and simplify access management in the full article.
Table of Comparison
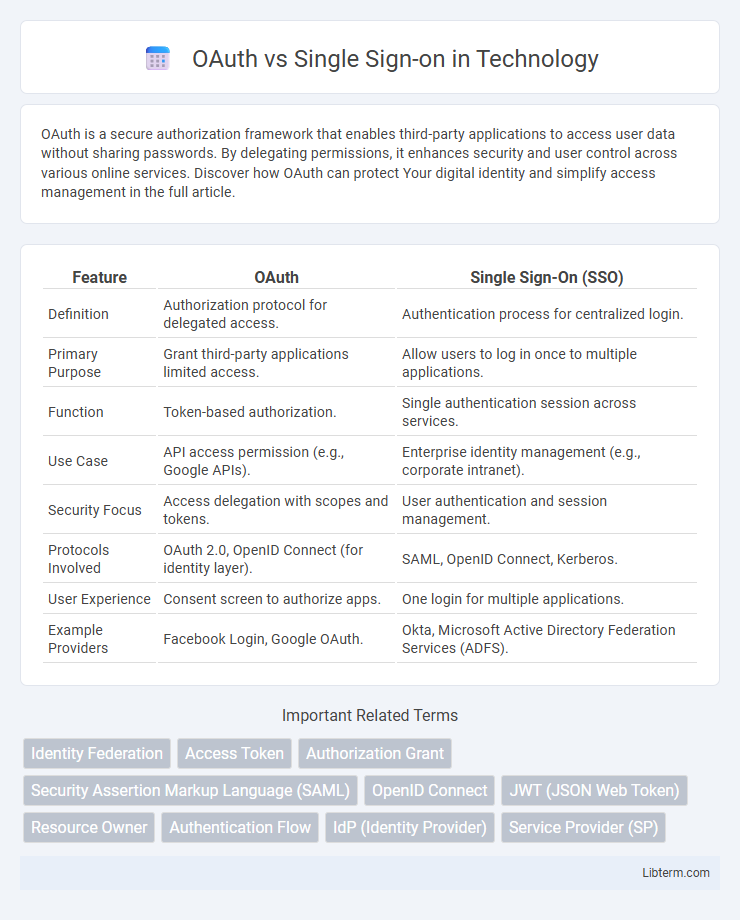
| Feature | OAuth | Single Sign-On (SSO) |
|---|---|---|
| Definition | Authorization protocol for delegated access. | Authentication process for centralized login. |
| Primary Purpose | Grant third-party applications limited access. | Allow users to log in once to multiple applications. |
| Function | Token-based authorization. | Single authentication session across services. |
| Use Case | API access permission (e.g., Google APIs). | Enterprise identity management (e.g., corporate intranet). |
| Security Focus | Access delegation with scopes and tokens. | User authentication and session management. |
| Protocols Involved | OAuth 2.0, OpenID Connect (for identity layer). | SAML, OpenID Connect, Kerberos. |
| User Experience | Consent screen to authorize apps. | One login for multiple applications. |
| Example Providers | Facebook Login, Google OAuth. | Okta, Microsoft Active Directory Federation Services (ADFS). |
Introduction to OAuth and Single Sign-On (SSO)
OAuth is an open standard protocol that allows third-party applications to access user data without exposing passwords, enabling secure authorization across different services. Single Sign-On (SSO) simplifies user authentication by enabling access to multiple applications with one set of login credentials, reducing password fatigue and improving user experience. Both OAuth and SSO enhance security and usability in identity management but serve distinct purposes: OAuth focuses on delegated access, while SSO centralizes authentication.
Understanding OAuth: Definition and Core Concepts
OAuth is an open standard for access delegation commonly used to grant websites or applications limited access to user information on other services without exposing credentials. It operates through token-based authorization, allowing third-party apps to act on behalf of users by obtaining an access token from the authorization server. Core concepts include resource owner, client, authorization server, resource server, and access token, which collectively enable secure, granular, and scoped access to protected resources.
What is Single Sign-On (SSO)? Key Principles Explained
Single Sign-On (SSO) is an authentication process that enables users to access multiple applications with a single set of login credentials, improving user experience and security. Key principles of SSO include centralized authentication, where a trusted identity provider verifies user credentials once, and federation, which allows seamless access across different domains or systems. By reducing credential fatigue and minimizing password-related attacks, SSO streamlines user management while maintaining robust access control.
Core Differences Between OAuth and SSO
OAuth is an authorization protocol designed to grant third-party applications limited access to a user's resources without exposing credentials. Single Sign-On (SSO) is an authentication process enabling users to access multiple applications with one set of login credentials, enhancing user convenience and security. The core difference lies in OAuth managing delegated access permissions while SSO focuses on verifying user identity across systems.
How OAuth Works: Authorization Flow Overview
OAuth operates through an authorization flow where the user grants a third-party application limited access to their resources without sharing credentials. The process begins with the user authenticating via an authorization server and authorizing the application to receive an access token. This access token then allows the application to access the user's resources on the resource server securely.
How SSO Functions: Seamless Authentication Process
Single Sign-On (SSO) functions by enabling users to authenticate once and gain access to multiple applications without repeatedly entering credentials, streamlining the user experience. It leverages a centralized identity provider to validate user identity and issue authentication tokens that are recognized across connected services. This seamless authentication process reduces password fatigue and enhances security by minimizing credential exposure across different platforms.
Use Cases: When to Use OAuth vs SSO
OAuth is ideal for authorizing third-party applications to access specific user data without sharing credentials, such as granting a payment app permission to access bank details. Single Sign-On (SSO) is best suited for enterprise environments where users need seamless access to multiple internal applications with one set of login credentials. Use OAuth for delegated access scenarios and SSO for centralized identity management and user convenience across multiple services.
Security Implications: OAuth versus SSO
OAuth primarily provides secure delegated access by issuing tokens to third-party applications without exposing user credentials, reducing the risk of password compromise. Single Sign-On (SSO) enhances security by centralizing authentication across multiple services, minimizing password fatigue and the chances of phishing attacks through a single trusted identity provider. However, if the SSO provider is compromised, it presents a single point of failure, making robust security measures and continuous monitoring essential.
Benefits and Drawbacks of OAuth and SSO
OAuth provides secure delegated access by allowing users to authorize third-party applications without sharing credentials, enhancing privacy and minimizing risk of password exposure. However, OAuth's complexity can lead to implementation errors and potential vulnerabilities if not properly managed. Single Sign-On (SSO) improves user convenience by enabling access to multiple applications with one set of credentials, reducing password fatigue and IT administrative overhead, but it presents a single point of failure risk and requires robust security policies to prevent widespread account compromise.
Choosing the Right Solution: OAuth or SSO for Your Application
Choosing between OAuth and Single Sign-On (SSO) depends on your application's authentication and authorization needs, where OAuth excels in delegated access and API authorization, granting limited access to third-party services without sharing credentials. Single Sign-On streamlines user experience by enabling access to multiple applications with one set of credentials, ideal for enterprise environments requiring centralized identity management. Evaluate factors like security requirements, user convenience, and integration complexity to select the optimal solution for seamless authentication and authorization workflows.
OAuth Infographic
 libterm.com
libterm.com